
CimTrak Integrity
@cimtrak
Security and compliance tool; Detect, alert and respond to changes in your IT environment. File Integrity Monitoring #PCIDSS #cybersec #infosec #ITSecurity
ID:236995760
http://www.cimtrak.com 11-01-2011 21:02:47
3,1K Tweets
2,2K Followers
1,6K Following

Happy RSA Week! 🎉
You won't want to miss seeing the Cimcor, Inc. team at the LogRhythm booth - Wednesday May 8th.
#RSAC #RSAC onference #Cybersecurity #LogRhythm #CimTrak


Whether you're a defense contractor navigating compliance or an organization aiming to bolster your cybersecurity posture, understanding the basics of CMMC is the first step toward success.
hubs.la/Q02ndLpn0
#CMMC #compliance #cybersecurity

NIST 800-171 Revision 3 signifies a substantial evolution in the standard, demanding the attention of organizations handling CUI. Staying informed and staying compliant are of the utmost importance. Learn more ⬇️
hubs.la/Q02k0RtT0
#NIST800171 #CMMC #compliance

Members of the Cimcor team are heading to the Automate Conference in Chicago next week! 🛡️
Attending the event? Let us know! ➡️ hubs.la/Q02vZGZr0
#Automate2024 #cybersecurity #infosec #conferenceszn


In this latest podcast, let's review the federal rules for reporting not only cybersecurity incidents but also ransomware payments for critical infrastructure operators. Listen to the podcast ⬇️
hubs.la/Q02vZNVc0
#criticalinfrastructure #cybersecurity #ransomware #infosec

The Cimcor team is heading to RSA Conference next week! 🛡️
Attending the event? Let us know! ➡️ hubs.la/Q02vNVkr0
#RSAConference2024 #RSAC24 #RSAC2024


Zero-day attacks pose serious risks, but file integrity monitoring can identify them. Learn 3 ways FIM detects and protects against these stealthy threats before damage occurs.
hubs.la/Q02vMR2f0
#cybersecurity #zeroday #fileintegritymonitoring

Achieving HIPAA compliance is complex, but maintaining it is often even more challenging. These 5 FIM facts can help healthcare organizations with many of the key requirements in their compliance journey. ⬇️🛡️
hubs.la/Q02mKv9x0
#HIPAA #cybersecurity #compliance

Change monitoring is one important tool to stay on top of risks, but it's not the only piece of the puzzle...
hubs.la/Q02dSVSv0
#changemanagement #changemonitoring #changecontrol #cybersecurity

Attending IT compliance conferences is an excellent way to stay up-to-date on current trends, requirements, and policies. Here are the 11 best IT compliance conferences you may want to attend in 2024 ⬇️
hubs.la/Q02q9Qjt0
#cybersecurity #compliance #conferences #events

What happens when organized crime groups become the dominant force in cybercrime?
hubs.la/Q02r3wJk0
#cybercrime #cybersecurity #infosec

