Connor McGarr
@33y0re
Software Engineer @preluderesearch
ID: 1160734131531243520
https://connormcgarr.github.io 12-08-2019 02:05:57
907 Tweet
9,9K Followers
90 Following

Looks like BlueHat IL talks are online now, so here’s my talk for anyone who wanted to learn about the latest episode of KASLR and couldn’t make it: youtu.be/Dk2rLO2LC6I



Chatting with mah fwend and co-worker Jonny Johnson to learn all about Event Tracing for Windows, and some super cool projects he has been working on: a lightweight and custom "toy EDR" JonMon and ETWInspector to help with Windows telemetry research! youtu.be/BNWAxJFL6uM


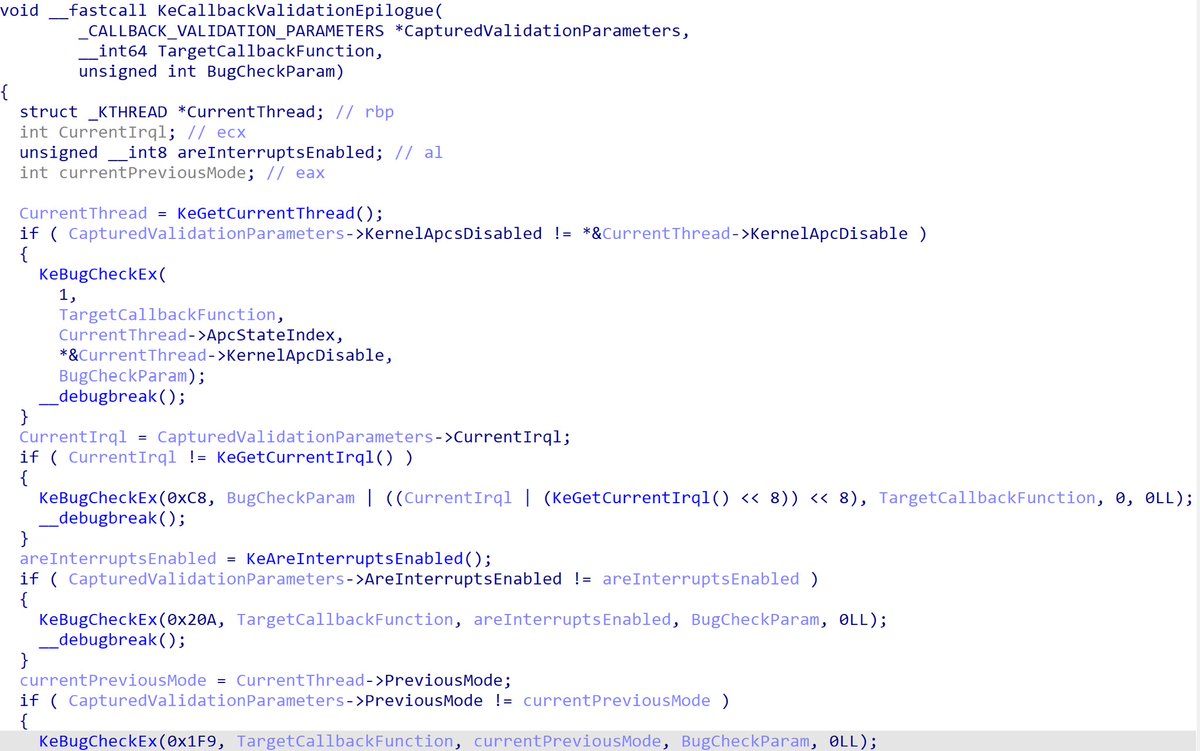
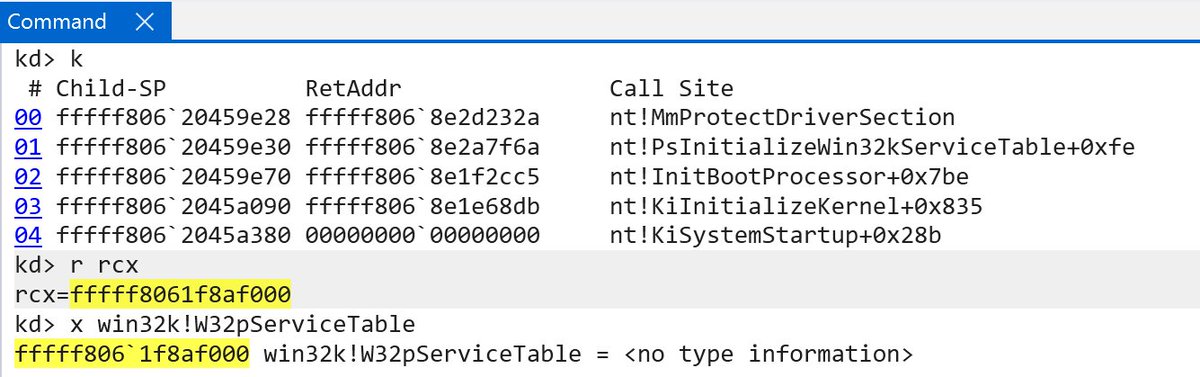
Exploit Development: Investigating Kernel Mode Shadow Stacks on Windows, by Connor McGarr connormcgarr.github.io/km-shadow-stac…









My slides are available now! Thank you Alex Plaskett !!!