Anchor
@datanchor
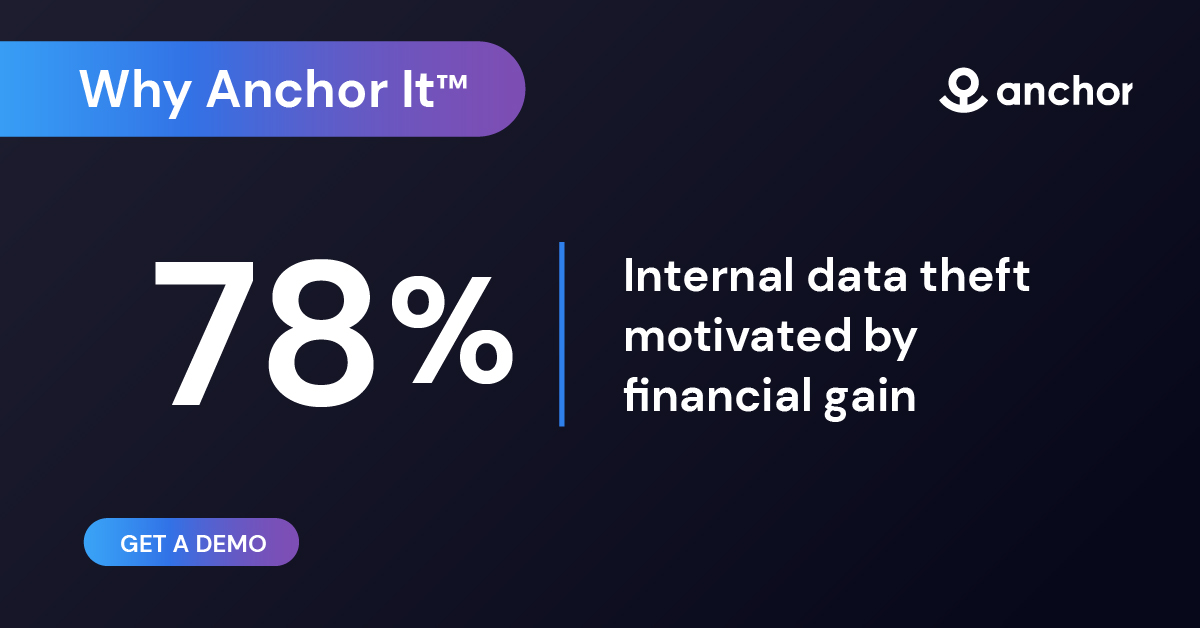
Anchor redefines IT security with the security baked right into the data. Anchored files remain secure, controlled, and auditable. Sensitive data? Anchor it™.
ID: 1229840490218086400
http://anchormydata.com 18-02-2020 18:50:40
134 Tweet
66 Takipçi
90 Takip Edilen