WBG
@wbgiil
ID: 831880573375221761
http://wbglil.github.io 15-02-2017 14:59:19
1,1K Tweet
586 Followers
2,2K Following











Introducing Stifle! A super simple .NET tool I spun up these past few days for abusing explicit strong certificate mappings leading to impersonation in Active Directory! Based off the research and powershell tools by Jonas Bülow Knudsen and SpecterOps last year. github.com/logangoins/Sti…


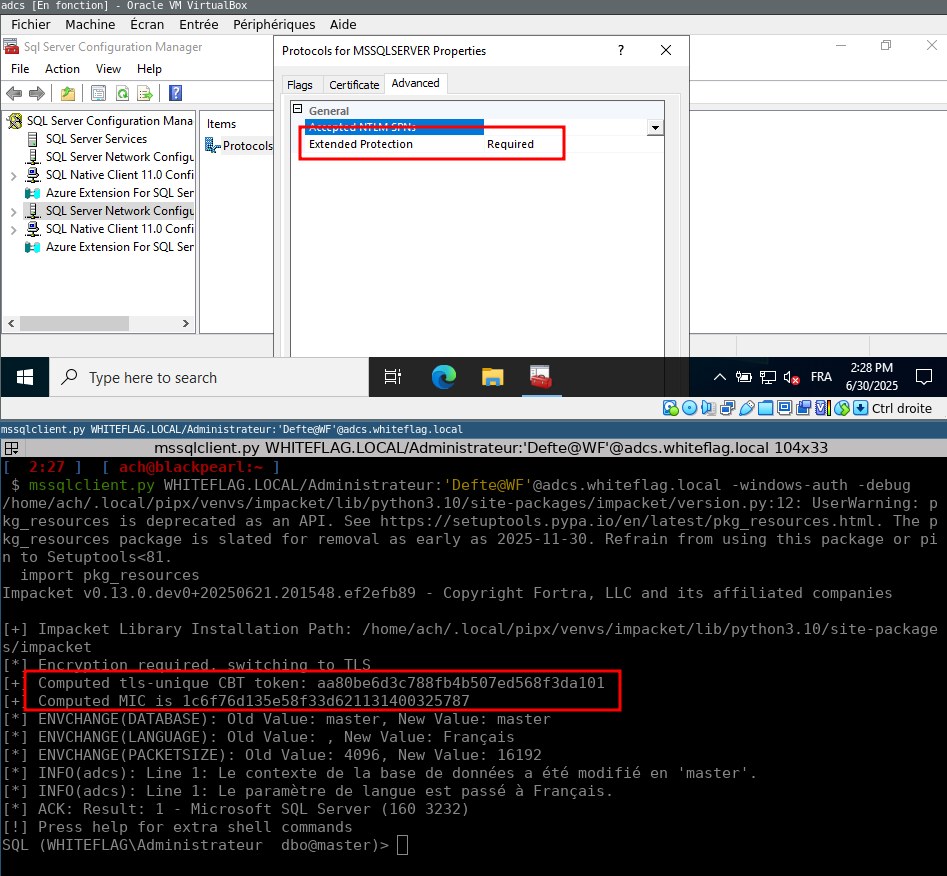
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (Aurélien Chalot), including instructions for reproducing the test environment yourself. (link below)

