
Asi Greenholts
@tupletype
Concentrated AppSec juice • Security Researcher @PaloAltoNtwks
ID: 1440528621613895682
https://greenholts.com 22-09-2021 04:09:37
43 Tweet
182 Followers
52 Following





My submission got accepted to BSides Las Vegas!! Join me at the underground track 🤫 where I'll talk about: The GitHub Actions Worm: Compromising GitHub repositories through the action dependency tree 🌳


Highly inspired by our OWASP® Foundation Top 10 CI/CD Security Risks project, cool:)







📚 tl;dr sec 234 🗡️ Awesome CI/CD Attacks Asi Greenholts 🤖 STRIDE GPT ☁️ Non Production AWS Attack Surface Nick Frichette 🛡️ Secure defaults Rami McCarthy 🛠️ WAF bypass tool shubs 💻 Hacking millions of routers Sam Curry tldrsec.com/p/tldr-sec-234

Right now on stage Asi Greenholts with “The GitHub Actions Worm: Compromising GitHub repositories through the actions dependency tree”! Join live: youtube.com/live/tlBnIA9FQ…


Thank you Yaniv Hoffman for inviting me to discuss about CI/CD security and my "Awesome CI/CD Attacks" project. We explored challenges, solutions, and key insights in this critical area of cybersecurity. youtube.com/watch?v=FiTERo…


This Saturday I will be speaking at #DefCon32 about OIDC misconfigurations and abuses in the context of CI/CD 🥴👹. Come check it out! info.defcon.org/event/?id=54867 Palo Alto Networks #OIDC #oauth2 #ci #cd


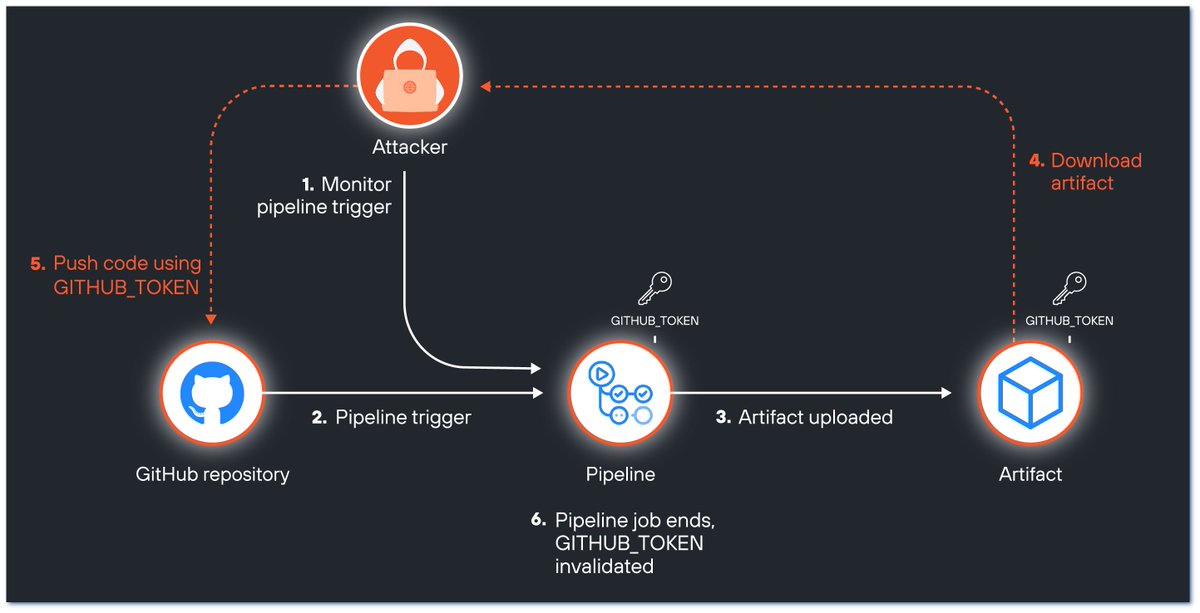
New research our team released today, showing how we could push code to highly popular open source projects maintained by Google, AWS, Microsoft, & Red Hat, through a race condition in GitHub Actions. Go hunt critical #bugbounty issues ;) by Yaron Avital unit42.paloaltonetworks.com/github-repo-ar…

🚨 We know the real target behind the attack on tj-actions/changed-files! Coinbase! The first publicly known exploitation of the technique I presented at DEFCON 31: The GitHub Action Worm. Read the full story: unit42.paloaltonetworks.com/github-actions… By Omer Gil Yaron Avital Aviad and I


