I¯\_(ツ)_/¯I \ (•◡•) /
@bountyoverflow
BBH ( ͡° ͜ʖ ͡°) 💰 @Bugcrowd Top 50 \o/ ✌️ MVP✌️
I am here to learn/share application security stuff ✌️
I enjoy finding auth bypass bugs 🐞
ID: 223011491
05-12-2010 03:36:07
1,1K Tweet
6,6K Followers
1,1K Following

















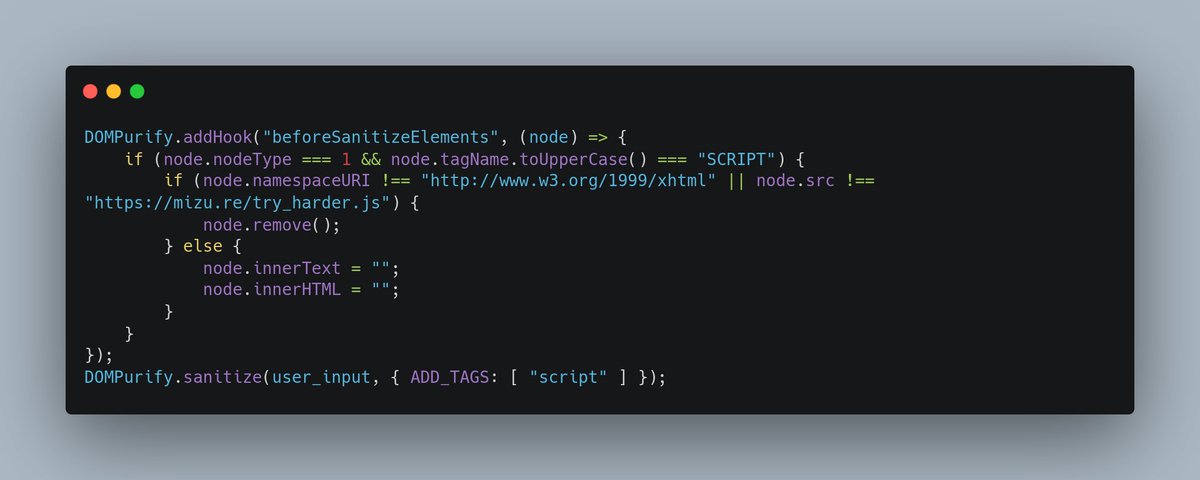
Thanks to the recent PortSwigger top 10, I finally found the motivation to finish writing the 2nd article about DOMPurify security! 😁 Before releasing it, I would like to share a small challenge 🚩 Challenge link 👇 challenges.mizu.re/xss_04.html 1/2