Steven G
@processhacker
System Informer | Process Hacker | Windows Internals | Wrangler of Dingoes
ID: 266376391
15-03-2011 03:52:41
46 Tweet
413 Followers
16 Following

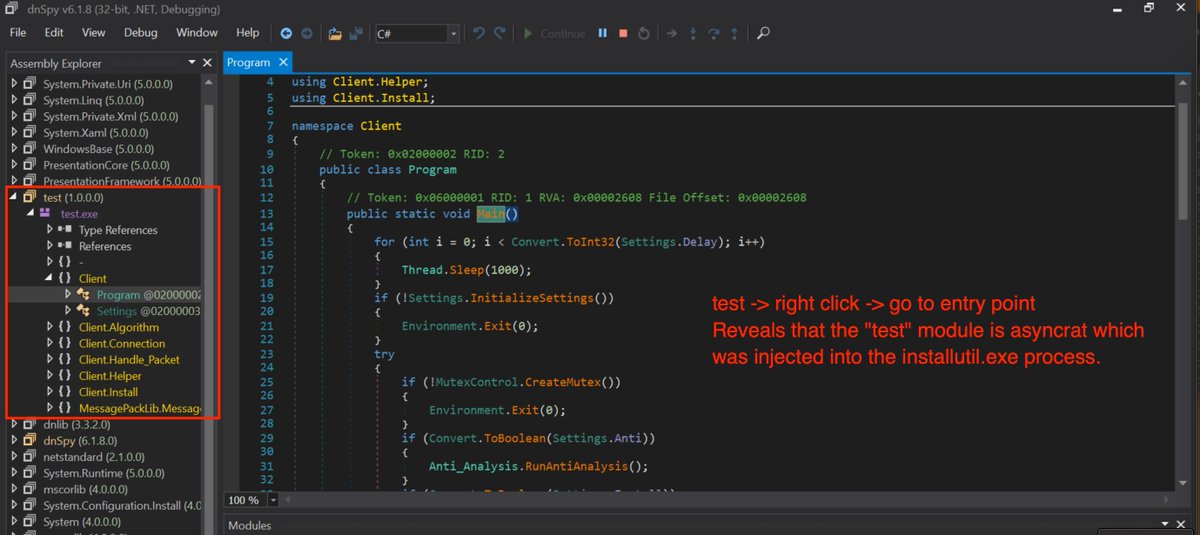
How to use Trend Micro's Rootkit Remover to Install a Rootkit, including a fun bonus discovery that Trend Micro is cheating WHQL certification. cc Microsoft Security d4stiny.github.io/How-to-use-Tre…


David Weston (DWIZZZLE) Yarden Shafir The driver doesn't have "arbitrary kernel RW" functionality, you can verify our source code... The bigger issue here is Microsoft Security and David Weston (DWIZZZLE) secretly banning a competitors product using a false pretext which is a federal crime.



Alex Ionescu David Weston (DWIZZZLE) And then we have Steven G that's trying its best to be complaint and MS bans them without any reason or help to solve the issues :(



I am ecstatic to announce that Winsider Seminars & Solutions, Inc. (the training company that Yarden Shafir and I co-own) has finalized the transfer of the venerable Process Hacker project into a new System Informer project (github.com/winsiderss/sys…). We are still migrating.. 1/2


