
daevlin
@daevlin
Mr Malware, meet Mr Poke and Mr Stick
ID:22911209
https://daevlin.github.io 05-03-2009 12:07:07
32,1K تغريدات
408 متابعون
334 التالية
Follow People









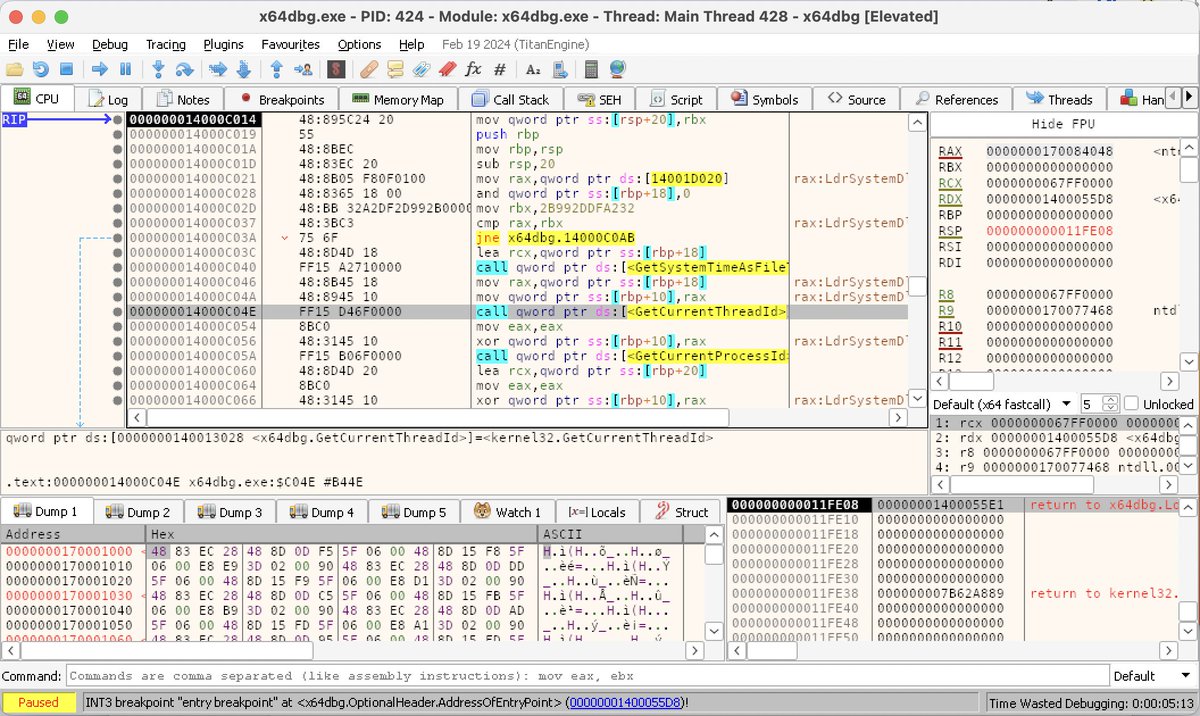
RE tip of the day: APIs like DebugActiveProcess, DbgUiDebugActiveProcess or NtDebugActiveProcess can be used by malware to attach to its own process. If the debugger is attached, they will fail this way revealing its presence
#infosec #cybersecurity #malware #reverseengineering








Do you like unpacking malware? We too! During our recent #AgentTesla analysis we wrote unpacker for #DotRunPeX , and decided to share it. Read our blog post for more info: cert.pl/en/posts/2023/…








![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2023-10-04 16:31:51 #Pikabot- #TA577 - url > .zip > .lnk > .dll cmd /c WX.pdf.lnk rundll32.exe xSa.log, HUF_inc_var c2's 102.129.139.]65:32999 79.141.175.]96:2078 167.86.96.]3:2222 144.64.204.]81:2078 45.131.108.]250:1194 38.242.240.]28:1194 IOC's github.com/pr0xylife/Pika… #Pikabot- #TA577 - url > .zip > .lnk > .dll cmd /c WX.pdf.lnk rundll32.exe xSa.log, HUF_inc_var c2's 102.129.139.]65:32999 79.141.175.]96:2078 167.86.96.]3:2222 144.64.204.]81:2078 45.131.108.]250:1194 38.242.240.]28:1194 IOC's github.com/pr0xylife/Pika…](https://pbs.twimg.com/media/F7m-BBGXQAQmyFb.jpg)
![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2023-09-27 16:22:13 #DarkGate - #TA577 - url > .zip > lnk > .vbs > .exe Some updated distro urls 👇 http://84.246.85.]138/xNn/ys http://162.19.130.]45/Gdt5p3y/vWw http://84.246.85.]121/nvT4ni/XX IOC's github.com/pr0xylife/Dark… #DarkGate - #TA577 - url > .zip > lnk > .vbs > .exe Some updated distro urls 👇 http://84.246.85.]138/xNn/ys http://162.19.130.]45/Gdt5p3y/vWw http://84.246.85.]121/nvT4ni/XX IOC's github.com/pr0xylife/Dark…](https://pbs.twimg.com/media/F7C5Np3WcAAOs_l.jpg)