Jorge Gibbs
@v4ltzz
🇲🇽 Cybersecurity professional | SOC Analyst | CTF player | DFIR, Threat Intelligence | I like to think like an attacker | Opinions are my own
ID: 627089949
05-07-2012 03:23:43
1,1K Tweet
373 Followers
1,1K Following



















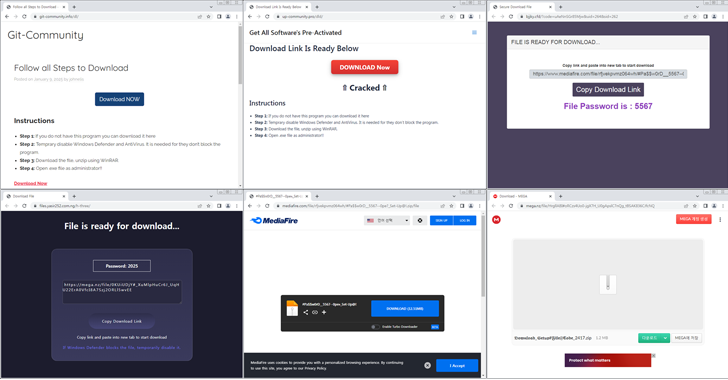
Don't trust the Host header in HTTP, firstly - check DNS 🧐 Here #ACRStealer mimics Bitdefender (indicates the official website in this POST request, but the real IP is different) 🦎 C2: 87.120.219[.]223 tria.ge/251014-qd8j9aa… virustotal.com/gui/file/83b63… #stealer
![Kseniia \n (@naumovax) on Twitter photo Don't trust the Host header in HTTP, firstly - check DNS 🧐
Here #ACRStealer mimics <a href="/Bitdefender/">Bitdefender</a> (indicates the official website in this POST request, but the real IP is different) 🦎
C2: 87.120.219[.]223
tria.ge/251014-qd8j9aa…
virustotal.com/gui/file/83b63…
#stealer Don't trust the Host header in HTTP, firstly - check DNS 🧐
Here #ACRStealer mimics <a href="/Bitdefender/">Bitdefender</a> (indicates the official website in this POST request, but the real IP is different) 🦎
C2: 87.120.219[.]223
tria.ge/251014-qd8j9aa…
virustotal.com/gui/file/83b63…
#stealer](https://pbs.twimg.com/media/G3OWWlQXgAAD9Cb.jpg)