
Joel GM
@joelgmsec
● Senior Red Team Cybersecurity Expert ● Ex-CTO @ Cyberguard
● SysAdmin +10 years ● Creator of AutoRDPwn: The Shadow Attack Framework
ID: 916599353355186176
https://darkbyte.net 07-10-2017 09:41:30
5,5K Tweet
2,2K Followers
2,2K Following


Following S3cur3Th1sSh1t's TROOPERS talk and release of BitlockMove, we're releasing our internal DCOMRunAs PoC made by @SAERXCIT last year. It uses a similar technique with a few differences, such as DLL hijacking to avoid registry modification. github.com/AlmondOffSec/D…




Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (Aurélien Chalot), including instructions for reproducing the test environment yourself. (link below)
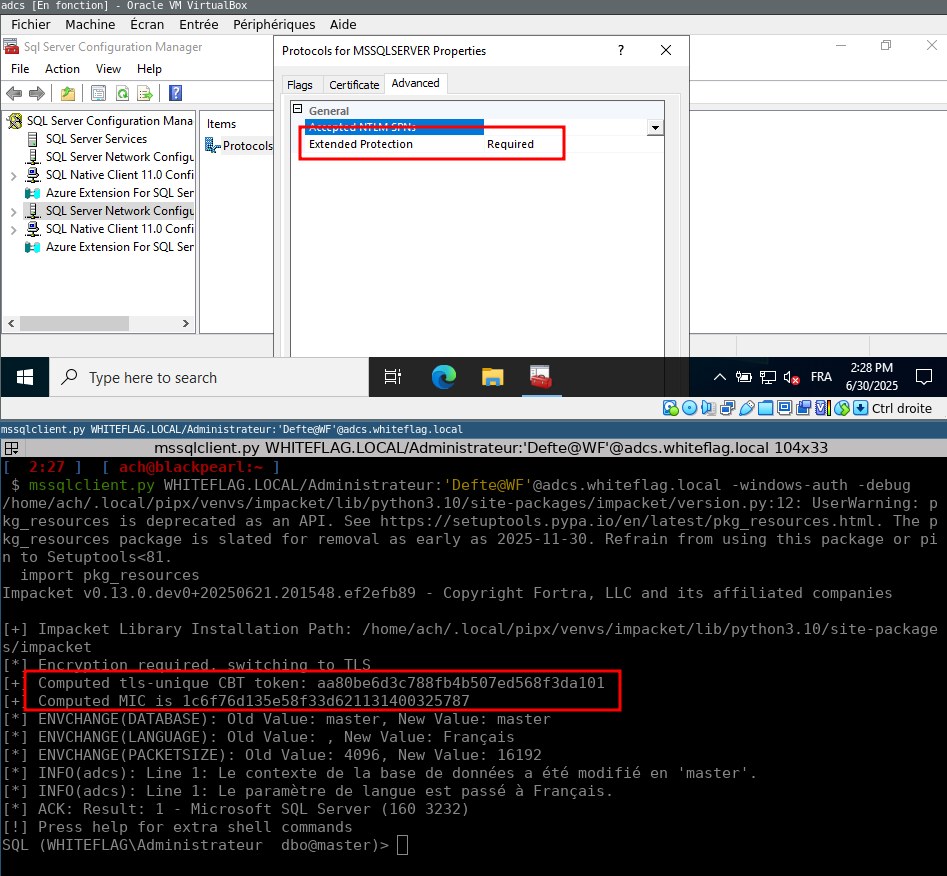

The code is here. As always, "Not tested in prod, use at your own risk". All credit goes to Yuval Gordon, sn🥶vvcr💥sh and fulc2um. gist.github.com/ThePirateWhoSm… 🌻








Hoy a las 20:00 (hora España) estaré hablando sobre Windows, suplantación de usuarios y movimientos laterales en el canal de Alberto J Garcia YouTube: HablemosCyber










