
Fabio Pagani
@pagabuc
Vulnerability Research Lead @binarly_io. Prev: Postdoc @ucsantabarbara. Binary analysis, memory forensics et al. Captures flags with Shellphish and NOPS.
ID: 326371255
https://pagabuc.me/ 29-06-2011 20:20:25
1,1K Tweet
893 Followers
557 Following

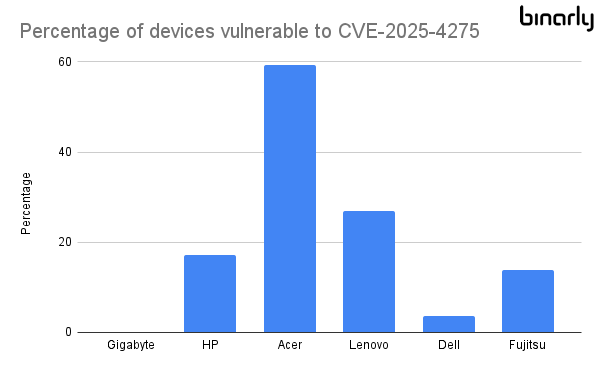
Nikolaj Schlej What’s alarming is how many devices are still vulnerable in-the-wild. Binarly telemetry data reveals the percentage of vulnerable system firmware update packages per vendor, and the numbers are concerning (🚨𝟯,𝟮𝟯𝟯 𝘂𝗻𝗶𝗾𝘂𝗲 𝘃𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗹𝗲 𝗱𝗲𝘃𝗶𝗰𝗲𝘀).

🔎From Hidden Semantics to Structured Insights✨ By combining static analysis techniques and tailored heuristic improvements, we've significantly enhanced the precision of type inference, enabling more effective vulnerability triage. lukas seidel Sam Thomas 👏 binarly.io/blog/type-infe…









Nvidia OSR (Alex Tereshkin, Adam 'pi3' Zabrocki) reveals high-impact Supermicro BMC vulnerabilities (CVE-2024-10237/38/39). Binarly REsearch documenting the details: 👻Ghost in the Controller: Abusing Supermicro BMC Firmware Verification. Read the full story: binarly.io/blog/ghost-in-…






Binarly is celebrating Phrack Zine 40th anniversary! 61st floor energy. Legends only 🎉










