0xW43L
@ghnimiwael
Cyber Threat Intelligence Researcher | #OSEP | #eWAPTx | #eJPT
An enthusiastic CyberSec Enthusiast who loves to explore, learn, break, and hack all thing !
ID: 793523100516225024
https://ghnimiwael.github.io/about/ 01-11-2016 18:40:24
80 Tweet
622 Followers
3,3K Following







As promised... this is Loki Command & Control! 🧙♂️🔮🪄 Thanks to Dylan Tran for his work done on the project and everyone else on the team for making this release happen! github.com/boku7/Loki






I've been poking at #Golang malware a bit lately and wrote up some tips/tricks that I use when analyzing Golang. Josh Stroschein | The Cyber Yeti and I just talked about this on his live stream too. Check it out here -> (The livestream replay is linked in the blog post) 🤓 securityliterate.com/go-big-or-go-h…






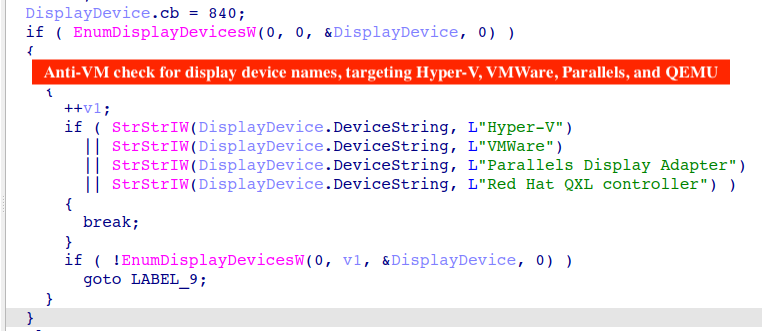

![hackyboiz (@hackyboiz) on Twitter photo [Research] Bypassing Windows Kernel Mitigations: Part0 - Deep Dive into KASLR Leaks Restriction
hackyboiz.github.io/2025/04/13/l0c…
In this post, we’ll take a closer look at the new KASLR-related mitigation introduced in Windows 11 and Windows Server 24H2, and explore a novel method for [Research] Bypassing Windows Kernel Mitigations: Part0 - Deep Dive into KASLR Leaks Restriction
hackyboiz.github.io/2025/04/13/l0c…
In this post, we’ll take a closer look at the new KASLR-related mitigation introduced in Windows 11 and Windows Server 24H2, and explore a novel method for](https://pbs.twimg.com/media/Goa1wLHWwAARmZs.jpg)