Erol Rsync | Web3
@web3rsync
Securing smart contracts | Managing risks | Digital forensic | #Ethereum block builder | Ape🍌
ID: 234878409
06-01-2011 20:09:03
3,3K Tweet
153,153K Takipçi
469 Takip Edilen


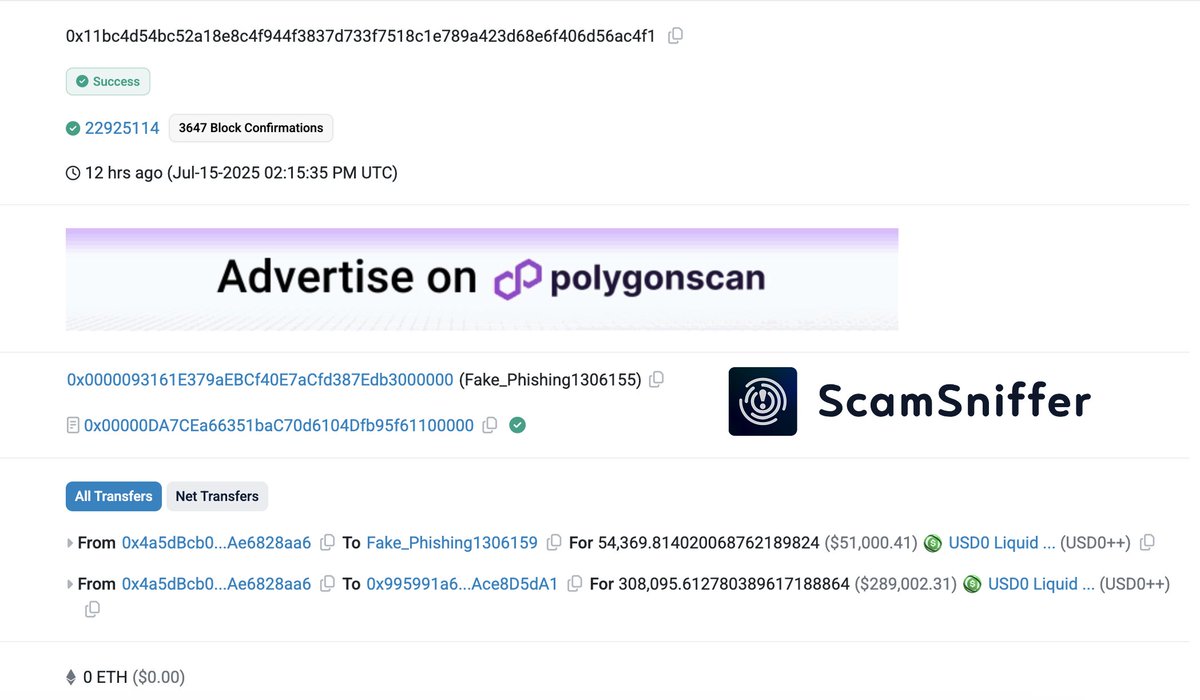
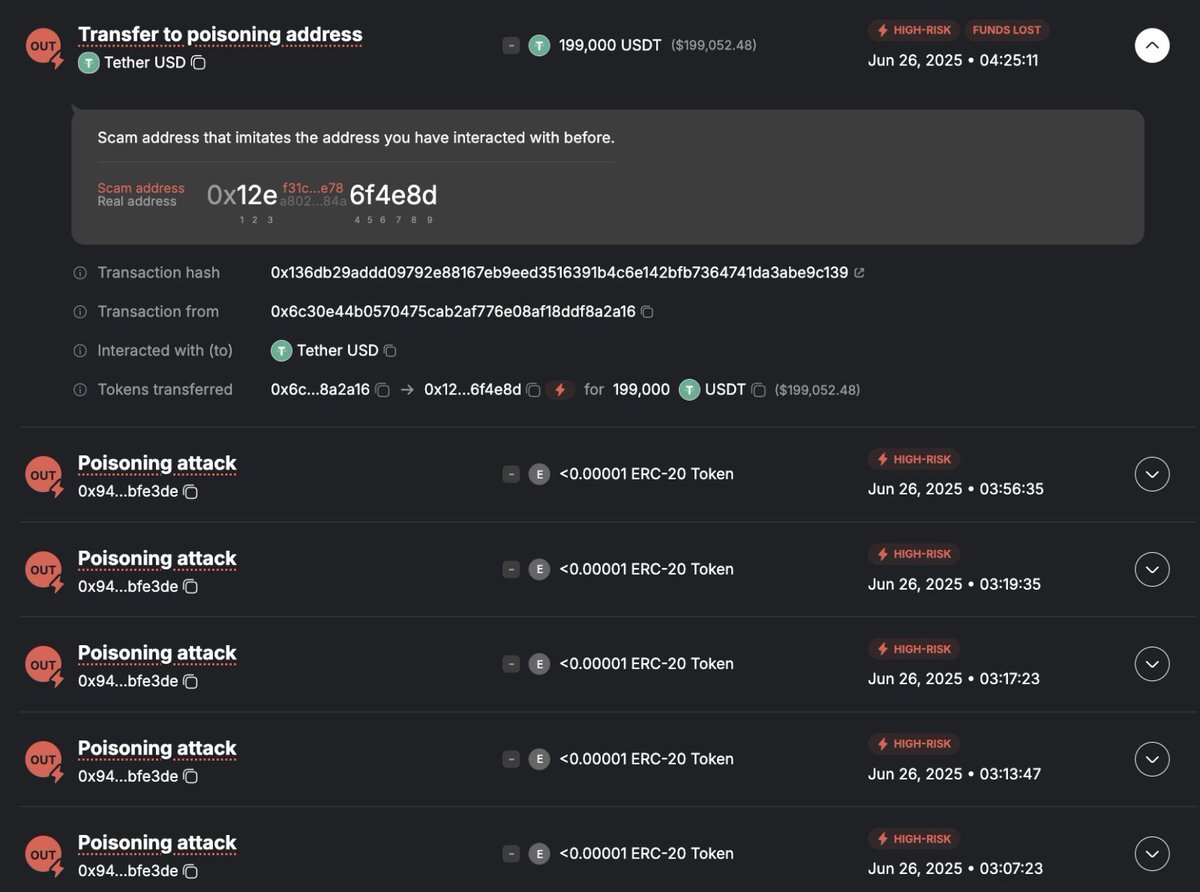
JUST IN: USER LOSES $199K USDT IN ADDRESS POISONING SCAM FUNDS SENT TO LOOKALIKE WALLET Source: Web3 Antivirus























![Scam Sniffer | Web3 Anti-Scam (@realscamsniffer) on Twitter photo 🧵 [1/4] 🚨 ScamSniffer H1 2025 Phishing Report
H1 2025: $39.33M lost across 43,628 victims
5 whale attacks >$1M accounted for $9.97M (25% of total losses), while monthly figures swung from $10.25M peak (Jan) to $2.80M low (Jun) 📊 🧵 [1/4] 🚨 ScamSniffer H1 2025 Phishing Report
H1 2025: $39.33M lost across 43,628 victims
5 whale attacks >$1M accounted for $9.97M (25% of total losses), while monthly figures swung from $10.25M peak (Jan) to $2.80M low (Jun) 📊](https://pbs.twimg.com/media/Gu2Itz2awAASLCf.jpg)