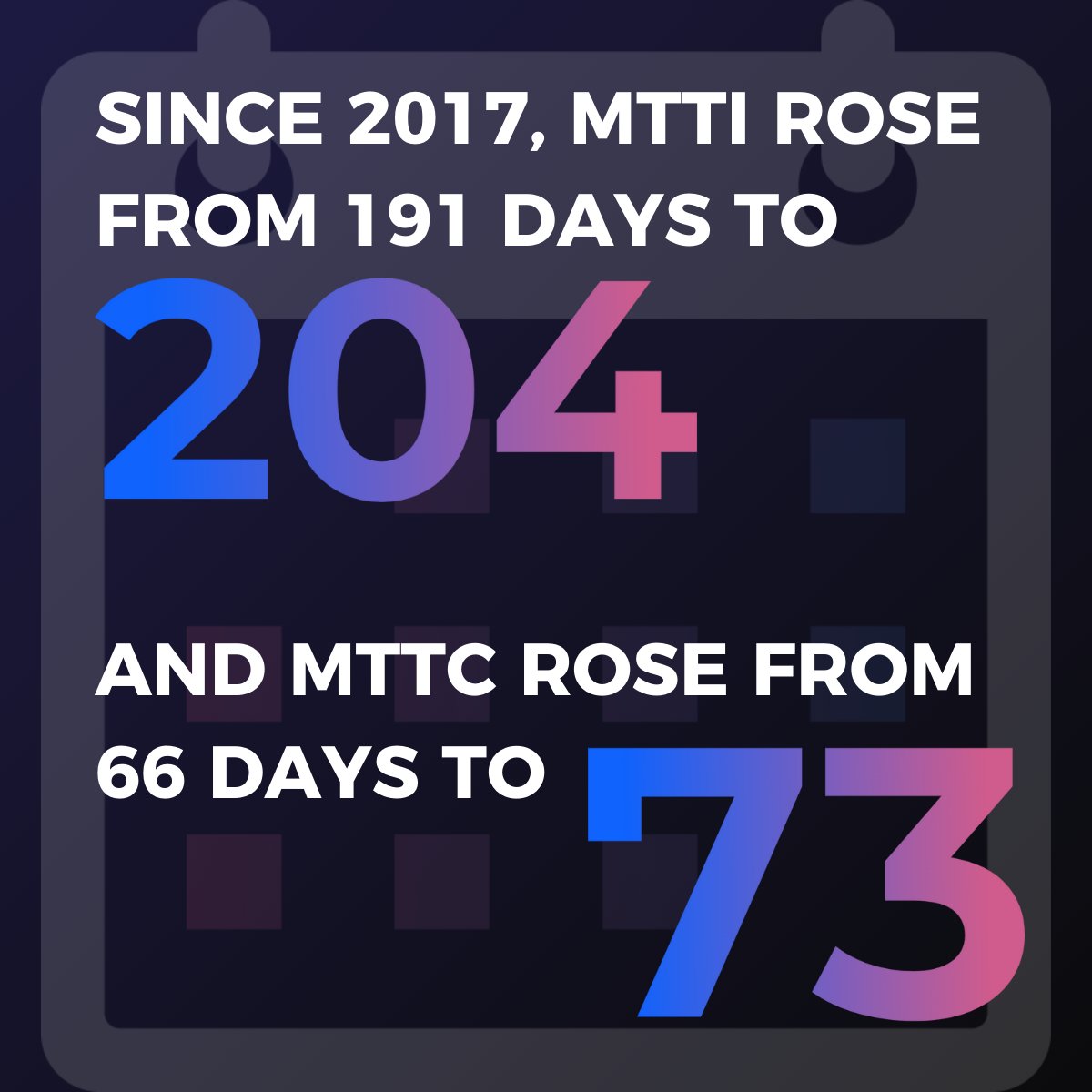
Despite rising cybersecurity budgets, breaches are harder to detect and contain. Learn the overlooked basics that are key to achieving and maintaining a robust security posture. 🛡️
hubs.la/Q02v2yb80
#CybercrimeInsights #Cybersecurity #Infosec #DataBreach

Adding to the mix of existing cyber threats, other types of malware and malicious infrastructure are being offered as-a-service on the dark web.
For more on growing cyber trends, download our latest Cybercrime Landscape Report! ⬇️
hubs.la/Q02rZCbC0
#CybercrimeReport2023



Does your business need to be PCI compliant? Let's cover the basics.
hubs.la/Q02lHyPV0
#PCI #compliance #cybersecurity

The industry is going backward. What can we do about it?
Learn more about the changes in the Cybercrime Landscape and where we go from here in our latest report.⬇️
hubs.la/Q02rZvT60
#CybercrimeReport2023 #CybersecurityInsights

AI-powered cybercrime is on the rise, with deepfakes and AI-generated content fueling more convincing social engineering and phishing attacks. Learn how threat actors are leveraging these emerging tactics. 🤖⬇️
hubs.la/Q02tkShs0
#cybersecurity #AI #socialengineering

For DoD contractors aiming to reach CMMC 2.0 compliance before the final deadline, here are seven CMMC challenges they are likely to face. ⬇️
hubs.la/Q02lcdH00
#CMMC #compliance #DoD #cybersecurity

T-2 hours until this week's Walkthrough Wednesday! ⏳It's not too late to join - secure your spot now! ⬇️
hubs.la/Q02t9bg30
#WalkthroughWednesday #CimTrak #FileIntegrityMonitoring #Cybersecurity #Infosec


Cybersecurity expert Tom Cornelius raises concerns that many CISOs may be engaging in criminal behavior. Explore his take on the cybersecurity industry's top challenges. ⬇️
hubz.li/Q02t3vFs0
#CybercrimeInsights #Cybersecurity