Davide Avilloni 🇮🇹🏴
@aristodemox
0x..
ID: 287606350
25-04-2011 09:56:08
10,10K Tweet
296 Followers
1,1K Following





exploiting #Zerologon... Tired: boring all 0s challenge 😴 Wired: Exciting challenges with non 0 values 🥳 See my new blog on the matter medium.com/@TalBeerySec/z… Thanks to @djrevmoon.bsky.social Dirk-jan 🥝🏳️🌈 Benjamin Delpy Samir Mitja Kolsek 0patch Ophir Harpaz 🎗️ @SagieSec Chris Nickerson Secura





A relatively new implant, which we have dubbed #SlothfulMedia, has been used to target victims in a number of countries, including: India, Kazakhstan, Kyrgyzstan, Malaysia, Russia and Ukraine. See more on U.S. Cyber Command's Virus Total page: virustotal.com/gui/file/64d78…


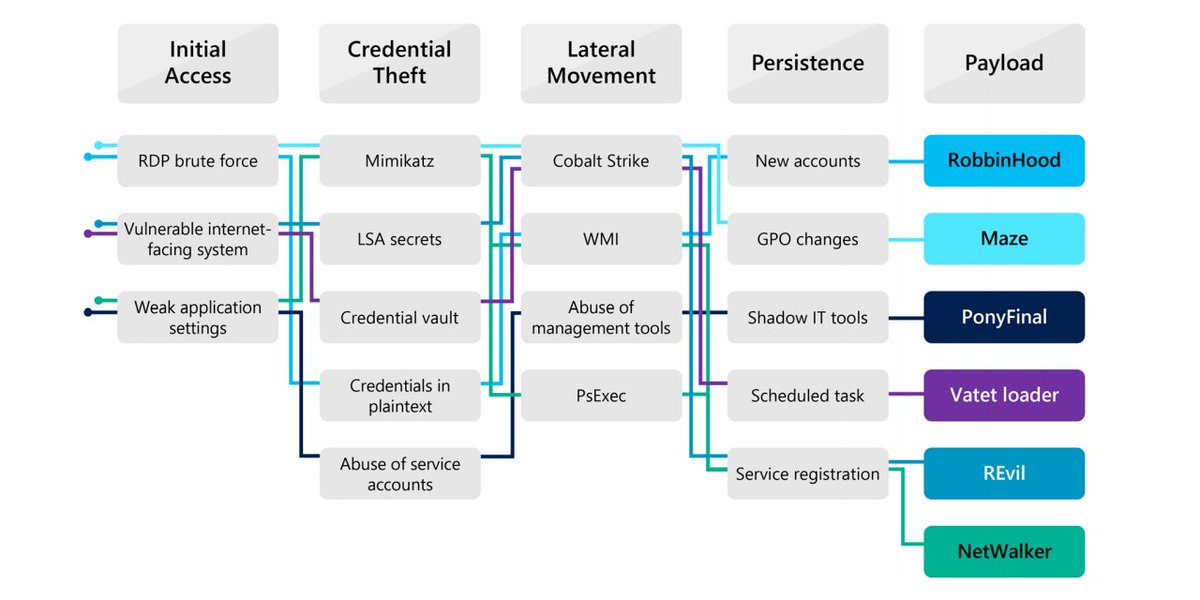
Presented Virus Bulletin 2020 - this excellent session by @Glacius___ and Jeffrey Sman on Netwalker #ransomware is definately worth watching youtube.com/watch?reload=9… #malware #cybersecurity

Excited to publish our research in which Eyal Itkin and I were able to fingerprint 2 of the most active exploit developers for Windows. Together, they account for 16 Windows LPE exploits, of which 5 were 0-Days that were sold to APTs and crime groups. research.checkpoint.com/2020/grapholog…





Here is the recording of the full x64 Linux Binary exploitation training. Couldn’t cover few topics due to time restrictions, but overall I am happy with the coverage. Thanks to all, who submitted the pre-training challenge and attended. The Offensive Labs youtu.be/gxU3e7GbC-M