AYYAN Irfan🇵🇸
@ayyanirfan16
Hacker | Muslim 🫀
ID: 1529931489894445058
26-05-2022 21:04:42
269 Tweet
19 Takipçi
192 Takip Edilen



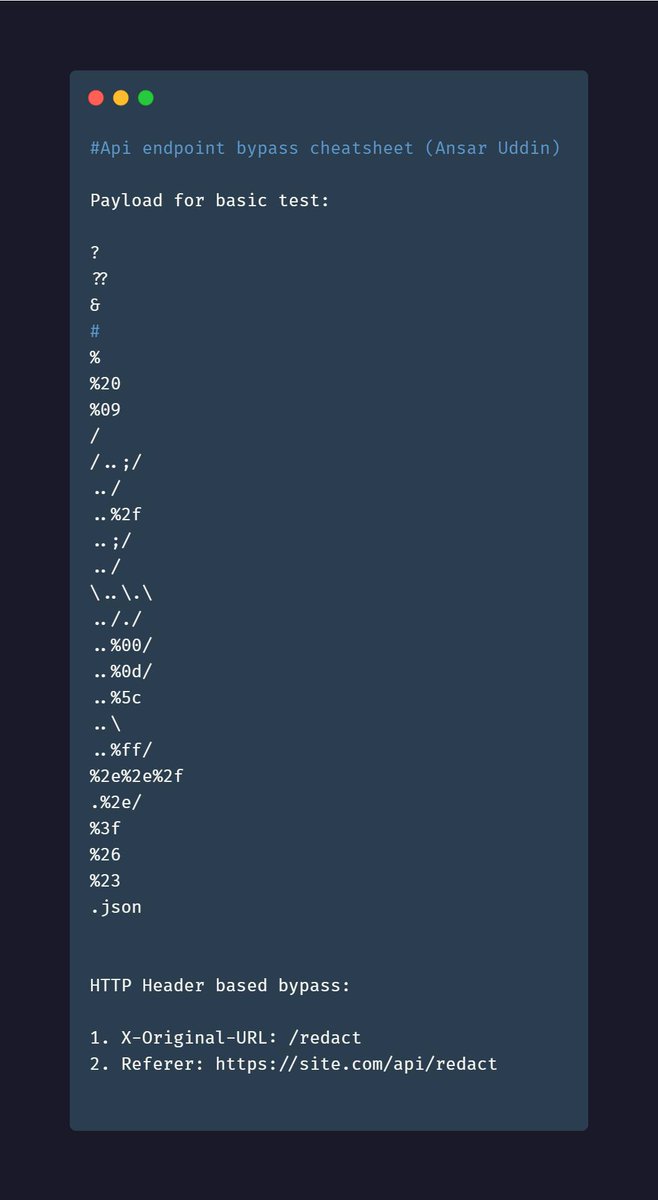
Becoming a pro in finding client-side bugs is simple. Not easy, but simple. 1. Go through a JS tutorial and understand the basics. 2. Ready everything on this blog 8x until you understand it: ysamm.com 3. Read JS for Hackers by Gareth Heyes \u2028 4x Then go hack stuff


I have a one year PentesterLab voucher for one random person retweeting and replying to this tweet with #nahamcon2023 :)





Hy BXSS Hunter I need your help I am new in bxss My payload got fired on a different subdomain How can I identify the vulnerable input field where I enter this payload and its got fired BXSS Hunter



OTP bypasses? Here are 10 blogs for testing OTP bypasses for bug bounty 1. aravind07.medium.com/otp-bypass-pat… 2. infosecwriteups.com/otp-bypass-and… 3. logicbomb.medium.com/otp-bypass-acc… 4. infosecwriteups.com/otp-bypass-on-… 5. shahjerry33.medium.com/otp-bypass-dev… 6. medium.com/@regan_temudo/… 7. medium.com/@arrheniuspael… 8.