Fabian Thomas
@fth0mas
PhD Student @CISPA Helmholtz Center for Information Security.
ID: 1666886822629089282
08-06-2023 19:16:17
16 Tweet
97 Followers
36 Following

I'm thrilled to present our (@____salmon____, Michael Schwarz) work Hammulator, a parameterizable Rowhammer simulator, at #DRAMSec 2023 (June 17). Our simulator supports both syscall and full-system emulation, enabling comprehensive analysis of #Rowhammer attacks and mitigations.

I am happy to announce that Collide+Power, our new and generic software-based power side-channel technique, has been accepted at USENIX Security 2023 #usesec23. collidepower.com


Had the pleasure to present two papers at ESORICS today! The first analyzes the remaining attack surface of Meltdown 3a, the second (presented together with Fabian Thomas) shows that we can use Meltdown-US to leak the cache state of kernel structures on fully patched systems! 1/n


In "Reviving Meltdown 3a", we (Fabian Thomas, @____salmon____, Ruiyi Zhang, Michael Schwarz) analyzed 19 CPUs for the system registers that we can still leak using Meltdown 3a. Find the details and the tool to check your own CPU here: github.com/cispa/regcheck
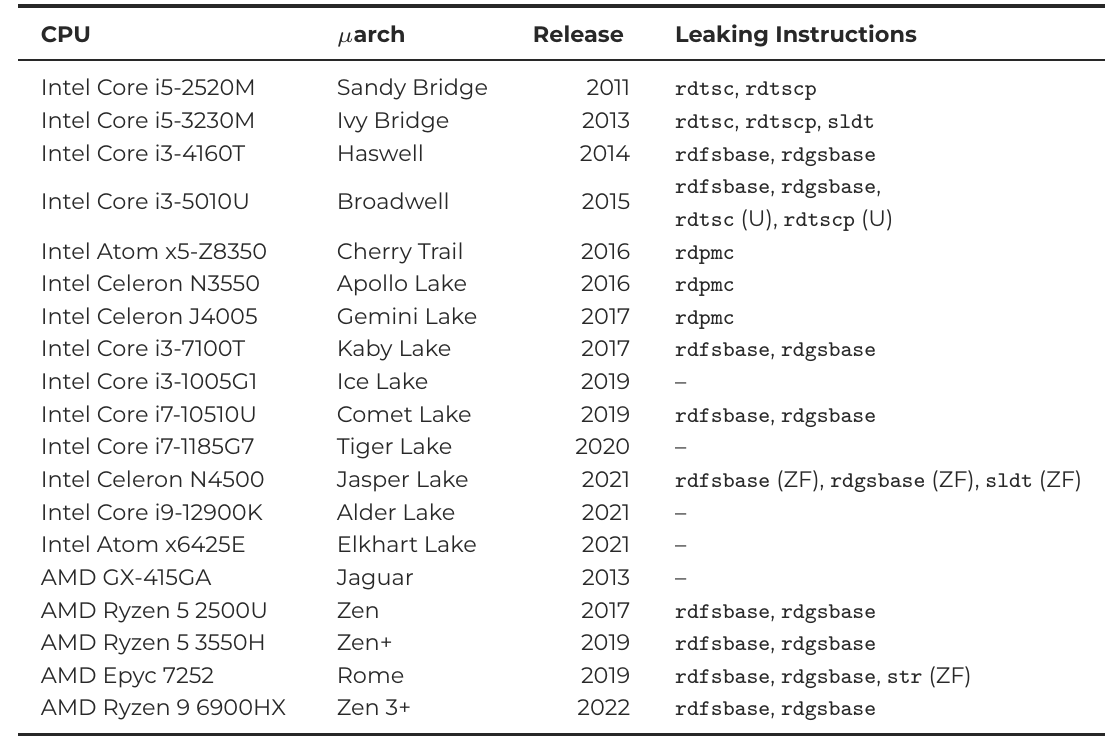

In "Indirect Meltdown", we (Fabian Thomas, @____salmon____ , Ruiyi Zhang, Michael Schwarz) show that transient-execution attacks can be turned into side-channel attacks (on fully patched machines)! If you want to know more or play around with our PoC: github.com/cispa/indirect…