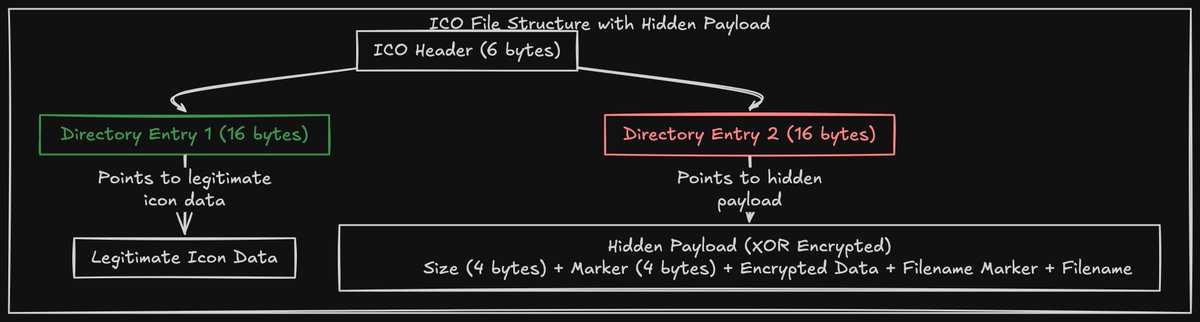
Vikas Anil Sharma
@vikzsharma
Strive for greatness | Building @agilehunt | Security Research & Bug Bounty
ID: 2191596000
https://agilehunt.com/ 13-11-2013 03:56:28
1,1K Tweet
1,1K Followers
1,1K Following




I've just released HTTP Request Smuggler 2.17 which fixes a nasty Client-Side Desync false-negative. Big thanks to Thomas Stacey for reporting it! Hope you all find some nice CSDs in 2025 :)
















I think many people are familiar with the topic of blind CSS exfiltration, especially after the post by Gareth Heyes \u2028 However, an important update has occurred since then, which I wrote below ->
![Vikas Anil Sharma (@vikzsharma) on Twitter photo When burp after 20-30k requests [Extensions Loaded] forces you to buy this ☠️ When burp after 20-30k requests [Extensions Loaded] forces you to buy this ☠️](https://pbs.twimg.com/media/GYarHI8bgAEkYJc.png)