Bojan Zdrnja
@bojanz
IT Security guy, penetration testing is my thing. One of the SANS Internet Storm Center handlers at isc.sans.org. SANS SEC542 instructor and course co-author.
ID: 21474216
https://www.infigo.hr 21-02-2009 09:42:17
2,2K Tweet
4,4K Followers
689 Following

Wrote a short diary about some reversing I did on the #xz #xzbackdoor at isc.sans.edu/diary/30802 SANS.edu Internet Storm Center with a bit more explanation of few functions.

Greetings cybersecurity collective, lectures (bsideszagreb.srce.hr/schedule/) and photos (flickr.com/photos/srcehr/…) are available. Deep appreciation to our exceptional lecturers, sponsors, and attendees! Powered by Srce Sponsored by Help Net Security and Diverto security #bsides


🚨 #WJAI Special Episode: Unpacking the xz-utils Backdoor Crisis! Tune in tomorrow as SANS experts Johannes Ullrich & Bojan Zdrnja dissect the threat that has shaken the open-source community. Set your alert now ▶️ youtube.com/live/HTNKS3tw3…


🤝 Strengthen your defenses & advance EU SANS NIS 2 research Bojan Zdrnja explains, “By participating, orgs take a significant step towards bolstering their defenses " ✍️ Complete the survey now → sans.org/u/1vtf #SANSTraining #Cybersecurity #NIS2 #Compliance


💬 Be part of the solution: Take the EU NIS 2 Survey and chart the cybersecurity course ✍️ Take the lead – Your insights can drive change. Share your thoughts by 10 May → sans.org/u/1vtf Dean Parsons Bojan Zdrnja | #SANSTraining #Cybersecurity #NIS2 #Compliance


📣 Starting in 15 Min! | Join us for #SANSAiForum to hear firsthand accounts of how SANS Faculty are using #AI to make significant advancements in #cybersecurity w/ talks from Mick Douglas 🇺🇦🌻 sethmisenar Jorge Orchilles Tim Schulz & more! Register/Join: sans.org/u/1uVn


Several classes at #SANSFIRE are led by SANS.edu Internet Storm Center handlers: SEC542 Web Pentesting Bojan Zdrnja FOR610 Rev Malware Xavier Mertens @[email protected] 🇧🇪 SEC522 Defending Web Apps Johannes Ullrich We also have some great additional events exclusive for live attendees. See you in July! In person!

⏳ Time's ticking: Share your thoughts on EU cybersecurity regulations! Take part in the essential survey by Dean Parsons and Bojan Zdrnja to guide industries through new Directives. ✍️ Lend your voice → sans.org/u/1vtf #SANSTraining #Cybersecurity #NIS2 #Compliance


Quick Hackfest Hollywood keynote announcement: Day One Keynote: David Weston (David Weston (DWIZZZLE)) Day Two Keynote: Yarden Shafir (Yarden Shafir) October 28th & 29th in Los Angeles! Register for virtual (free) & in-person attendance here: sans.org/cyber-security…

🇪🇺 Orgs are quickly running out of time to prepare for new EU #NIS2 regulations. SANS expert Bojan Zdrnja emphasises, "Early prep is crucial." Start your journey to compliance with SANS → sans.org/u/1wi8 Read more → csoonline.com/article/210596… #SANSTraining #Compliance

⚠️ Deadline extended: Participate in the SANS Institute survey by Dean Parsons and Bojan Zdrnja to prepare your organisation. 1️⃣ Take the survey → sans.org/u/1vtf 2️⃣ Complete the questions 3️⃣ Submit by 31 May #SANSTraining #Cybersecurity #NIS2 #Compliance


And I will be there teaching SEC542. Come hack web applications with me, or secure them with Johannes Ullrich and enjoy talks by other SANS.edu Internet Storm Center handlers!

If you are into web application penetration testing make sure that you read the new blog by my talented colleague Mateo Hanžek who wrote about some novel event handler XSS techniques that can be used to bypass WAF's too :)

25 years! What a ride. Very proud to be part of SANS.edu Internet Storm Center and looking forward to another 25 years!


