Pumpkin 🎃
@u1f383
Security researcher at DEVCORE. Focus on Linux kernel.
ID: 2228169914
https://u1f383.github.io 03-12-2013 11:49:08
151 Tweet
1,1K Followers
275 Following














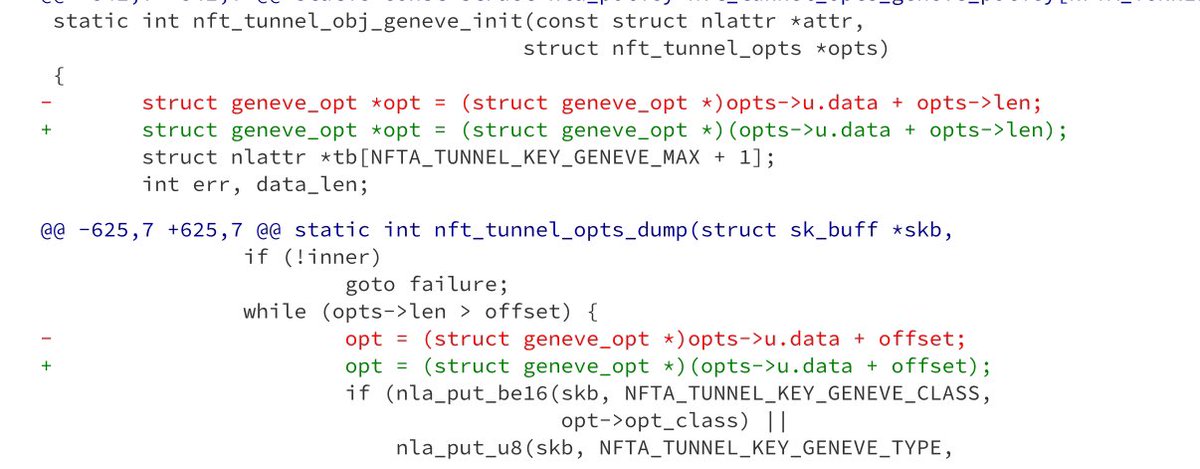
New blogpost! Want to see how we exploited Synology Inc. network-attached-storage devices at Pwn2Own Ireland? RCE to root via out-of-bounds NULL-byte writes, click the embed for a fun little writeup of CVE-2024-10442 🔎🎉 blog.ret2.io/2025/04/23/pwn…