
Lê Văn Hùng
@iam_hscorpion
Security Researcher 🇻🇳
ID: 976413630026588160
21-03-2018 11:02:05
104 Tweet
38 Takipçi
486 Takip Edilen






One Bug to Rule Them All: Stably Exploiting a Preauth RCE Vulnerability on Windows Server 2025 by zhiniang peng @ver0759 Zishan Lin i.blackhat.com/Asia-25/Asia-2…








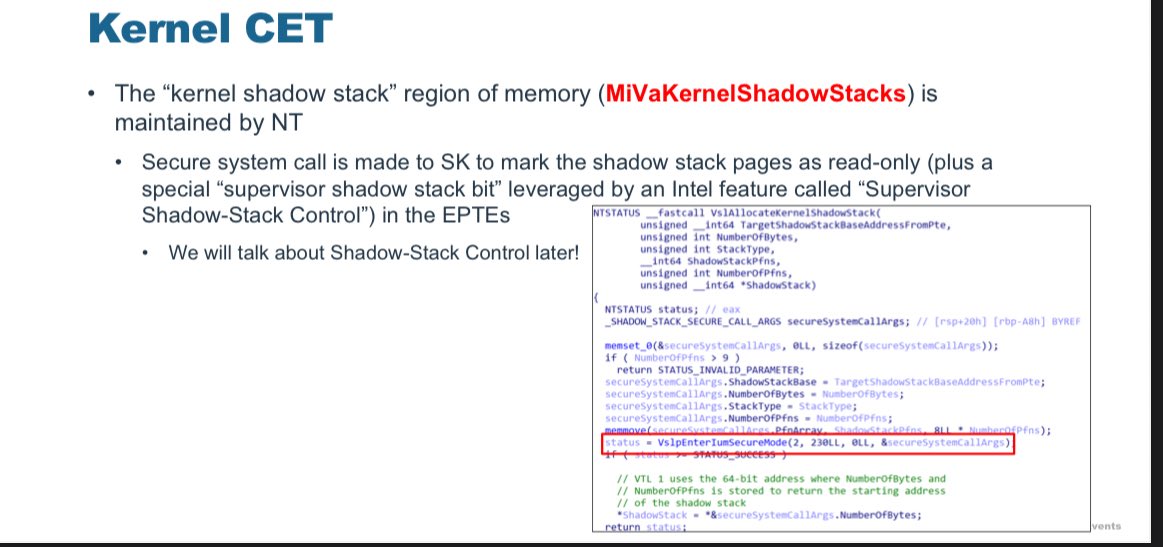
Out Of Control: How KCFG and KCET Redefine Control Flow Integrity in the Windows Kernel by Connor McGarr i.blackhat.com/BH-USA-25/Pres…






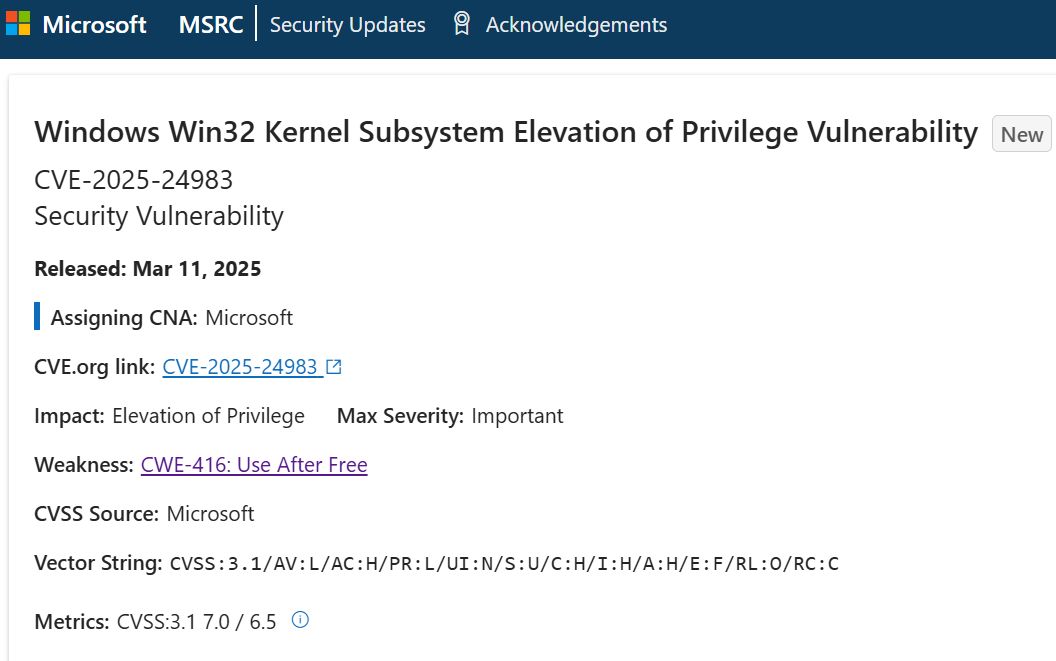



![hackyboiz (@hackyboiz) on Twitter photo [Research] CVE-2025-24985: Windows Fast FAT Driver RCE Vulnerability
hackyboiz.github.io/2025/07/17/ogu…
The vulnerability was caused by the ability to control five variables within the VHD file that determine the number of clusters. [Research] CVE-2025-24985: Windows Fast FAT Driver RCE Vulnerability
hackyboiz.github.io/2025/07/17/ogu…
The vulnerability was caused by the ability to control five variables within the VHD file that determine the number of clusters.](https://pbs.twimg.com/media/GwC4HkLasAEh-9D.jpg)
