🏴☠️
@dmnsch
¯\_(ツ)_/¯
ID: 81334833
10-10-2009 11:24:01
51 Tweet
41 Followers
139 Following



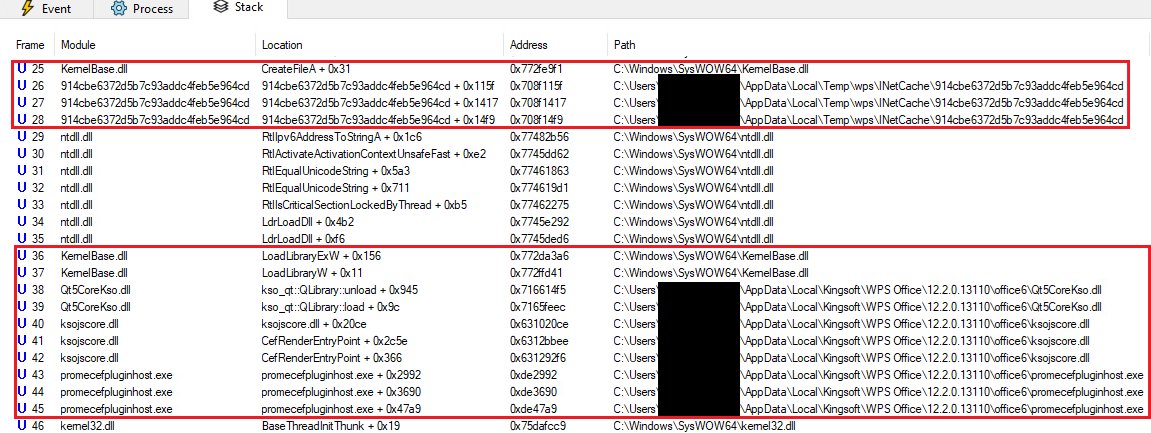
#POVERTYSTEALER #GOVUA #VBS #SSU DOC: d12934-0202334.doc MD5: eac138b49c6f90896c9af5cbc8fe38b8 DNS: npddocs[.]com IP: 194[.]31.109.82 RTI: hxxps://npddocs[.]com/ssu.gov.ua/docs/file/util/0/d12934-0202334[.]doc Next-Stage: \\89.23.98[.]22\LN\Konstantin.exe Mikhail Kasimov
![匚ㄚ乃乇尺ㄖᐯ乇尺ㄥㄖ卂ᗪ (@cyber0verload) on Twitter photo #POVERTYSTEALER #GOVUA #VBS #SSU
DOC: d12934-0202334.doc
MD5: eac138b49c6f90896c9af5cbc8fe38b8
DNS: npddocs[.]com
IP: 194[.]31.109.82
RTI:
hxxps://npddocs[.]com/ssu.gov.ua/docs/file/util/0/d12934-0202334[.]doc
Next-Stage:
\\89.23.98[.]22\LN\Konstantin.exe
<a href="/500mk500/">Mikhail Kasimov</a> #POVERTYSTEALER #GOVUA #VBS #SSU
DOC: d12934-0202334.doc
MD5: eac138b49c6f90896c9af5cbc8fe38b8
DNS: npddocs[.]com
IP: 194[.]31.109.82
RTI:
hxxps://npddocs[.]com/ssu.gov.ua/docs/file/util/0/d12934-0202334[.]doc
Next-Stage:
\\89.23.98[.]22\LN\Konstantin.exe
<a href="/500mk500/">Mikhail Kasimov</a>](https://pbs.twimg.com/media/F-W18whWAAASDgG.png)


#ESETResearch has observed an alarming growth of deceptive Android loan apps offering personal loans designed to defraud users and gain their personal information. Many of these apps found their way to official marketplaces. Lukas Stefanko welivesecurity.com/en/eset-resear… 1/8
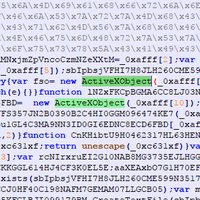



#ESETresearch has discovered a new campaign by 🇨🇳China-aligned #APT #EvasivePanda, leveraging the Monlam Festival to target Tibetans. The campaign included a targeted watering hole, compromised news website, and an additional supply-chain attack ... welivesecurity.com/en/eset-resear… 1/7






#ESETresearch’s Jean-Ian Boutin and __mat__ will be presenting at LABScon 2025 this Friday. Join them on site to hear about #Ebury - see the the full scale of a sophisticated Linux threat & about DigitalRecyclers, another member of the APT15 galaxy. events.sentinelone.com/event/LABScon2…





![souiten_4t_FuYingL4b (@souiten) on Twitter photo #maldoc targeting Indonesia government
file:
9ef96a2ca17ba3371fb5480b3e9083f9
Undangan KPU.docm
dl-url:
http://13.211.167[.]218/Update.exe
payload #meterpreter
d8e61c36fd3d2d31ff0ef02dd5112122
48.125.170[.]13:4444 #maldoc targeting Indonesia government
file:
9ef96a2ca17ba3371fb5480b3e9083f9
Undangan KPU.docm
dl-url:
http://13.211.167[.]218/Update.exe
payload #meterpreter
d8e61c36fd3d2d31ff0ef02dd5112122
48.125.170[.]13:4444](https://pbs.twimg.com/media/F9HV5VSawAAICFH.png)