Tao Idr
@tao_officiel
⚔️ Cybersecurity Specialist × Red Teaming | Privacy × Security | Crypto × Web3 |
❤️ Aviation × Chess • Gaming × Photography
ID: 978967657033674752
28-03-2018 12:10:52
1,1K Tweet
152 Followers
291 Following









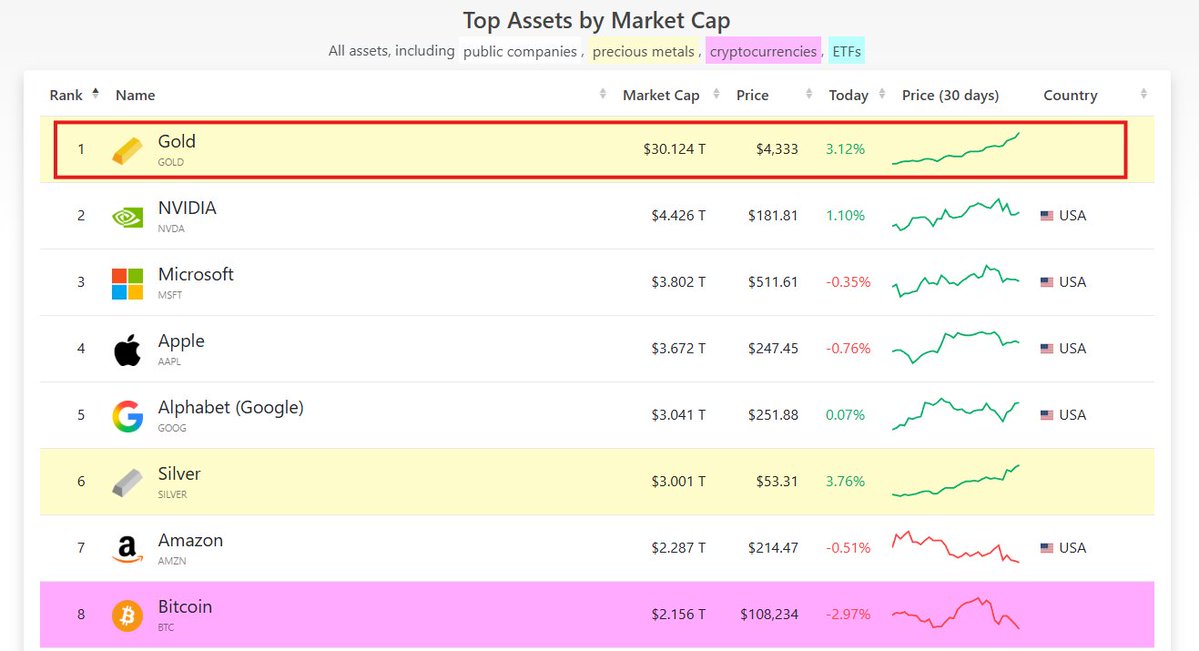
.Giggle Academy now teaches 70,000 kids for free. New version is backward compatible to iOS15 (really old version) to accommodate our demographic.