
Dominic Chell 👻
@domchell
Just your friendly neighbourhood red teamer @MDSecLabs | Creator of /r/redteamsec | https://t.co/3k3EBAZqGd | https://t.co/KwO2OwDOkl
ID:20015415
https://www.mdsec.co.uk 04-02-2009 00:02:39
14,3K Tweets
15,7K Followers
532 Following
Follow People

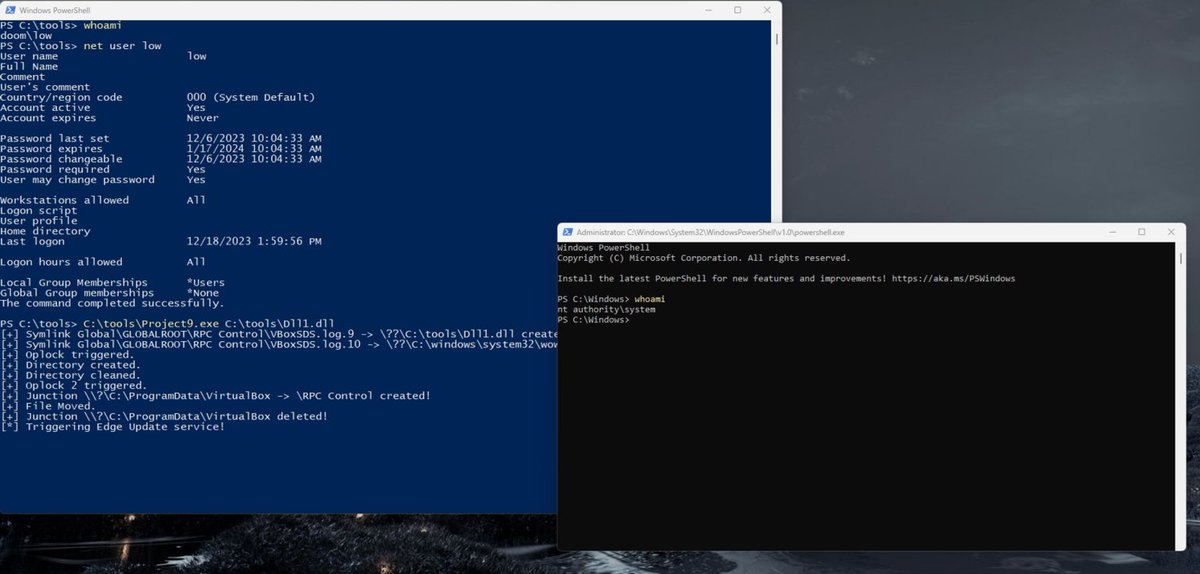
New post on the blog… Exploiting CVE-2024-21111 : Local Privilege Escalation in Oracle VirtualBox by Filip Dragovic mdsec.co.uk/2024/04/cve-20…














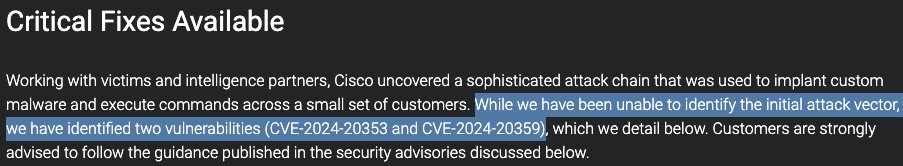
Full Rapid7 analysis of PAN-OS CVE-2024-3400 now available from Stephen Fewer and our stellar new research teammate ryan emmons! Spoiler: It's a two-vuln exploit chain. attackerkb.com/topics/SSTk336…

Our threat brief on Operation MidnightEclipse, tracking exploitation of #CVE20243400 , now has new indicators as well as lists of commands seen in exploitation attempts: bit.ly/43YOECb



Malicious activity tracked under the campaign #OperationMidnightEclipse is targeting CVE-2024-3400, which exploits a vulnerability in certain versions of PAN-OS software. This threat brief covers mitigations and product protections: bit.ly/3vPUngM













![blackorbird (@blackorbird) on Twitter photo 2024-04-13 04:00:30 Zero-Day Exploitation of Unauthenticated Remote Code Execution Vulnerability in GlobalProtect (CVE-2024-3400) 172.233.228[.]93 volexity.com/blog/2024/04/1… Zero-Day Exploitation of Unauthenticated Remote Code Execution Vulnerability in GlobalProtect (CVE-2024-3400) 172.233.228[.]93 volexity.com/blog/2024/04/1…](https://pbs.twimg.com/media/GLBEBmabYAApL4Y.jpg)