
doomerhunter
@doomeroutrun
Victor Poucheret
Bootstrapped a 7 figures business
Most Impactful Team @ H1-0131 - AWS / Amazon
Best collab @ H1-407 -Epic Games
Top 10 @ H1-702 Epic x TikTok
ID: 1156825647563587584
https://doomerhunter.fr/ 01-08-2019 07:15:01
308 Tweet
2,2K Takipçi
970 Takip Edilen




bugzilla.mozilla.org/show_bug.cgi?i… This is a big change for DOM Clobberers. Firefox Nightly no longer allows native document properties to be overwritten by elements with a name attr, e.g.: <img src=a name=currentScript> <script> alert(document.currentScript)// HTMLScriptElement </script>




I thought Golang had pretty secure defaults for parsing JSON, XML, YAML. But apparently there are some unexpected security footguns... Trail of Bits' Vasco Franco explores unexpected behaviors in Go's JSON, XML, and YAML parsers that can lead to security vulnerabilities,




Vibe hacking : Besides creating complex PoCs recently with agents, I've been using NotebookLM to increase my efficiency. Pretty crazy increase in performance on my side, ranging from : - Providing perfect context to my AI agents to generate PoCs (got a couple very severe bugs




Sadly, my talk on AI Hackbots was turned down at Unlock Your Brain, Harden Your System ! Where should I perform it now ? :D


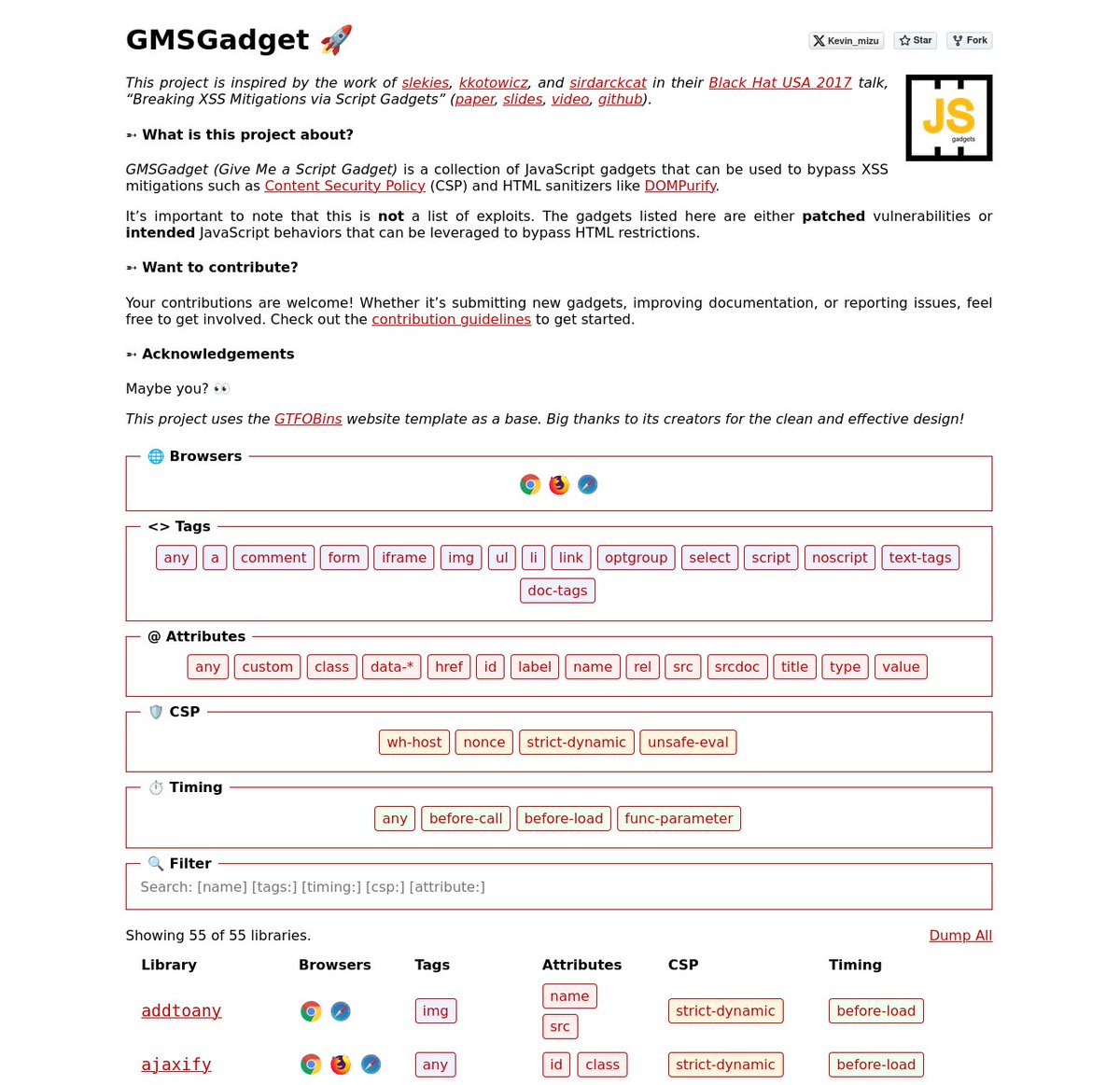
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4


🇫🇷🎙️Nouvel épisode du podcast Hack'n Speak accompagné de doomerhunter (Victor Poucheret) 🌺 On parle de son parcours, de bug bounty, d'évènement on site et d'IA ! 🥇 Bonne écoute à toutes et à tous 🎶 creators.spotify.com/pod/profile/ha…

We won o/ with doomerhunter (Victor Poucheret) and Snorlhax! #bugbounty #lhe #hackerone




