ʇıq
@charlievedaa
blue team, GSE #112
ID: 349134123
http://xn--q-eka93h.com 05-08-2011 16:17:08
216 Tweet
753 Followers
5,5K Following

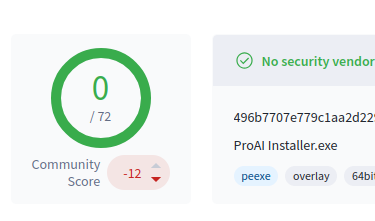
Again recommending my fun VirusTotal course on KC7 - Cyber detective game: kc7cyber.com/modules/VT101 It covers basics I've not seen elsewhere to empower analysts. Example: Signed File has 0/72 score virustotal.com/gui/file/496b7… Is it benign or not? How can we quickly come to a conclusion? /1









This is a simple .NET tool I wrote as apart of my research with Jonathan Beierle called Krueger, meant for disabling EDR remotely with WDAC to assist in lateral movement activities. github.com/logangoins/Kru…