
crazyman_army
@crazymanarmy
CTFer / APT hunter / RedTeam / BlueTeam
the member of @r3kapig
the leader of @ShadowChasing1
CVE-2022-30190
find job opportunities
opinions are own not group
ID: 1427918131322789898
https://crazymanarmy.github.io/ 18-08-2021 09:00:01
4,4K Tweet
5,5K Followers
2,2K Following








I'm pumped to announce the release of Misconfiguration Manager, a knowledge base and how-to for both offensive and defensive SCCM attack path management, that Duane Michael, Garrett Foster, and I have been working on! Check it out and let us know what you think! posts.specterops.io/misconfigurati…


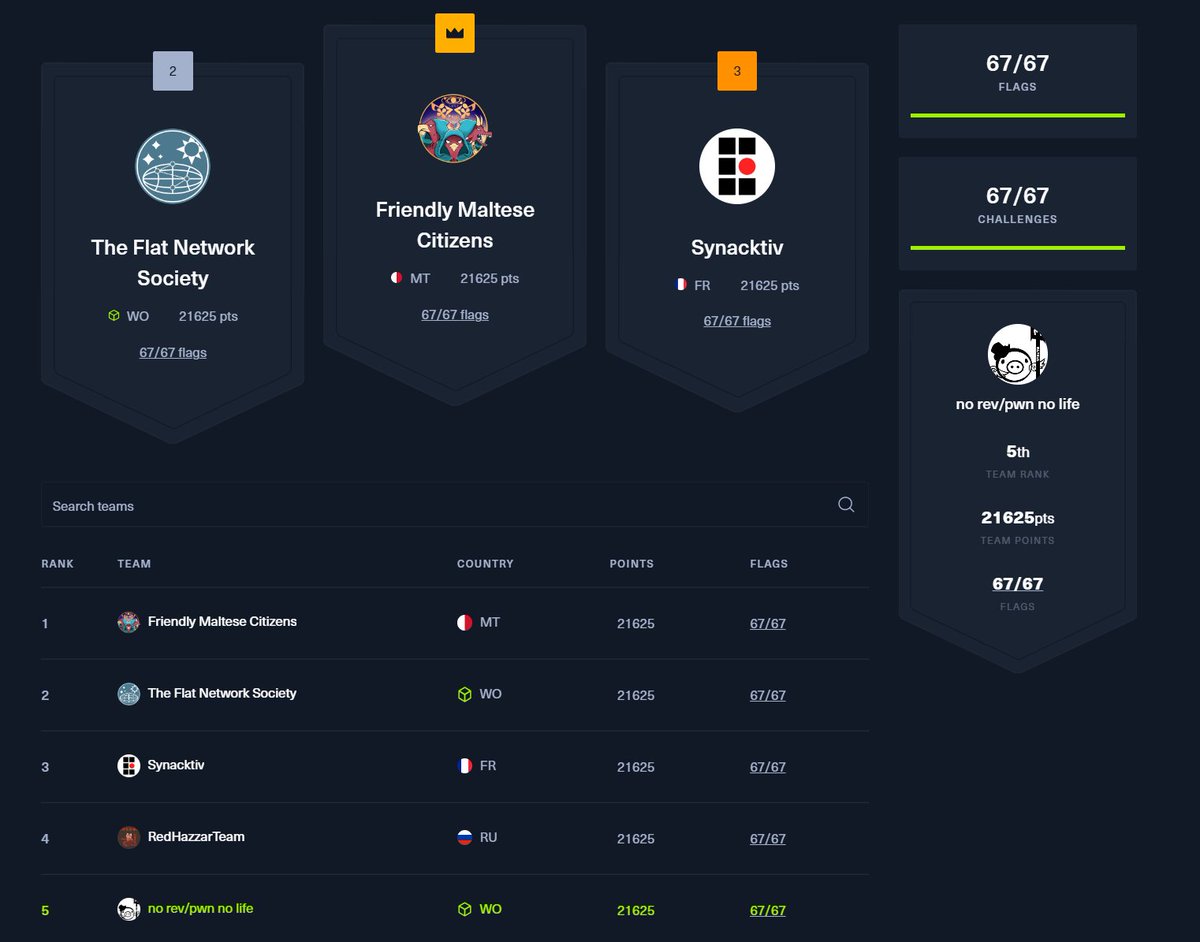
After two days of hard work we finally completed the all challenge of Cyber Apocalypse 2024: Hacker Royale challenge and came in 5th place! And congrats to Friendly Maltese Citizens 1st place 🥇, Flat Network Society 2nd place 🥈, Synacktiv 3rd place 🥉, RedHazzarTeam 4th place.



🚀 picoCTF 2024 Has Officially Started! 🎉 The wait is over – picoCTF 2024 is underway! Carnegie Mellon University TCM Security crl_official CyLabAfrica @CyLab picoCTF.org





![xvonfers (@xvonfers) on Twitter photo (CVE-2024-1694???)[$5000][1505686][Updater]EoP in GoogleUpdate with Windows(can be exploited by an attacker to gain SYSTEM privileges on a PC with Google Chrome).
issues.chromium.org/issues/40946325 (CVE-2024-1694???)[$5000][1505686][Updater]EoP in GoogleUpdate with Windows(can be exploited by an attacker to gain SYSTEM privileges on a PC with Google Chrome).
issues.chromium.org/issues/40946325](https://pbs.twimg.com/media/GIMCK6QXYAAimLT.jpg)

![NetSPI (@netspi) on Twitter photo [Blog] CVE-2024-21378 – Microsoft Outlook Remote Code Execution
How we discovered & were able to exploit this vulnerability: ow.ly/L29F50QQ7s4
Written by: Rich Wolferd, NetSPI’s Director of Red Team Operations & Nick Landers <a href="/monoxgas/">monoxgas</a> [Blog] CVE-2024-21378 – Microsoft Outlook Remote Code Execution
How we discovered & were able to exploit this vulnerability: ow.ly/L29F50QQ7s4
Written by: Rich Wolferd, NetSPI’s Director of Red Team Operations & Nick Landers <a href="/monoxgas/">monoxgas</a>](https://pbs.twimg.com/media/GIZEpxZXoAAGEwX.jpg)