In more System Informer news, Johnny Shaw and Alex Ionescu did amazing work mapping process connections over ALPC ports
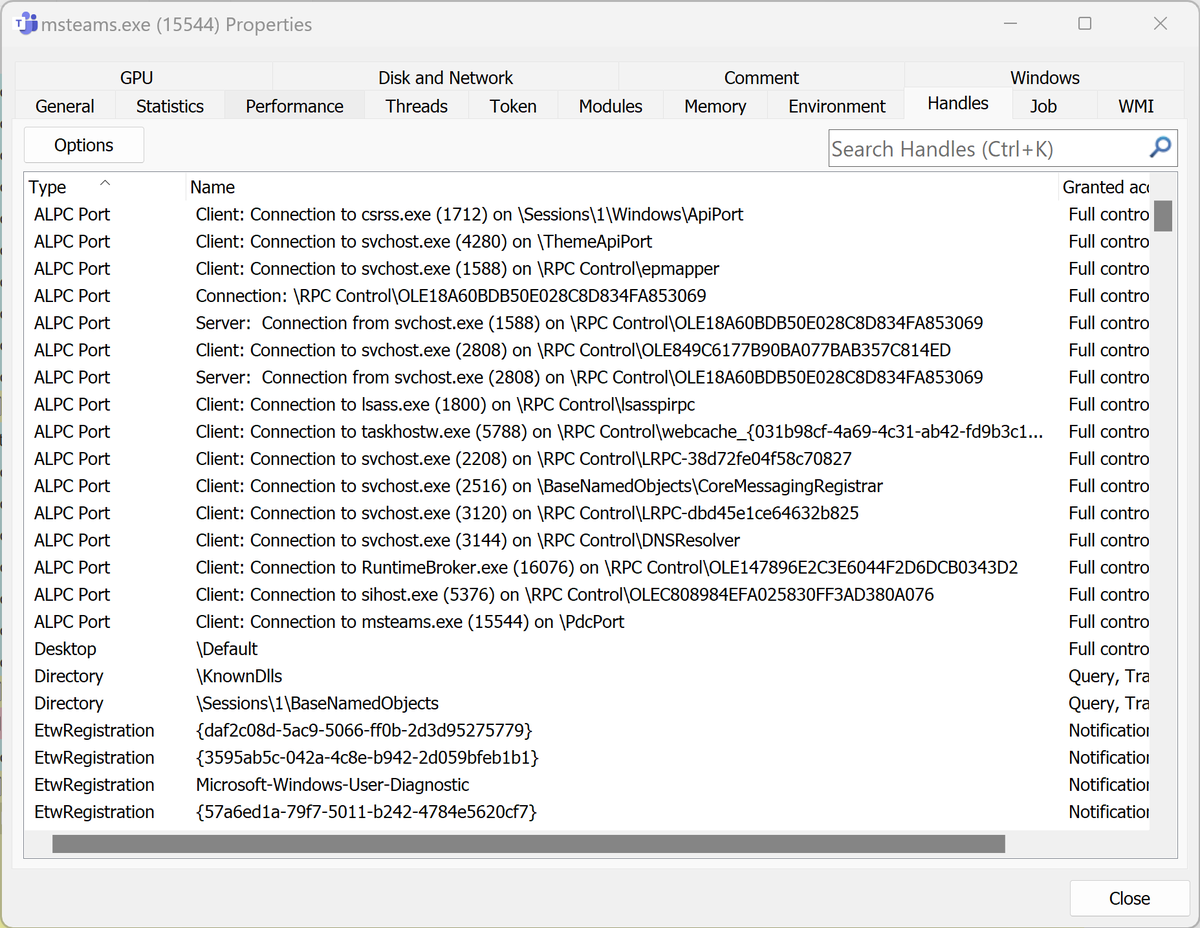




So I made a thing ☺️ Converted #phnt (Native API header files from the System Informer project) to #IDA TIL, IDC. To import "phnt" types and function definitions to IDA and help with Reverse Engineering. Hex-Rays SA Duncan Ogilvie 🍍 Introducing #IDA_PHNT_TYPES: github.com/Dump-GUY/IDA_P…



Better socket handle visibility coming soon to System Informer 🔥 When viewing a process handle table, SI will recognize files under \Device\Afd and retrieve information about their state, protocol, addresses, and more. Also works on Bluetooth and Hyper-V sockets 🤩
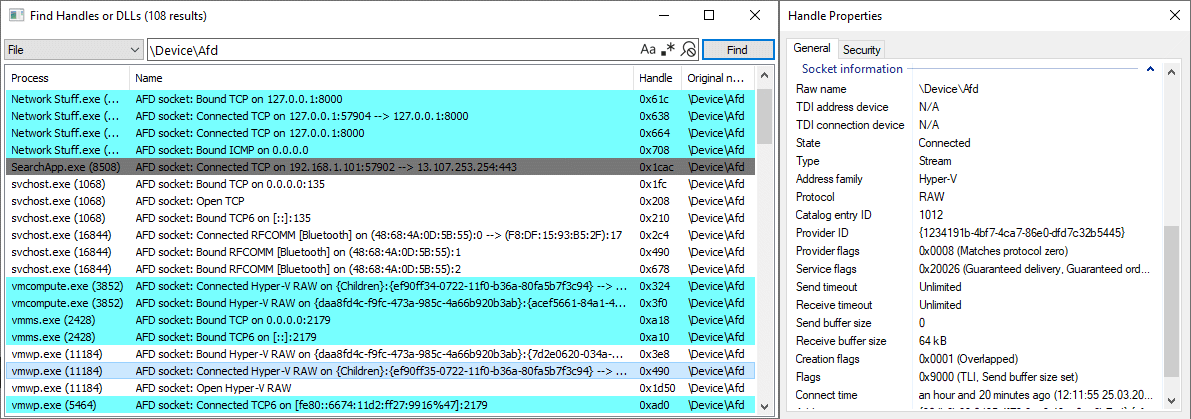

My new blog post 🥳 Improving AFD Socket Visibility for Windows Forensics & Troubleshooting It discusses the low-level API under Winsock (IOCTLs on \Device\Afd handles) and explores the workings of the new socket inspection feature in System Informer 🔥 huntandhackett.com/blog/improving…