PhreakingGeek
@PhreakingGeek
Purveyor of all things absurd. Security d00d. Lifelong learner. Human. Thoughts posted here are my own.
ID:250332794
http://keybase.io/phg 10-02-2011 22:01:58
8,3K Tweets
2,2K Followers
3,3K Following




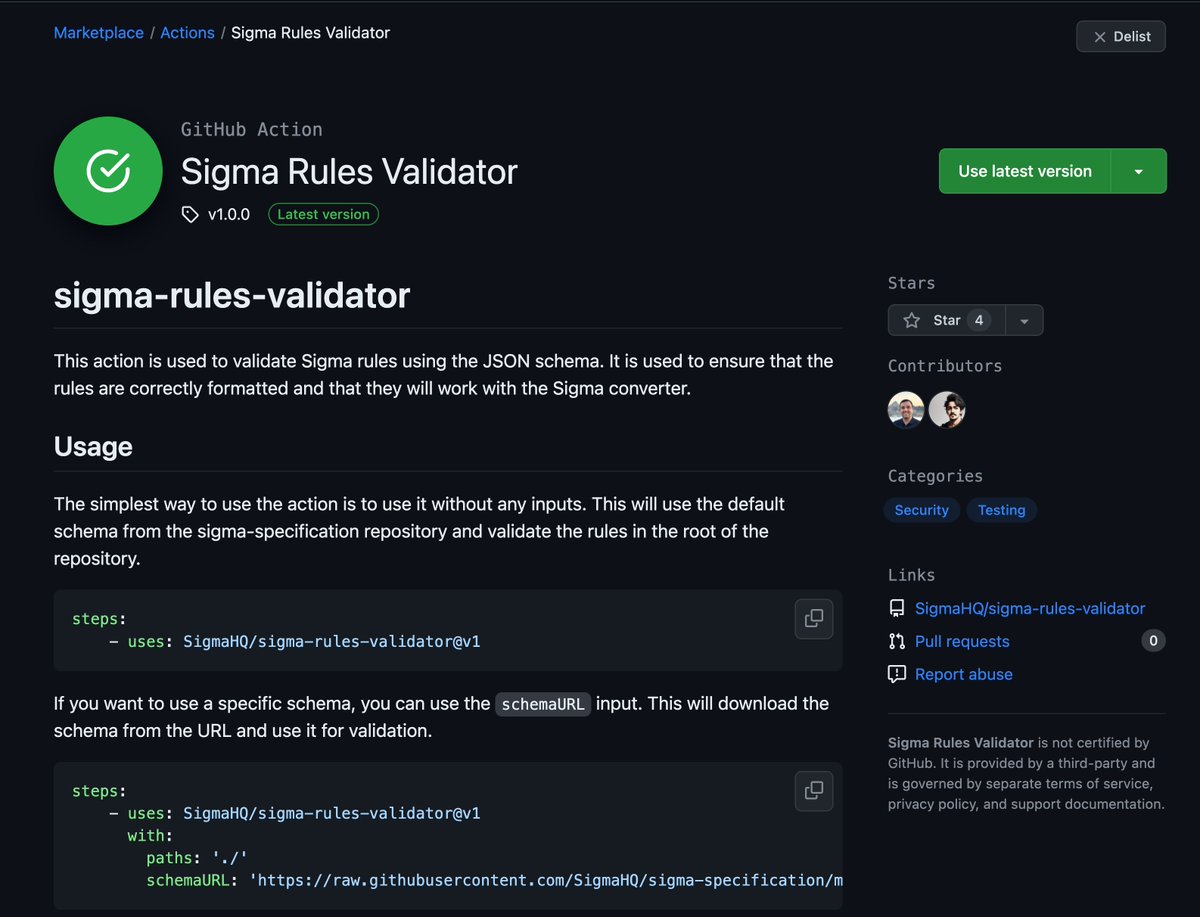
There is now a Sigma rule validator on the Github marketplace written by Mostafa Moradian
It helps you ensure that the rules you deploy to your repo can be converted using the official 'pySigma' converter
github.com/marketplace/ac…









