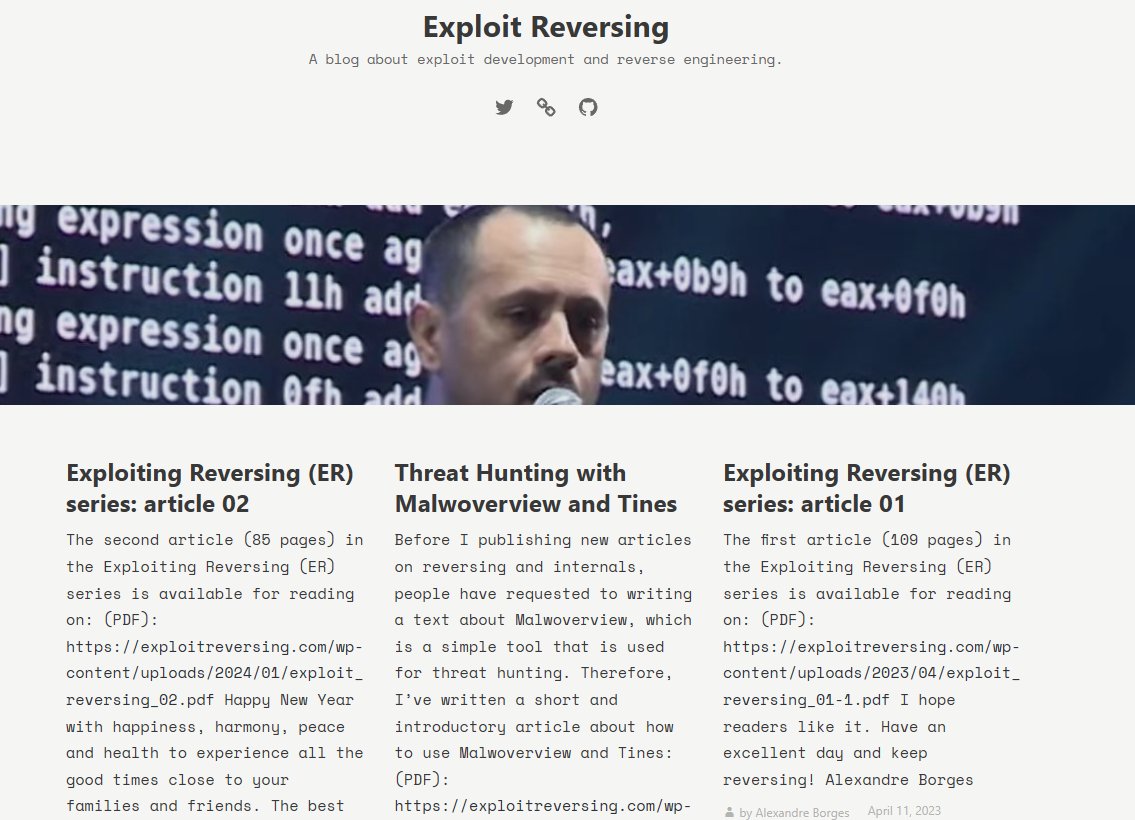
yed
@frdfzi
Interest in malware reversing, digital forensics, threat research and food 🍕 | KNR
ID:977452236178538496
http://Fareedfauzi.github.io 24-03-2018 07:49:08
3,8K Tweets
946 Followers
1,0K Following






My first blogpost and Analysis on a new #Ransomware called 'Donex'. Feel free to check it out🤘
dissect.ing/posts/donex/


Not sure if this account has enough visibility, but my current employer is looking for 2 more red team members to join us (cc:azrultech ).
Also looking for
+ Threat Intel/Hunting
+ Forensics
DM me your resume/CV
Please share to someone who you might think would be interested








register for a free workshop on malware analysis and development with me and Uriel Kosayev !
us06web.zoom.us/webinar/regist…

Fresh from Binarly REsearch team: We’ve completed an in-depth analysis of the #XZbackdoor , from initialization to the main hook enabling remote access.
Dive into our validated breakdown of techniques and backdoor functionalities, complete with proofs.
github.com/binarly-io/bin…