
Bandar Alharbi
@0xb4x
(•)E Focusing mode
ID: 2895615482
https://www.0x01team.com/ 10-11-2014 12:46:11
5 Tweet
51 Followers
122 Following


Happy to share (me, Bandar Alharbi & Meshari) our new findings on Microchip Atmel SAM E70/S70/V70/V71 family Writeup - CVE-2024-4760: 0x01team.com/hw_security/by… Were we are able to bypass the security mechanism by voltage fault injection⚡️!
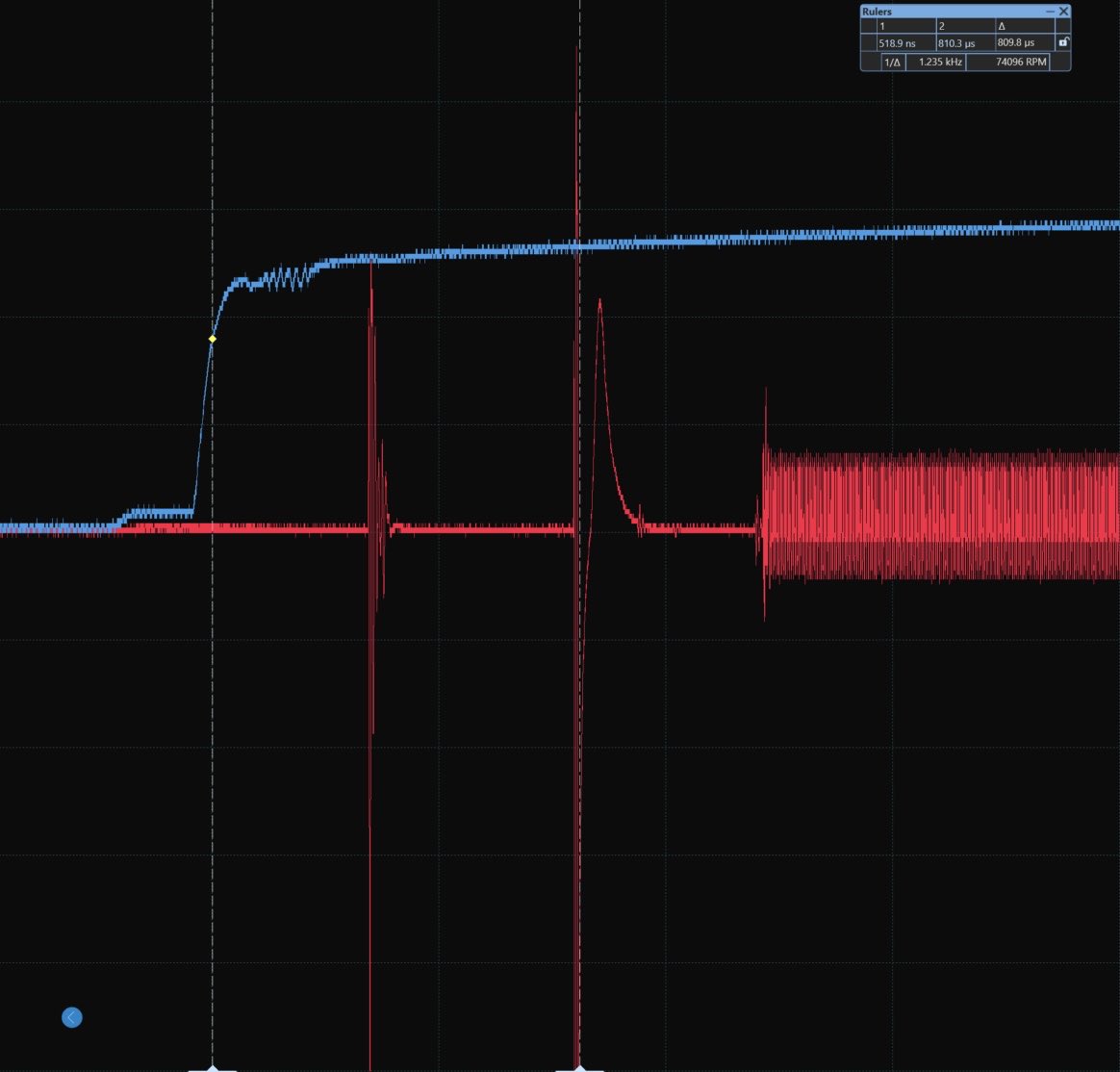


We were able to fully emulate a Cortex-M7 MCU ROM code after dumping it… we used Qiling Framework to do it. It’s interesting when you have almost full control without any hardware, allowing you to reverse and fuzz the binary! 0x01team.com/sw_security/sa…