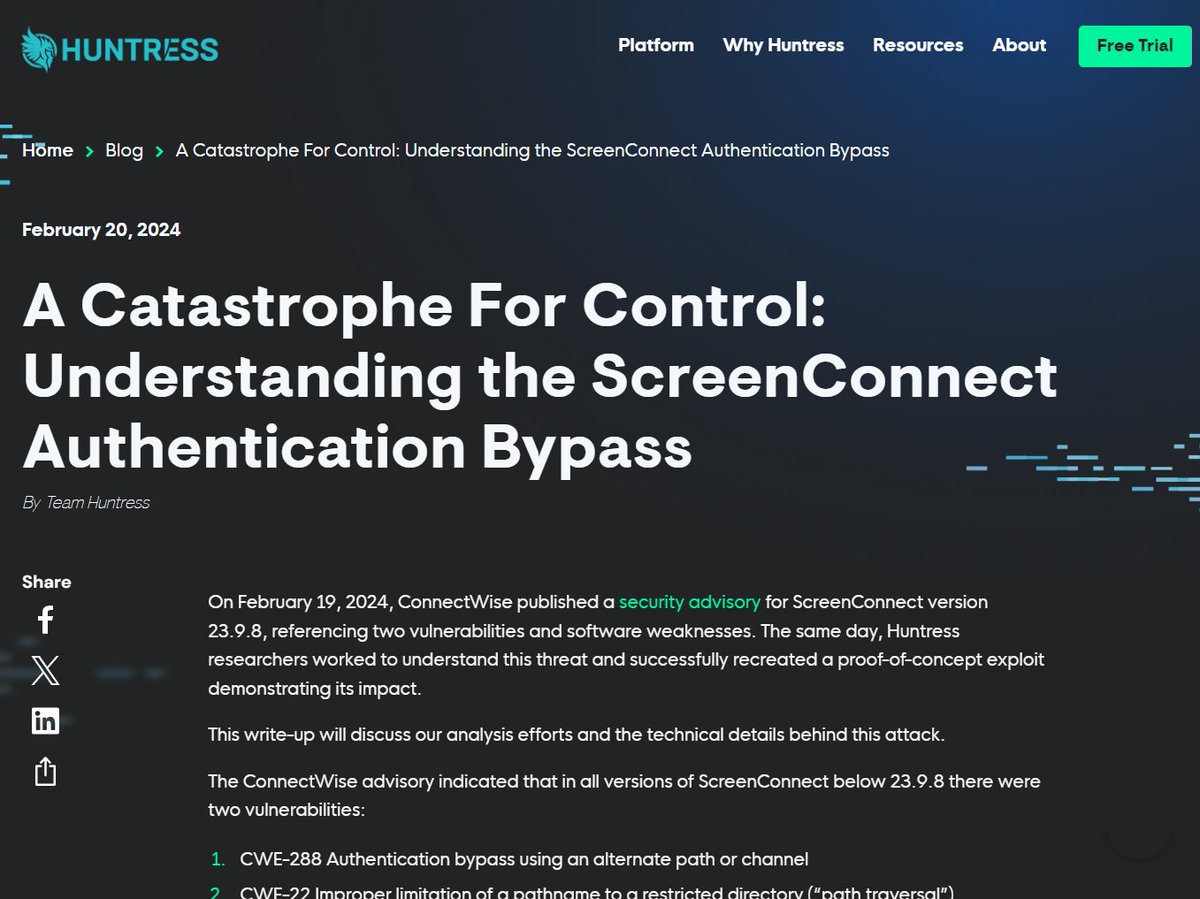
CVEs!!! 🤩
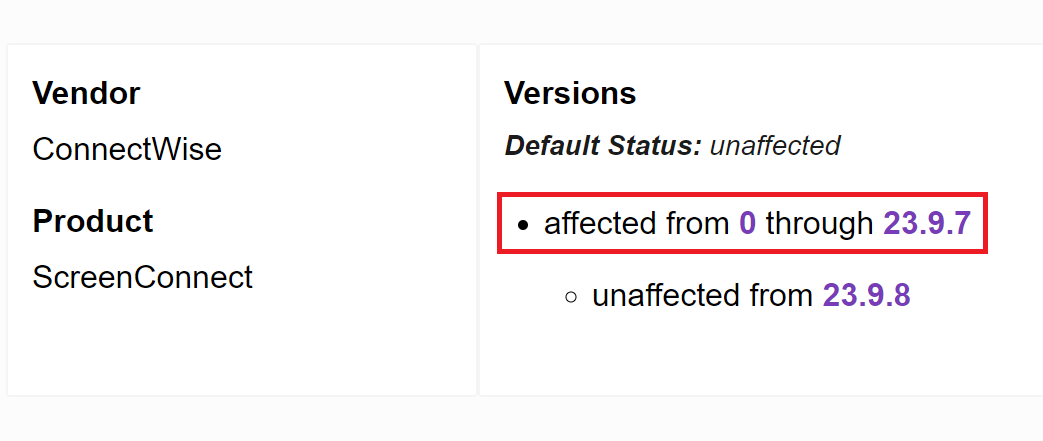
CVE-2024-1708 and CVE-2024-1709 assigned for the #ScreenConnect vulnerabilities.
.... and ah, the words 'affected from version 0' are pretty brutal 😅😅




New Fortinet RCE flaw in SSL VPN likely exploited in attacks - Lawrence Abrams
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…