Alex Tereshkin
@alextereshkin
Poked firmware before it was cool. Security researcher @NVIDIA. Opinions expressed are my own.
ID: 3435793450
22-08-2015 17:56:46
131 Tweet
572 Takipçi
159 Takip Edilen

Proud from this research ;-) CC: Alex Tereshkin, Jared Candelaria, Max Bazaliy, igoo!, NVIDIA PSIRT nvidia.com/en-us/security…





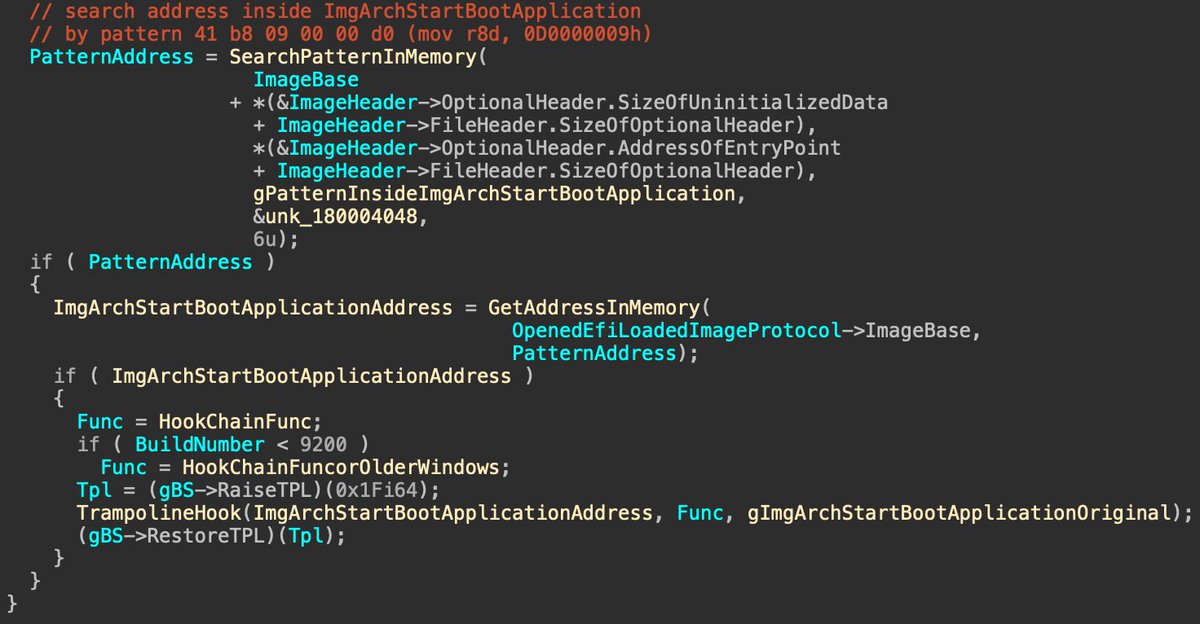
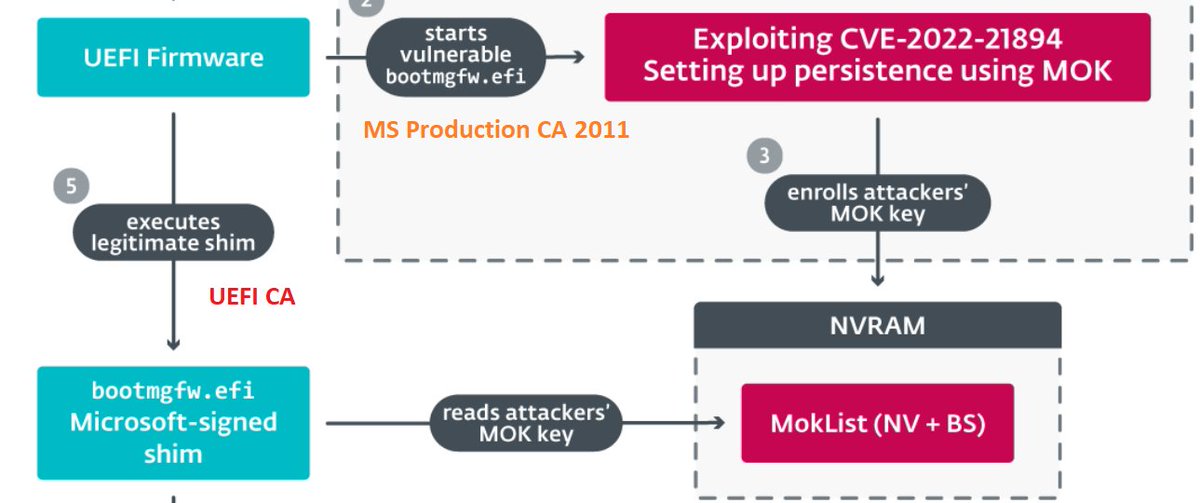
My 2c on the #BlackLotus UEFI bootkit (thanks, ESET Research): - "Exploitation Less Likely" is proven wrong, hope for a new DBX revocation list. - not trusting UEFI CA saves the day yet again. - having a single NV+BS variable as a gateway to booting whatever is a bad idea.



RISC-V (RISC-V International) Control Flow Integrity (CFI) is coming and I'm proud to be one of the contributors to this important security extension. Full spec is available here: github.com/riscv/riscv-cf…


Bug bounties are broken - the story of "i915" bug, ChromeOS + Intel bounty programs, and beyond Google VRP (Google Bug Hunters) Intel Security How the unspoken problems of bug bounties can be addressed? "Imbalance of Power" is a real problem and it should be changed. blog.pi3.com.pl/?p=931


Check out the abstract of our upcoming DC talk :) CC: Adam 'pi3' Zabrocki forum.defcon.org/node/245714

What is BMC? Should we care about BMC's security? How easy is it to hack it? You can find all the answers during our talk (CC Alex Tereshkin) at DEF CON at 3:30pm on Saturday ;-) Join us! forum.defcon.org/node/245714 CC: Max Bazaliy, igoo!, NVDA RISC-V FW dude #DEFCON31 #Defcon


🔬OSR Team keeps rocking! Alex Tereshkin and Adam 'pi3' Zabrocki keep digging into BMC and FW rabbit hole. 🔥The main caveat is that most of those discoveries are related to IBVs reference code and impact the entire industry. ⛓️One vendor fix != Industry ⛓️Supply Chain Security is hard!