🇪🇺 Navigate NIS2 Directive: Key Compliance Tips for EU Businesses Catch our webcast with Dean Parsons & Bojan Zdrnja, to understand & comply with the new regs 🎦 Watch now → youtu.be/eaOpc1fU3YQ?si… ℹ️ Prepare with our resource hub → sans.org/u/1xEu #SANSTraining #NIS2


Have AllExtendedRights on a computer object? Besides reading its LAPS password, you can also reset its account password and takeover the target computer. Downside - you'll break its AD membership. Kudos to Luka Srdarev for exploiting this in a recent engagement :-) #RT
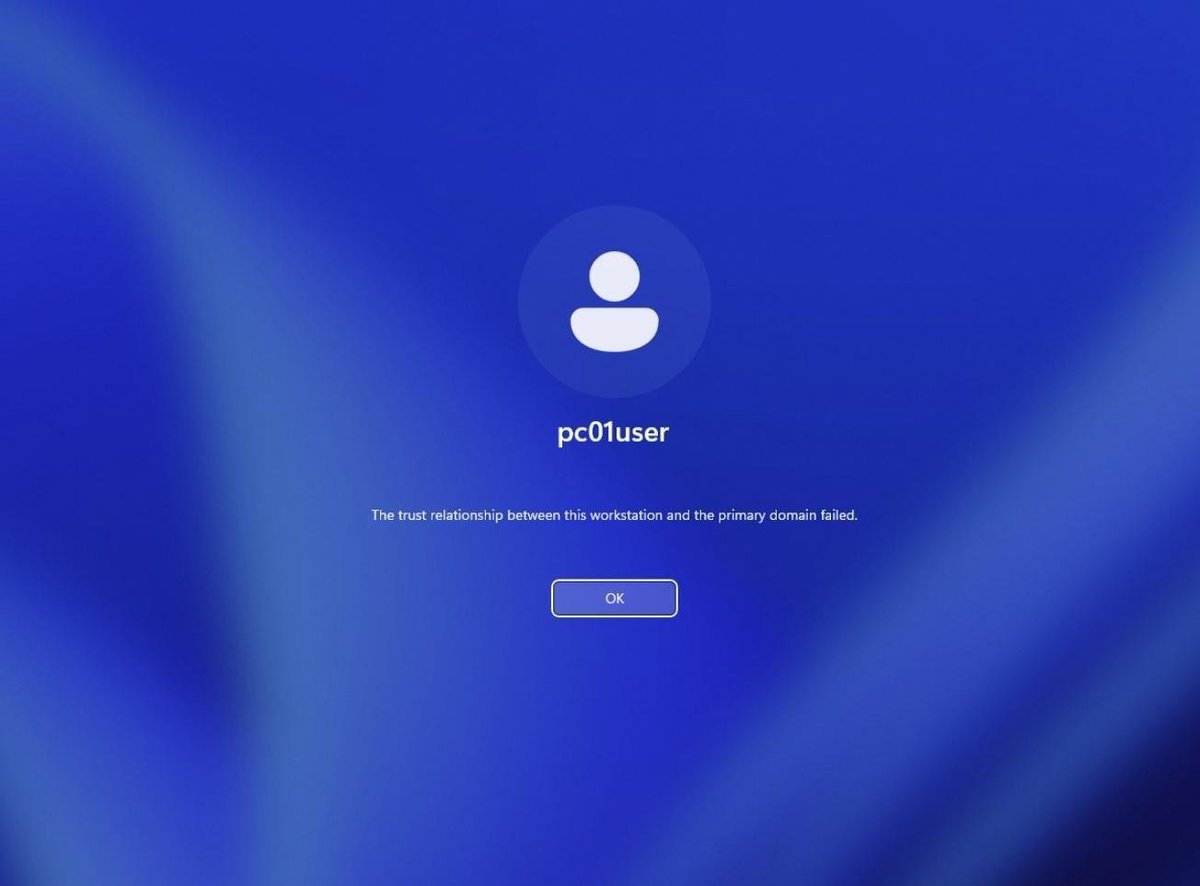


New diary: how Credential Guard prevented extraction of TGT from a service ticket by abusing Benjamin Deply's trick and why you should aim to enable it everywhere. Read the SANS.edu Internet Storm Center diary at isc.sans.edu/diary/Credenti…