
Umarex
@umarex01
Red Team Operator | Windows Security Researcher | Reverse Engineer | Keyboard Punching Expert
ID: 1830955596822003712
https://github.com/UmaRex01 03-09-2024 13:07:32
73 Tweet
75 Followers
675 Following



Building a custom Mimikatz binary by S3cur3Th1sSh1t s3cur3th1ssh1t.github.io/Building-a-cus…


I don't pay for premium, so please read the longform in the picture. TLDR: Cool new VS x86/x64 shellcode template from alex short 🇺🇦 at github.com/rbmm/SC_DEMO, he lives in Ukraine and is looking for remote work, help him make a connection if you can.






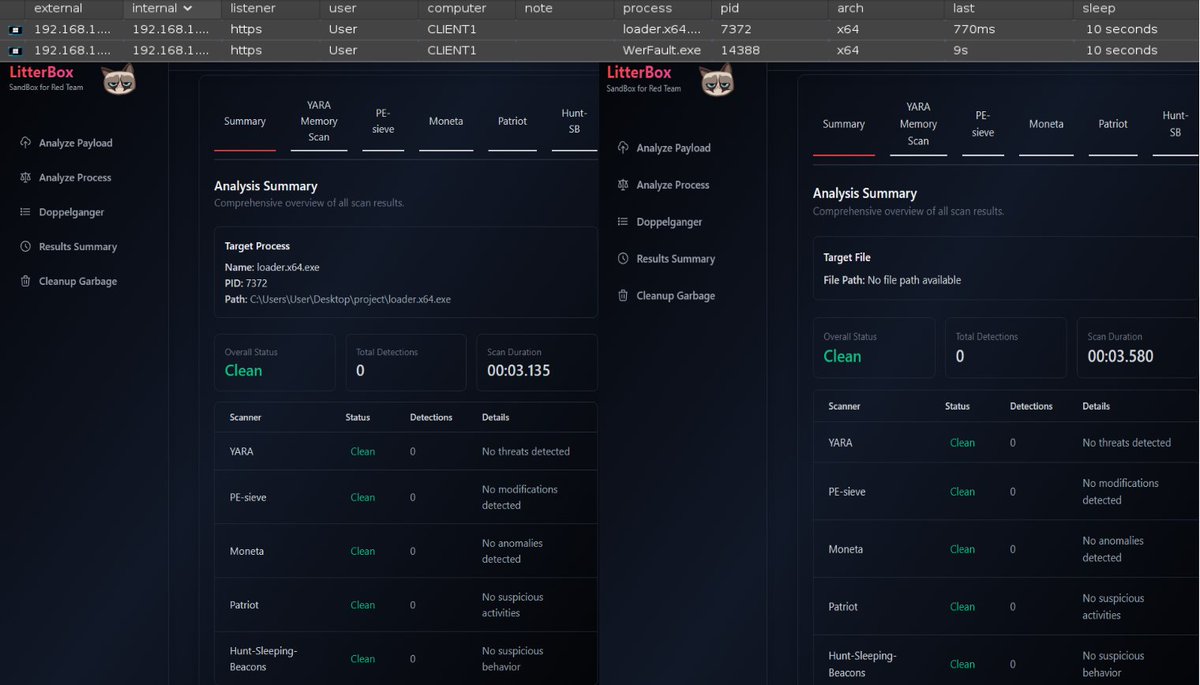
UDRL / Sleepmask combo is finally getting there. LitterBox(github.com/BlackSnufkin/L…) from BlackSnufkin makes it super convenient to test processes with multiple awesome dynamic analyzers. Kudos to to the authors of those tools as well, they pushed this project to another level.







With some guidance from DebugPrivilege I've found a way to easily dump clear text implants even while they sleep. Bad day for sleep obfuscation 💤 blog.felixm.pw/rude_awakening…







