Alae Eddine Lahlali
@aladinlahlali
sometimes accurate
ID: 781044387530825729
28-09-2016 08:14:28
28 Tweet
21 Takipçi
720 Takip Edilen








I just completed "Design Systems with React & Storybook" by Emma Bostian on Frontend Masters 💻✨! frontendmasters.com/courses/design… Very cool for those who want to learn some design jargon and dip their toes into Storybook! Storybook React

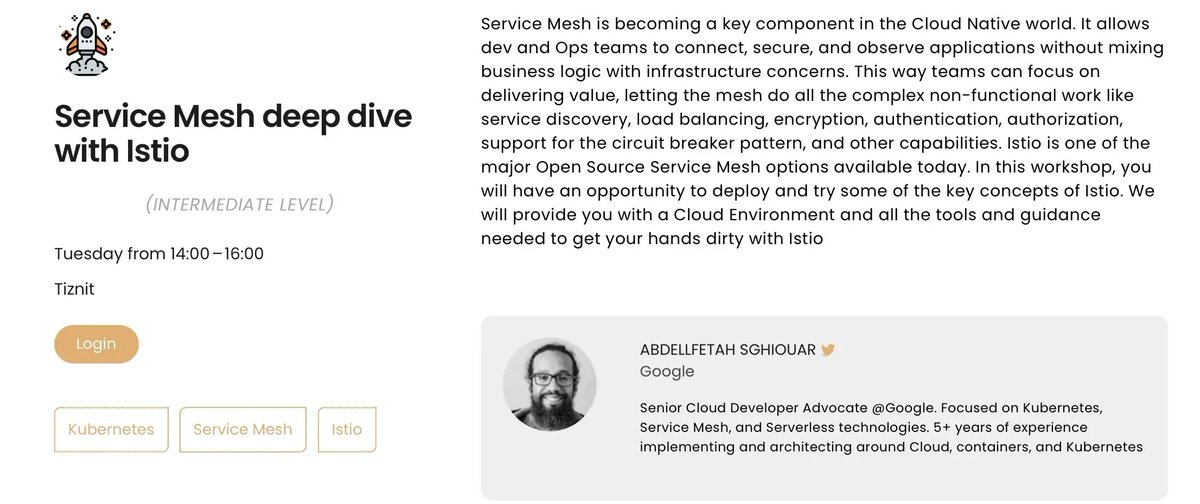
I’m giving two talks DevoxxMa 🇲🇦 November 12-14, 2025 this year A deep dive into Service Mesh with Istio on Tuesday Oct 4th at 2:00PM. A session on why probably DON’T need a Service Mesh on Thursday Oct 6th at 9:30AM. Check the schedule buff.ly/3SxArVS #DevoxxMA #DevoxxMA2022








Live Webinar: Overcoming Generative AI Data Leakage Risks thehackernews.com/2023/09/live-w… via The Hacker News

Youbit Bitcoin exchange quits operation after 2 hacks in 8 months hackread.com/?p=59833 via Hackread.com