yaala
@yaalaab
bug bounty hunter
ID: 3452705847
27-08-2015 01:35:03
209 Tweet
1,1K Takipçi
306 Takip Edilen









So I was researching iMessage exploits and found this: blog.zecops.com/research/the-r… This blog mentions an OOBW in CoreGraphics CGDataProviderDirectGetBytesAtPositionInternal, a different bug from CVE-2021-30860 that was an int overflow in JBIG2 PDF parsing. Any more details on this?




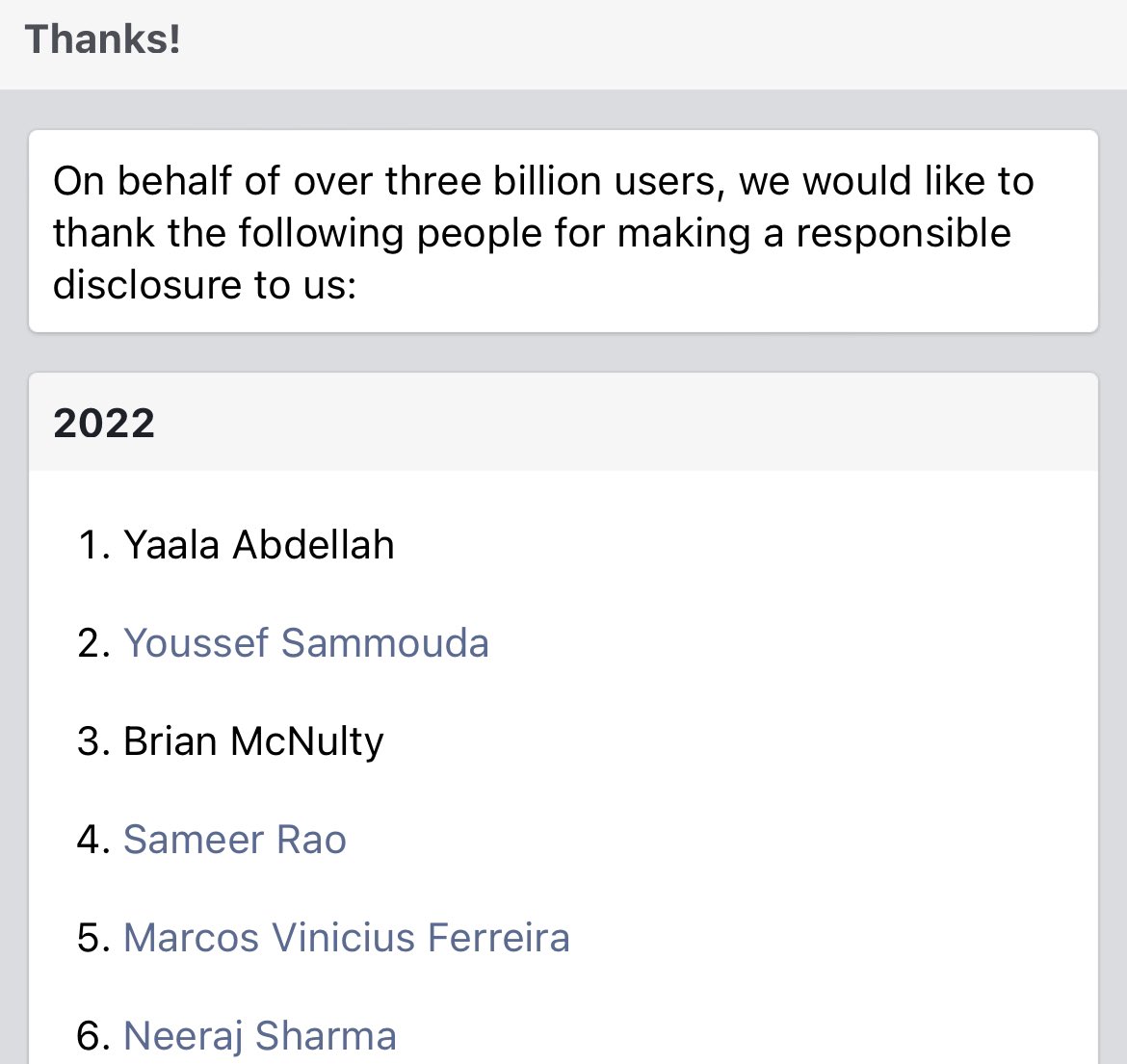
2022 is a good year for me and WC team moroccan 😁 Thanks Facebook Security m.facebook.com/whitehat/thanks





I recently developed and posted about a technique called "First sequence sync", expanding James Kettle's single packet attack. This technique allowed me to send 10,000 requests in 166ms, which breaks the packet size limitation of the single packet attack. flatt.tech/research/posts…

Detect the NextJS middleware bypass directly in Burp Suite with this BCheck from eternalkyu gist.github.com/fourcube/45a78…