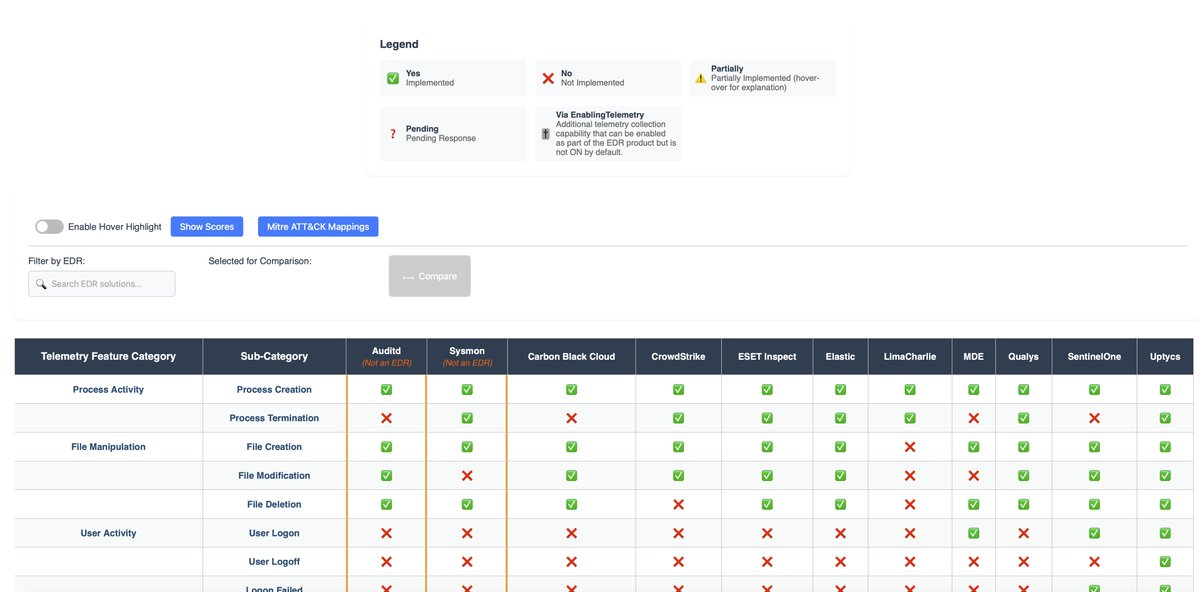
The 2025 CrowdStrike Threat Hunting Report was released today. The OverWatch team did an incredible job stopping an unprecedented number of threats in the last year, Cloud intrusions are up 136% with China based cloud intrusions up 40%! Get the report: crowdstrike.com/en-us/blog/cro…






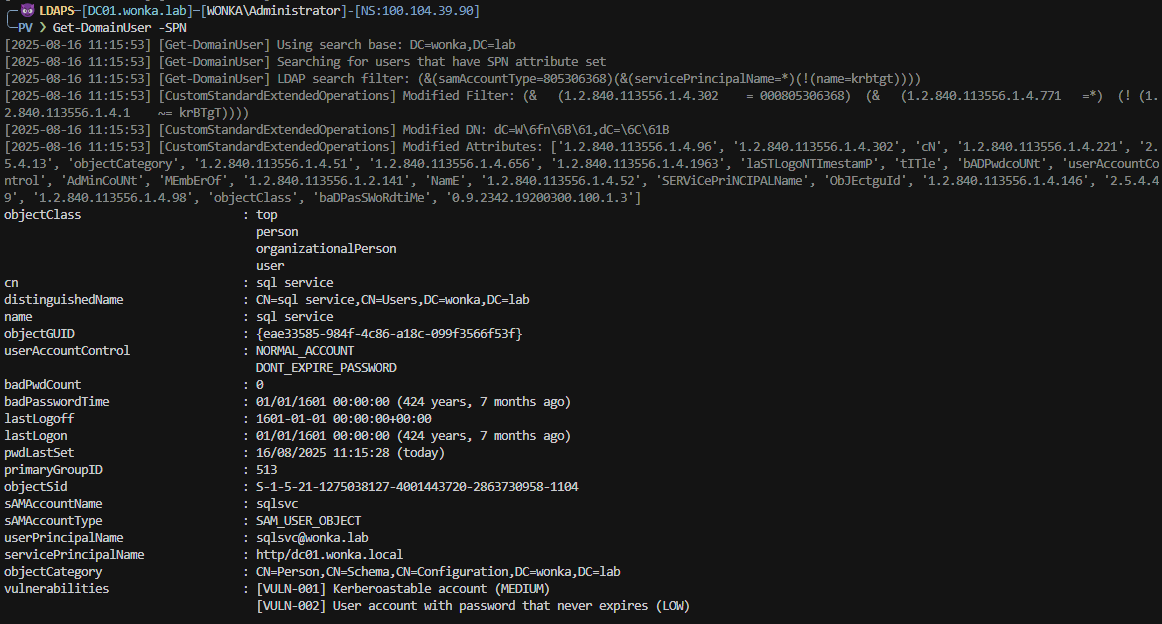
Powerview 2025.1.5: Added --obfuscate flag to obfuscate ldap filters and base DN. This is heavily inspired by github.com/Macmod/ldapx obfuscation logic by Artur Marzano Credits to the original research "MaLDAPtive" by Sabi and Daniel Bohannon
![hithere (@asdasd13asbz) on Twitter photo #Lazarus #APT
x.com/BaoshengbinCum…
Python Backdoor FTP Server : 67.203.7[.]245:21 #Lazarus #APT
x.com/BaoshengbinCum…
Python Backdoor FTP Server : 67.203.7[.]245:21](https://pbs.twimg.com/media/GNNELhZbkAAq5U2.png)