cyb3rmeerk4t
@cyb3rmeerk4t
ID: 968386361366478848
27-02-2018 07:24:35
154 Tweet
38 Followers
827 Following










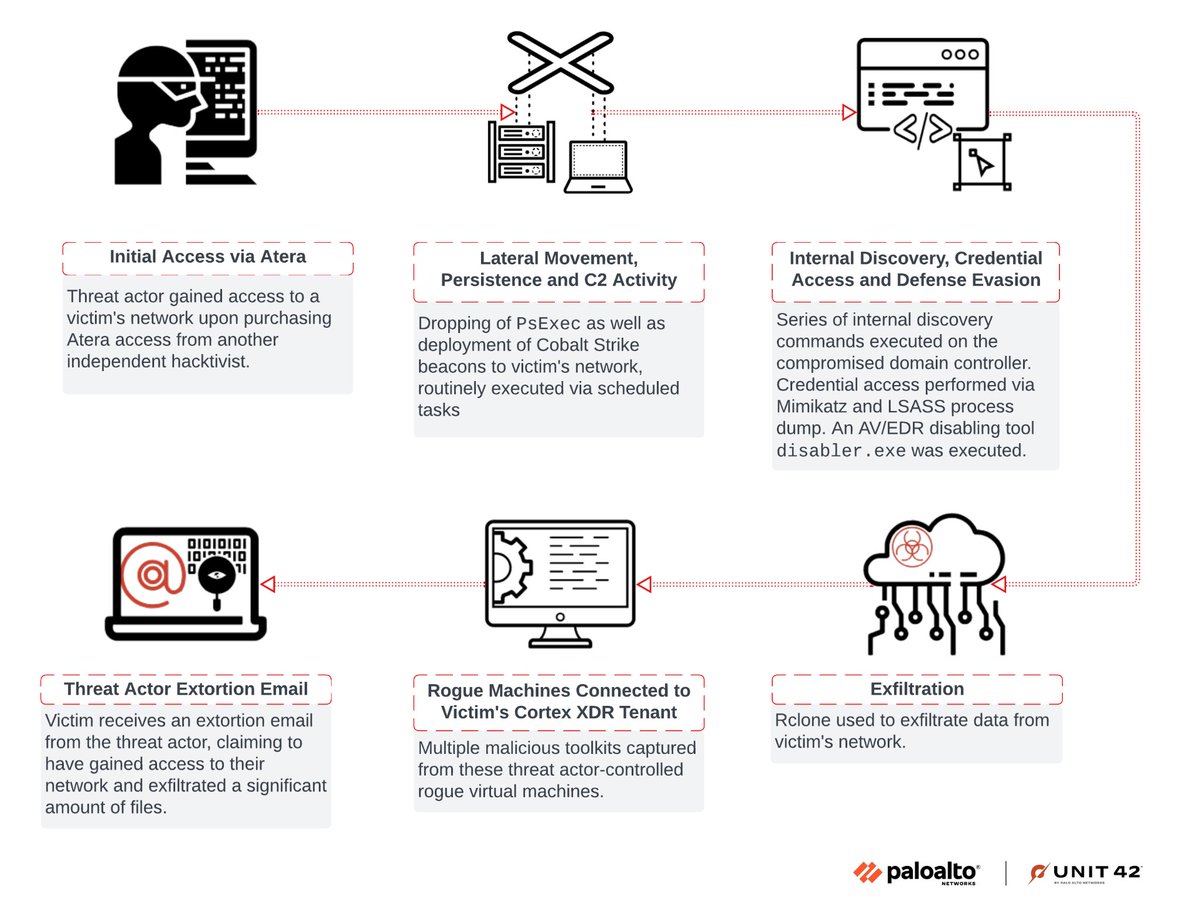
Palo Alto Networks analysts Navin Thomas, Renzon Cruz & Cuong Dinh look into an AV/EDR bypass tool discovered during investigation of an extortion attempt. The threat actor purchased access to the client network via Atera RMM from an initial access broker. unit42.paloaltonetworks.com/edr-bypass-ext…


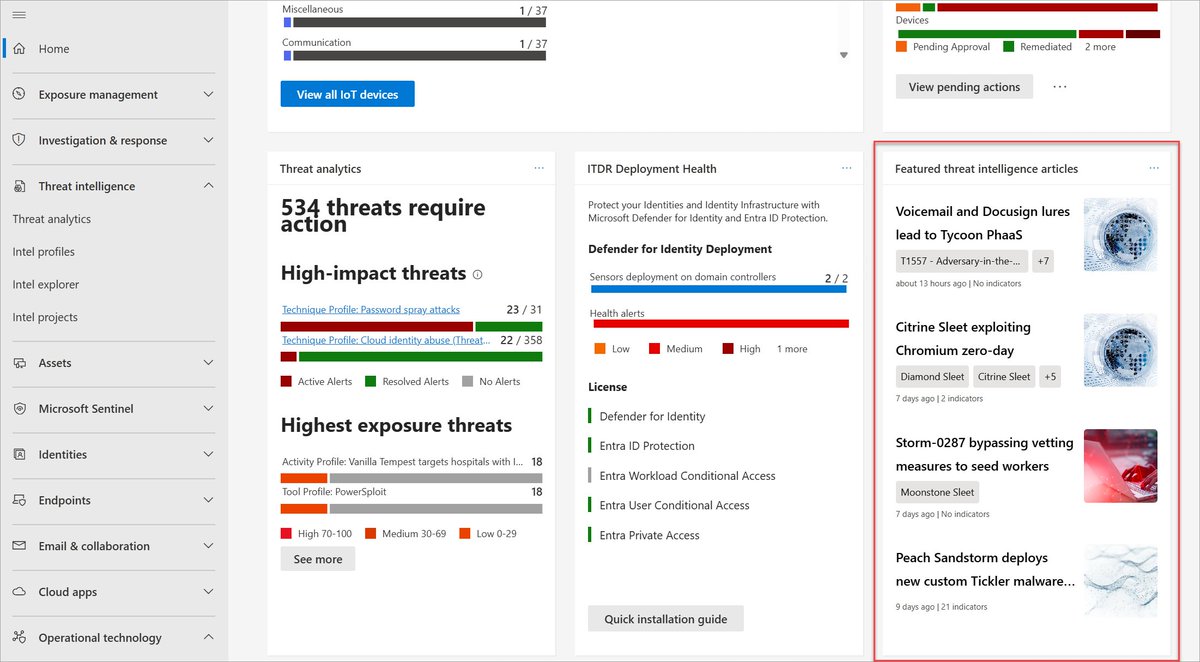
At CYBERWARCON, Microsoft is sharing research on North Korean threat actors who steal cryptocurrency and target satellite & weapons systems orgs, as well as details on intelligence collection operations by Chinese threat actor Storm-2077. Learn more: msft.it/6016Wvv28






📣 3 Weeks Away! | Join Katie Nickels Rebekah Brown Rick Holland & your community at #CTISummit for in-depth talks ft. cutting-edge insights, techniques, & solutions. 🗓️ Summit: Jan 27-28 📍 DC Metro | All-Access OR 🌐 Free Online | Select Talks ➡️ Register: sans.org/u/1xCe